Record replay attack detection method and system based on channel mode noise
A technology for replaying attack and pattern noise, which is applied in digital data information retrieval, speech analysis, speech recognition, etc. It can solve the problems of difficulty in determining the limit of replay attack, large storage space, and large calculation amount, and save storage space and calculation The effect of resource and feature dimension reduction and efficiency improvement
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
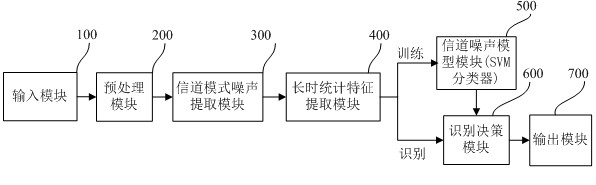
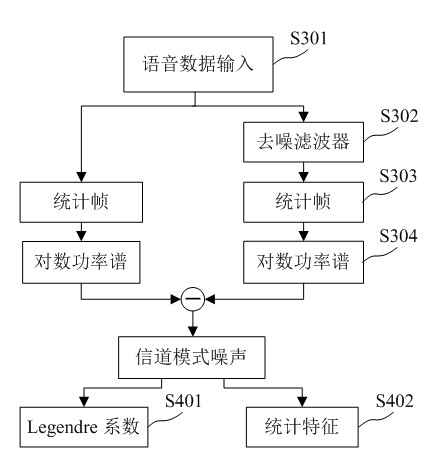
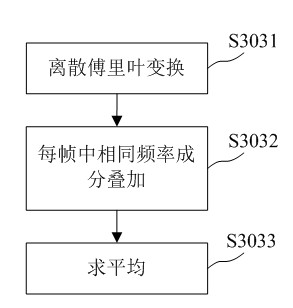
[0046] The implementation of the present invention will be further described below in conjunction with the drawings and embodiments, but the implementation of the present invention is not limited thereto.
[0047] The recording and playback attack detection method of the present invention can be realized in the embedded system according to the following steps:
[0048] Step (1), input training speech, which includes original speech signal and playback speech signal.
[0049] Step (2), preprocessing the input speech signal, including pre-emphasizing, framing and windowing the speech signal. Pre-emphasis is to perform high-pass filtering on the speech signal, and the transfer function of the filter is H(z)=1-az -1 , where a=0.975. For the framing of the voice signal, the frame length is 512 points, and the frame shift is 256 points. The window added to the speech signal is a Hamming window, where the function of the Hamming window is:
[0050] ω ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com