Terminal-based network access control system
A network access control and access control list technology, which is applied in the field of computer communication, can solve problems such as high hardware requirements, inability to isolate, limit network access, etc., and achieve the effect of simple configuration and maintenance and protection of security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
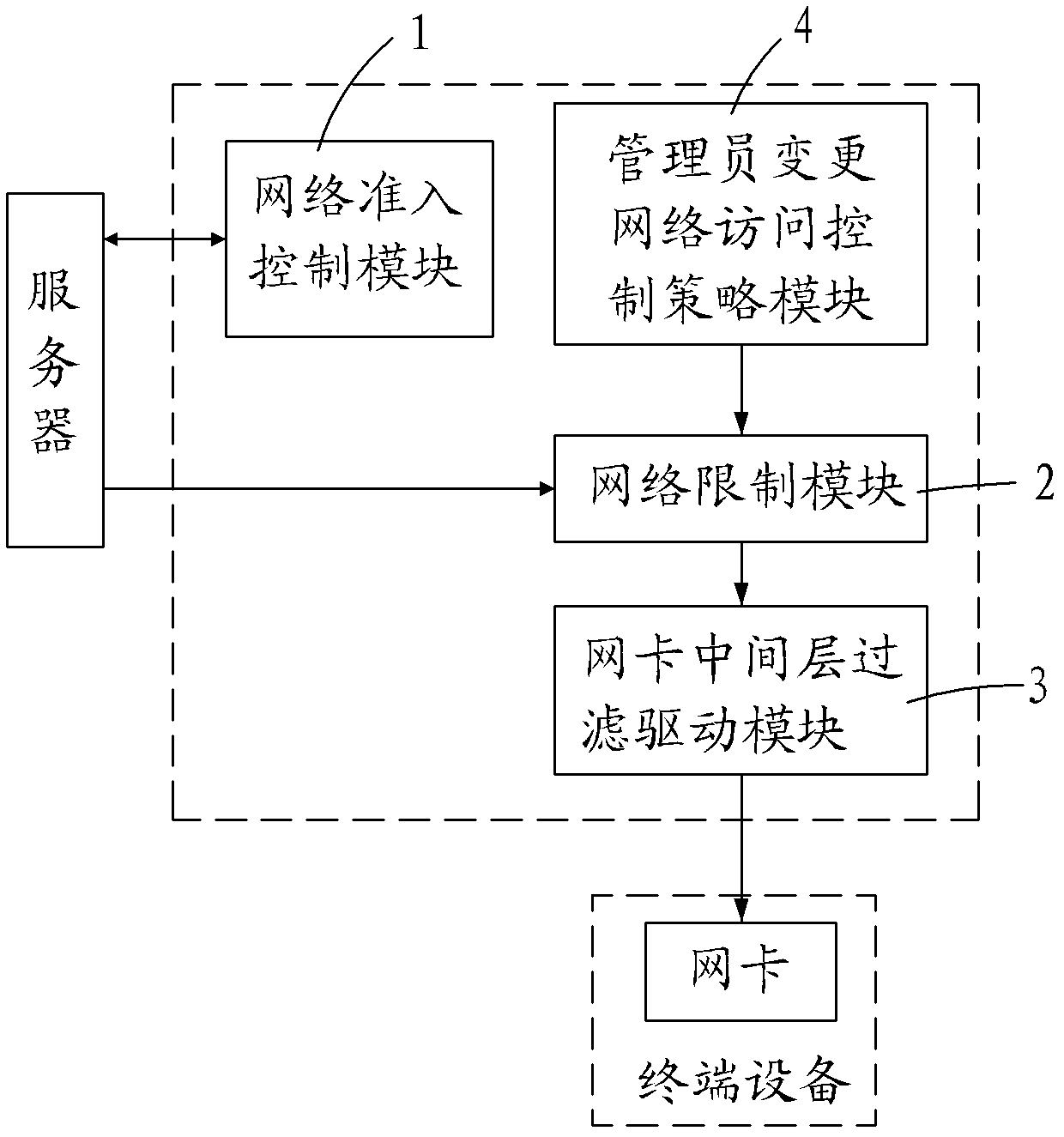
[0018] see figure 1 As shown, a terminal-based network access control system of the present invention includes a network access control module 1, a network restriction module 2, and a network card middle layer filter driver module 3;
[0019] The network access control module 1 performs network authentication according to the identity of the user to determine whether to allow the terminal device used by the user to connect to the network;
[0020] The network restriction module 2 is responsible for analyzing the network access control strategy issued by the server, and converting it into an access control list (i.e. the ACL table) that can be processed by the network card middle layer filter driver module 3, the access control list Including the IP address / IP address range field, the local port range field, the remote port range field, the protocol type field used by the internet, the traffic direction field and the authority field of the network data frame in the terminal dev...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com