Network attack filtering method and device
A network attack and filtering device technology, applied in the field of network security, can solve problems such as untimely detection, increased difficulty in maintenance, and impact of speed limit on normal access users, and achieve remarkable results.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
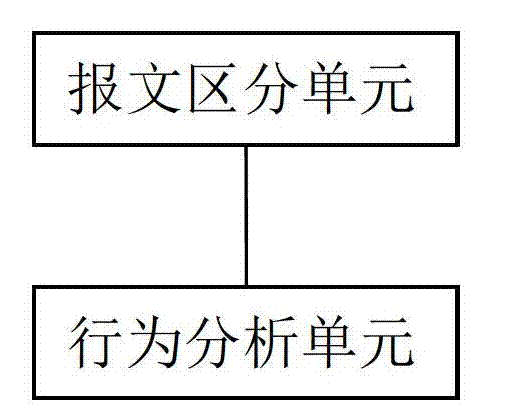
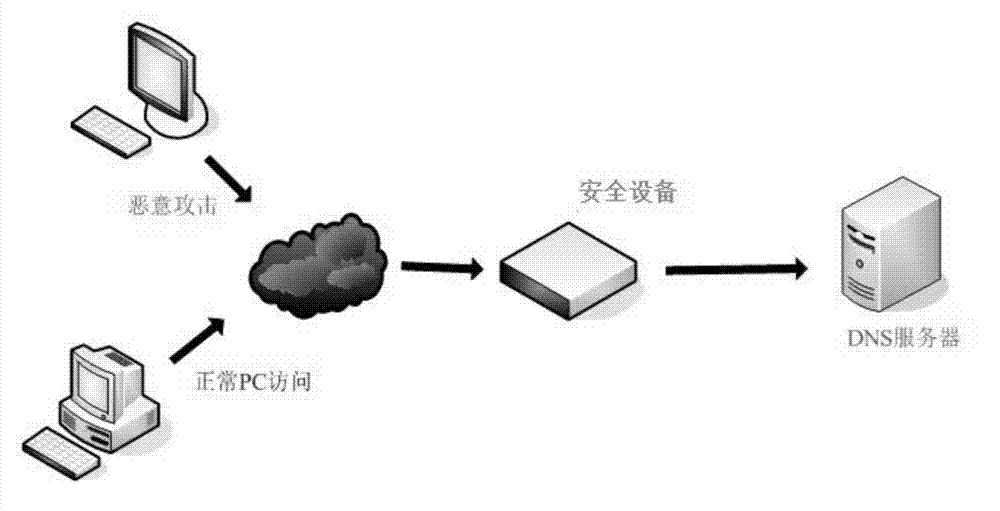
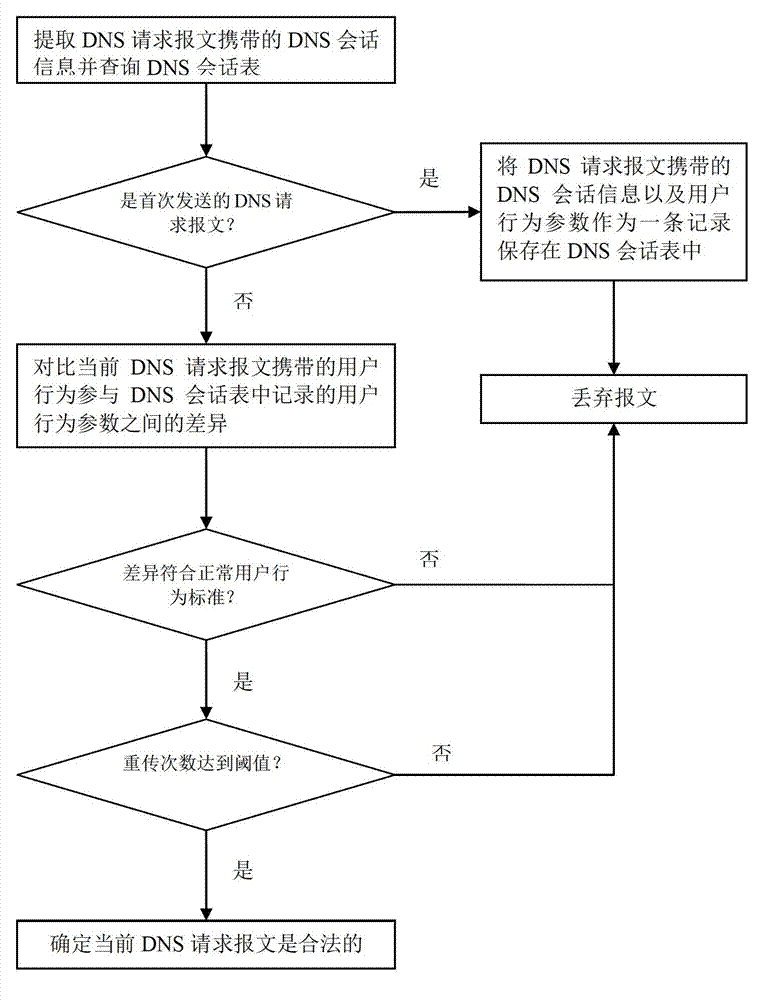
[0019] The present invention provides an accurate network attack filtering method and device for the DNS server, and its design principle is no longer rough protection from the number of packets and rate as in the prior art, but from the user's normal access to the DNS server. Beginning with behavioral characteristics, identify normal user access and malicious attacks. Please refer to figure 1 , Taking computer program implementation as an example (the present invention does not exclude other implementations), a network attack filtering device of the present invention is applied to a security device to provide a network attack filtering service for a DNS server, and the device includes: a message distinguishing unit and Behavior Analysis Unit. The security device can adopt a popular hardware architecture, which mainly includes CPU, memory, storage, and various business hardware (not required) including business cards. In a basic implementation, please refer to figure 2 as ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com