Method and device for monitoring terminal command line in real time
A terminal command and real-time monitoring technology, which is applied in digital transmission systems, electrical components, transmission systems, etc., can solve the problems of being unable to accurately locate the person responsible for operating commands, man-made tampering of files, and inability to perform centralized management and real-time monitoring, etc., to achieve less occupation , extensive compatibility, and the effect of less system resources
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0040] The specific implementation manners of the present invention will be described in further detail below with reference to the accompanying drawings.
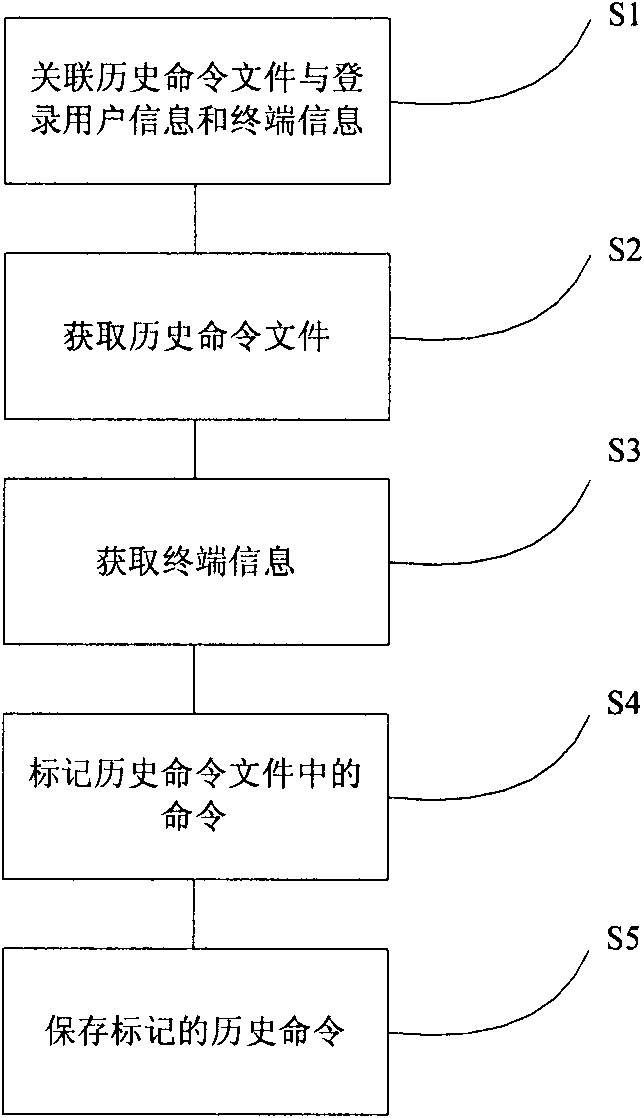
[0041] Embodiments of the present invention associate historical command file names with terminal information and user information, and utilize various log files provided by the Unix / Linux operating system to collect user operation commands and various other behaviors, and send these information to Event collection server for monitoring, management and auditing. These log files can include user information (utmp) successfully logged in the current system provided by the Unix / Linux operating system by default, user su records in the system (sulog), failed login information in the system (filedlogin), and user operations in the system Command (history), operation command (ftp log) after ftp login in the system, and other user-defined application logs.
[0042] Such as figure 1 As shown, the device for real-time monitoring ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com