Methods for passing through and assisting in passing through network isolation equipment in Internet protocol (IP) monitoring system, and node
A technology for monitoring nodes and network isolation, which is applied in transmission systems, electrical components, etc., and can solve problems such as hidden dangers in enterprise intranet security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
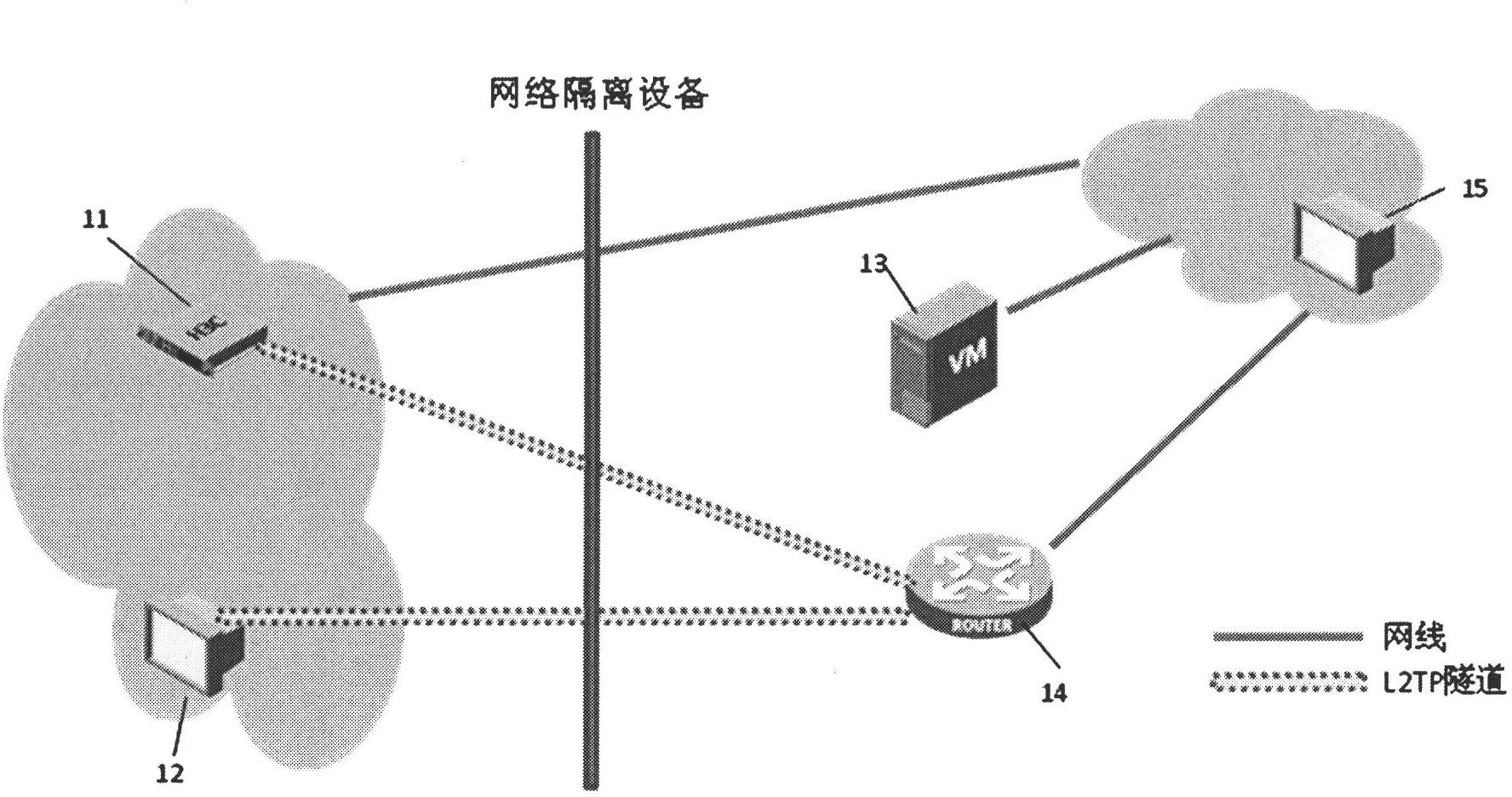
[0034] figure 1 A schematic network diagram of Embodiment 1 is shown. The network is an IP surveillance system. The IP monitoring system includes multiple monitoring nodes. figure 1 , the monitoring node EC11 is isolated from another network by a network isolation device. The network isolation device can be NAT, firewall or gatekeeper. In this example, if figure 1 , the network where the monitoring node EC11 in the monitoring system is located is the network inside the network isolation device, which is called network A here, which is isolated or protected by the network isolation device, and the network outside the network isolation device is called network B here. Due to the existence of the network isolation device, network A can access network B, but network B cannot access network A without special configuration. The IP surveillance system also includes an L2TP relay 14 . The IP address of the monitoring node EC11 itself is 10.10.10.10, that is, the IP address belon...
