Method for realizing strengthening of demilitarized zone (DMZ) of network
An isolated area and network technology, applied in the field of network communication data security, can solve the problem that NAPT performance cannot satisfy users, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
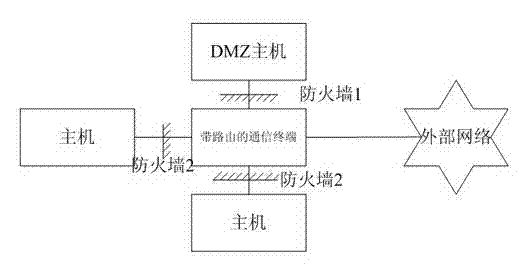
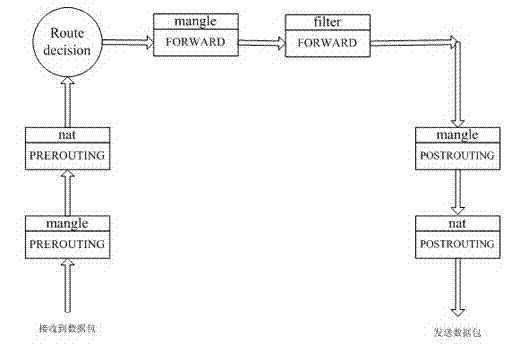
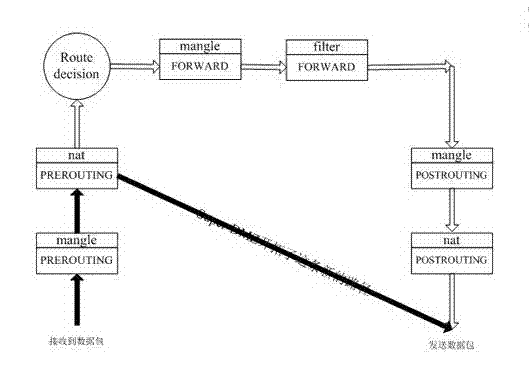
[0035] Example 1, such as image 3 As shown, the present embodiment is the flowchart of the uplink data packet and the downlink data packet of the DMZ host, because the IP address of the DMZ host is set to the IP address of the WAN side with the communication terminal with routing function, the DMZ host sends The uplink data of the DMZ is directly sent to the WAN, and the data packet reception (downlink data packet) and transmission (uplink data packet) of the entire DMZ include the following steps:
[0036] The following steps are included when receiving downlink data packets:
[0037] Step A, after the downlink data packet enters the communication terminal, compare the destination MAC address of the downlink data packet, if the destination MAC address is the same as the MAC address of the WAN interface of the communication terminal, receive the data packet;
[0038] Step B, if the receiving terminal of this data packet is the port of the open service on the DMZ host, then c...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com