Authentication method for preventing replay attack
An authentication method and anti-replay technology, applied in the direction of electrical components, transmission systems, etc., can solve the problems of communication protocol or system complexity, increase system instability, etc., and achieve the effect of ensuring accuracy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
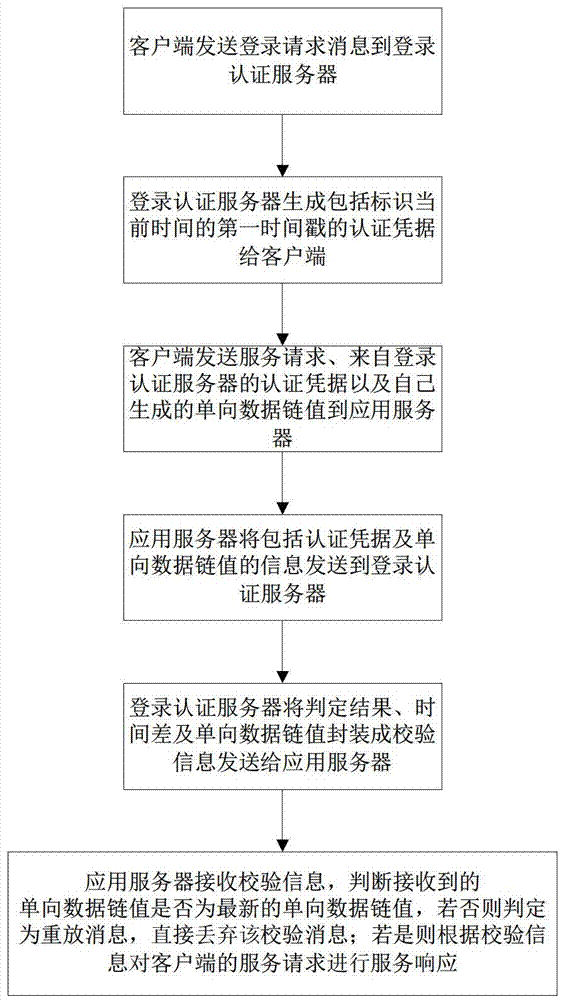
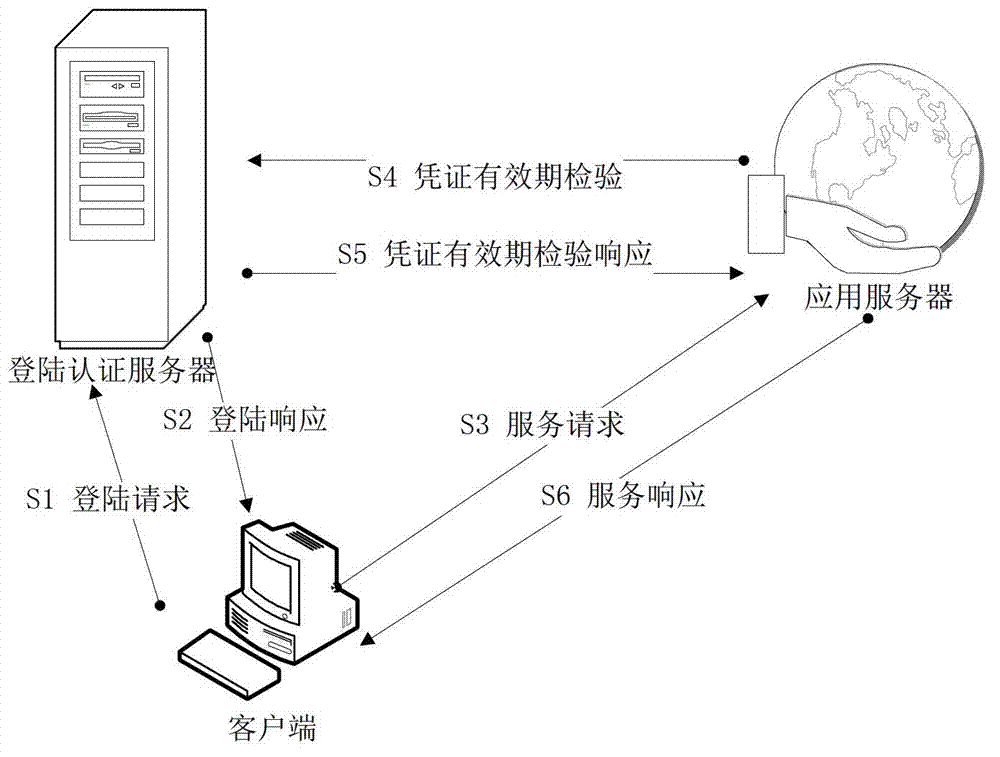
[0025] refer to figure 1 , an authentication method against replay attacks, comprising the following steps:
[0026] The client sends a login request message to the login authentication server;
[0027] The login authentication server generates the first timestamp Time that includes identifying the current time SignOn authentication credentials to the client;
[0028] The client sends the service request, the authentication credentials from the login authentication server and the one-way data link value generated by itself to the application server;
[0029] The application server sends information including authentication credentials and one-way data link values to the login authentication server;
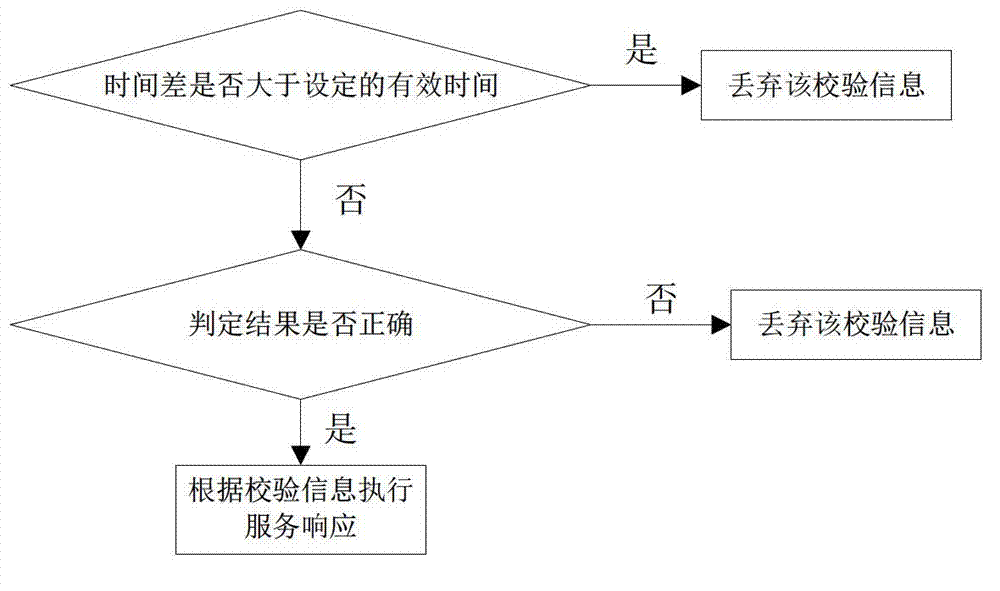
[0030] Log in to the authentication server to determine the correctness of the authentication credentials and calculate the current time Time Current with the first timestamp Time SignOn The time difference of the authentication credential used to prove whether the user has...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com