Restructurable Internet of things node intrusion detection method
A technology of intrusion detection and Internet of Things, applied in the direction of data exchange network, digital transmission system, electrical components, etc., can solve the problem of no consideration of the security of perception data collection, calculation and transmission, high false alarm rate, weak real-time performance, etc. problem, to achieve the effect of improving flexibility and real-time performance and reducing energy consumption
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
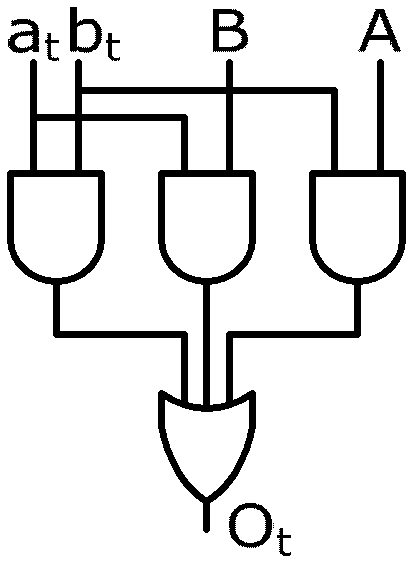
[0029] The present invention establishes a reconfigurable Internet of Things intrusion detection method, wherein gate level information flow tracking technology (gate level information flow tracking, GLIFT) is used to establish reconfigurable security "hot spot" tracking. The basic principles are as follows:
[0030] Let the original logic be f = f n ( A 1 , A 2 , . . . , A n , A 1 ‾ , A 2 ‾ , . . . A n ‾ ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com