Embodiment 2
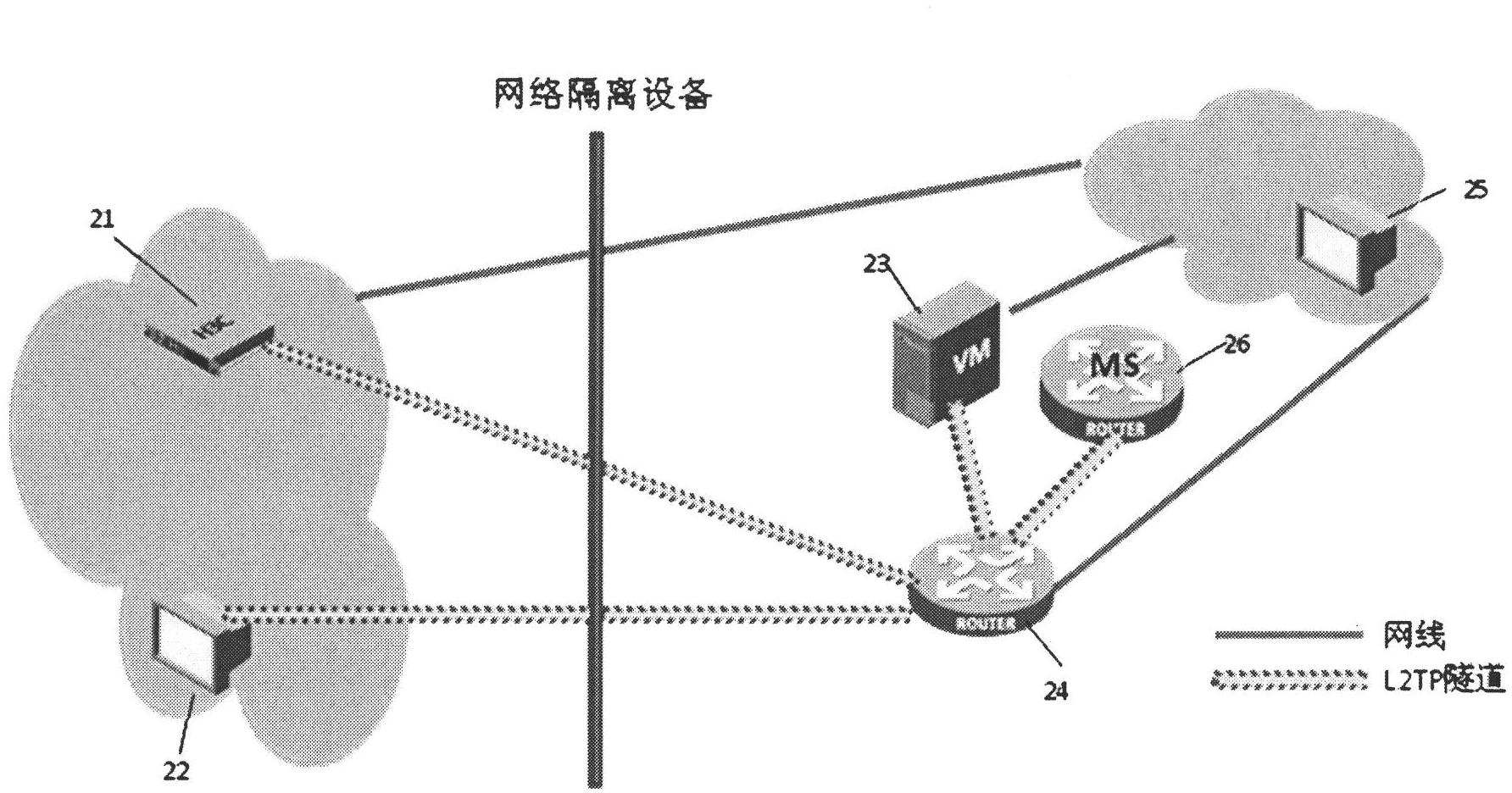
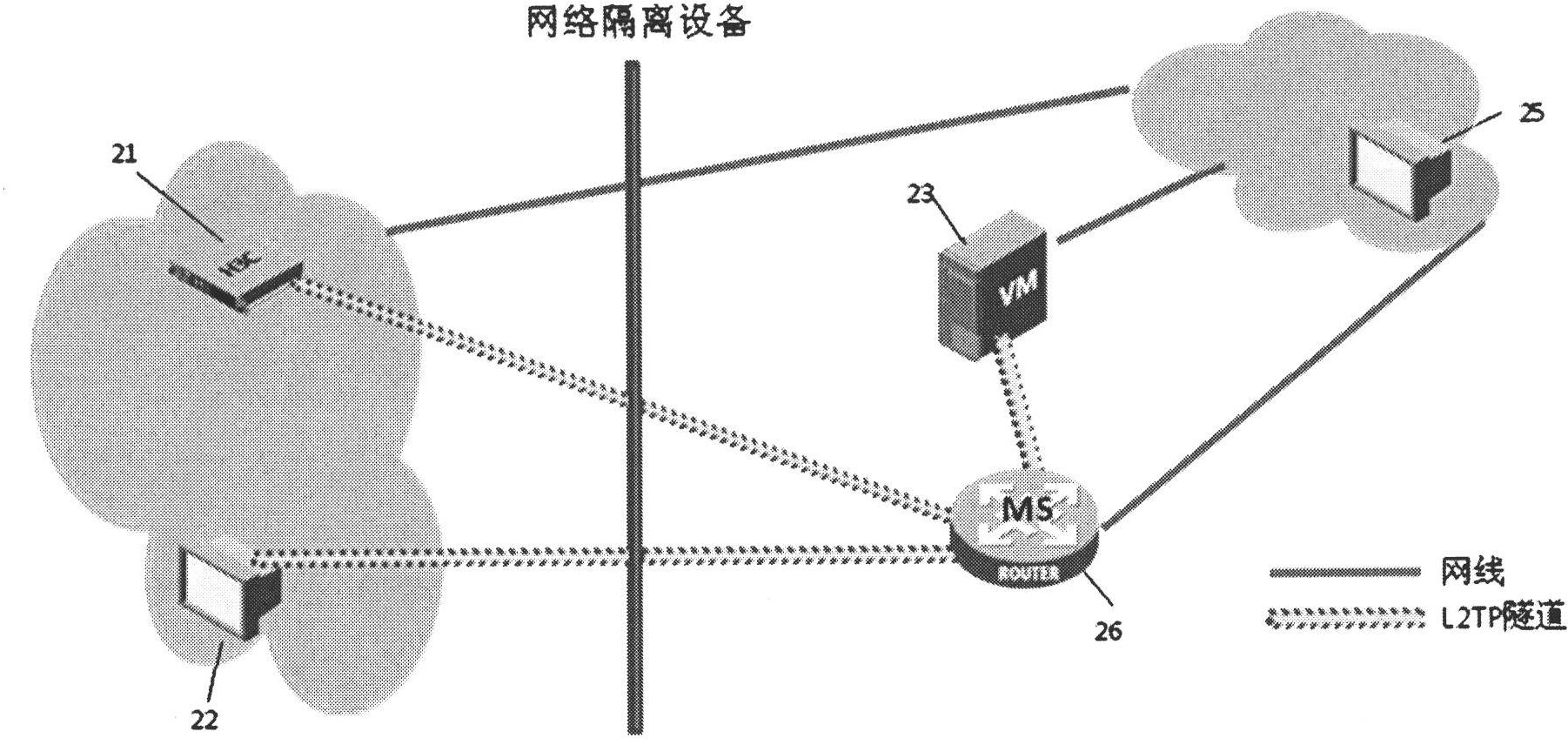
[0042] figure 2 A schematic diagram of the network of the second embodiment is shown. figure 2 network diagram and figure 1 The difference is that the L2TP relay 24 in network B initiates a tunnel connection request to VM23 to establish an L2TP tunnel connection with VM23; network B also includes an MS26, and the L2TP relay 24 also initiates a tunnel connection request to MS26 to establish an L2TP tunnel connection with MS26. The L2TP relay 24 also initiates a tunnel connection request to the monitoring node EC21 in the network A to establish an L2TP tunnel connection with EC21. The IP address allocated by EC21, VM23, and MS26 to L2TP relay 24 can be an IP address in an independent address pool, that is, the IP address in the address pool can plan an IP address segment separately, and does not need to occupy the IP address planned by network B, for example EC21 allocates addresses in 14.14.14.0 / 24, VM23 allocates addresses in 15.15.10.0 / 24, MS26 allocates addresses in 16.1...
Embodiment 3
[0049] image 3 A schematic diagram of the network of Embodiment 3 is shown. exist image 3 Among them, the IP monitoring system includes a monitoring node VM31, and the monitoring node VM31 is isolated from another network by a network isolation device. The network isolation device can be NAT, firewall or gatekeeper. The network where the monitoring node EC11 in the monitoring system is located is the network inside the network isolation device, called network A, which is isolated or protected by the network isolation device; the network outside the network isolation device is called network B. Due to the existence of the network isolation device, network A can access network B, but network B cannot access network A without special configuration. The IP monitoring system also includes an L2TP relay device 33 . The IP address of the monitoring node VM31 itself, that is, the IP address belonging to the network A is 10.10.10.10. The IP address of the L2TP relay device 33 itse...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com