Network-oriented penetration testing scheme automatic-generation method
A penetration testing and automatic generation technology, applied in the field of network information security, can solve the problems of too many irrelevant nodes and no abstract model of penetration testing scheme, so as to reduce the search effect.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0037] The present invention will be further described below in conjunction with the accompanying drawings and embodiments.
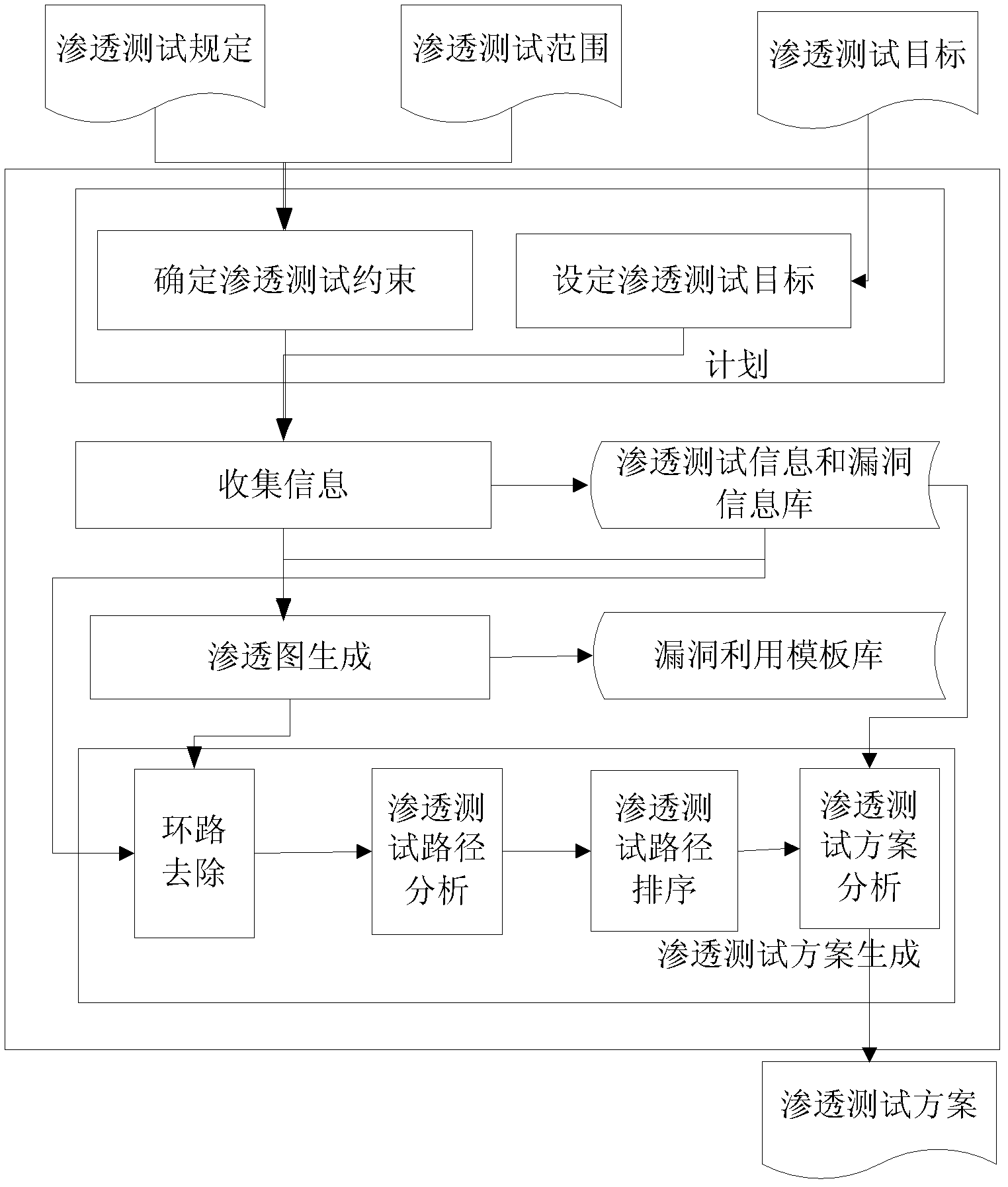
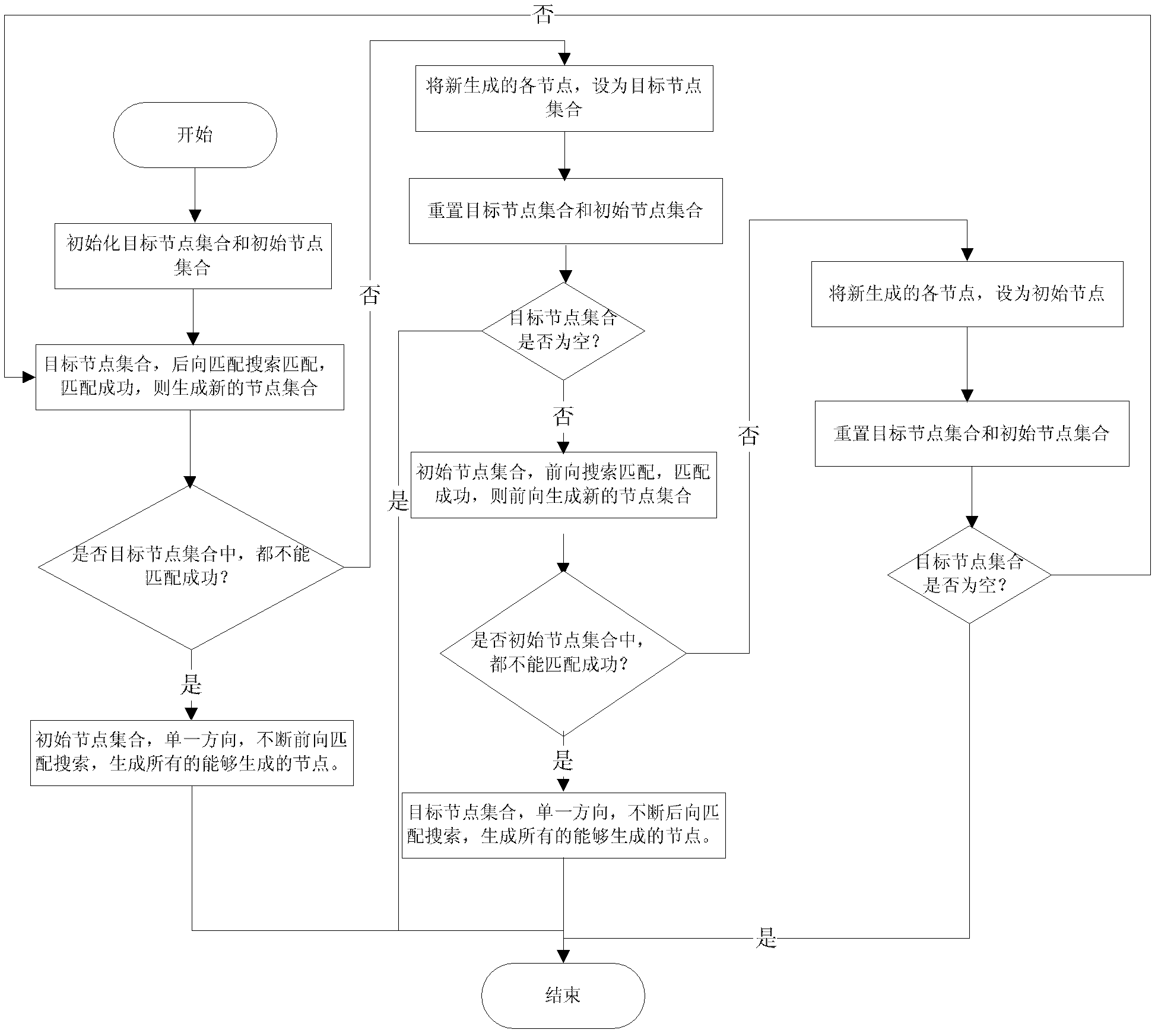
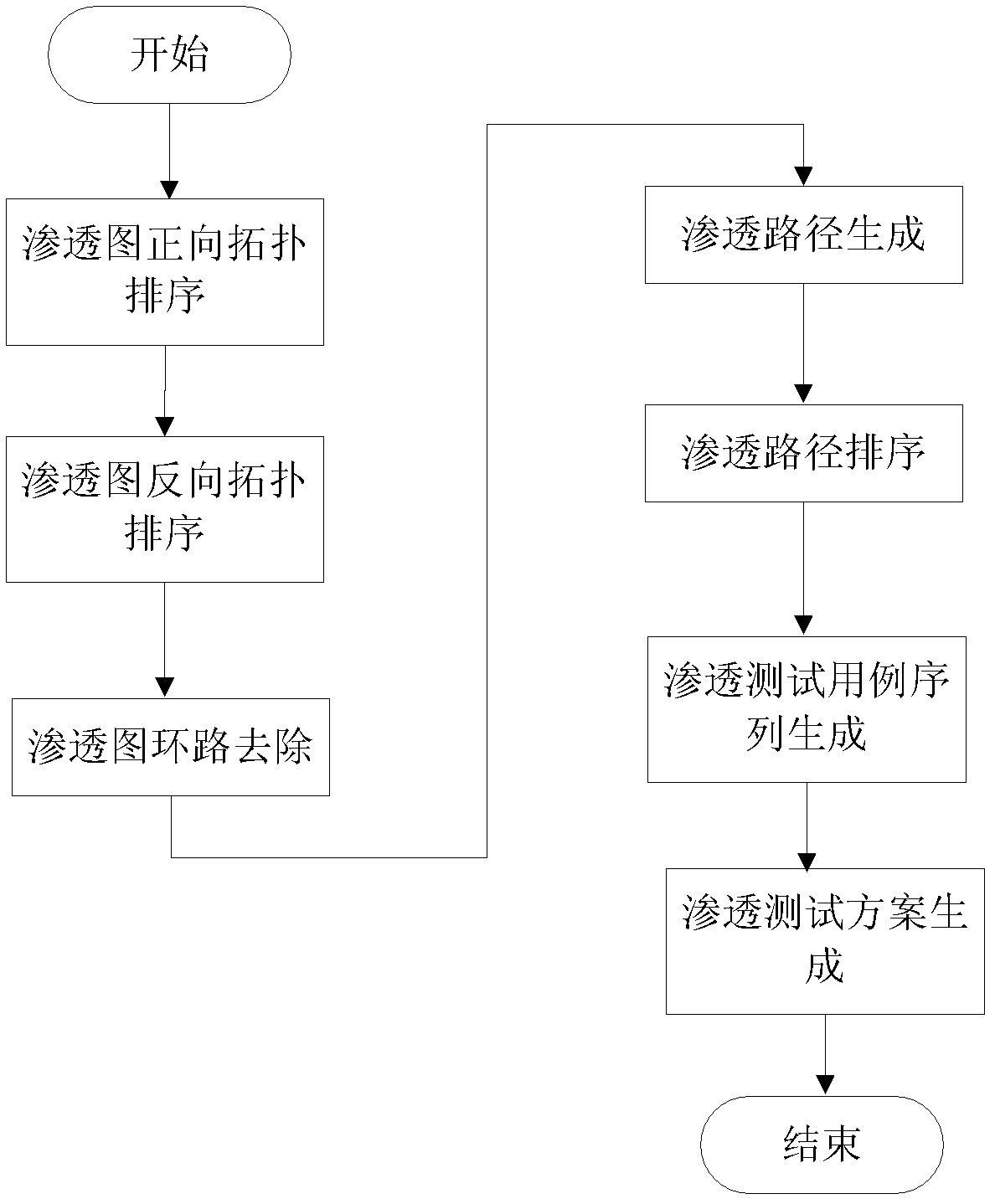
[0038] 1. If figure 1As shown, the present invention provides a method for automatically generating a network-oriented penetration testing scheme, which includes four processing flows: "planning", "information collection", "penetration map generation", and "penetration testing scheme generation". Among them, the "planning" processing flow is to give the penetration testing information about the penetration testing. The "information collection" processing flow is to collect vulnerability information on the network according to the set penetration test information, where the penetration test information includes penetration test constraints and penetration test objectives; connection relationship. The processing flow of "penetration graph generation" is to generate a penetration graph from the initial condition node of the penetration test to the target...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com