Method and system for modeling Web in weblog excavation
A log and network technology, applied in the field of Web user modeling, can solve problems such as performance degradation, and achieve the effects of increased accuracy, good convergence effect, and improved effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0052] Embodiment 1. A Web modeling method in network log mining
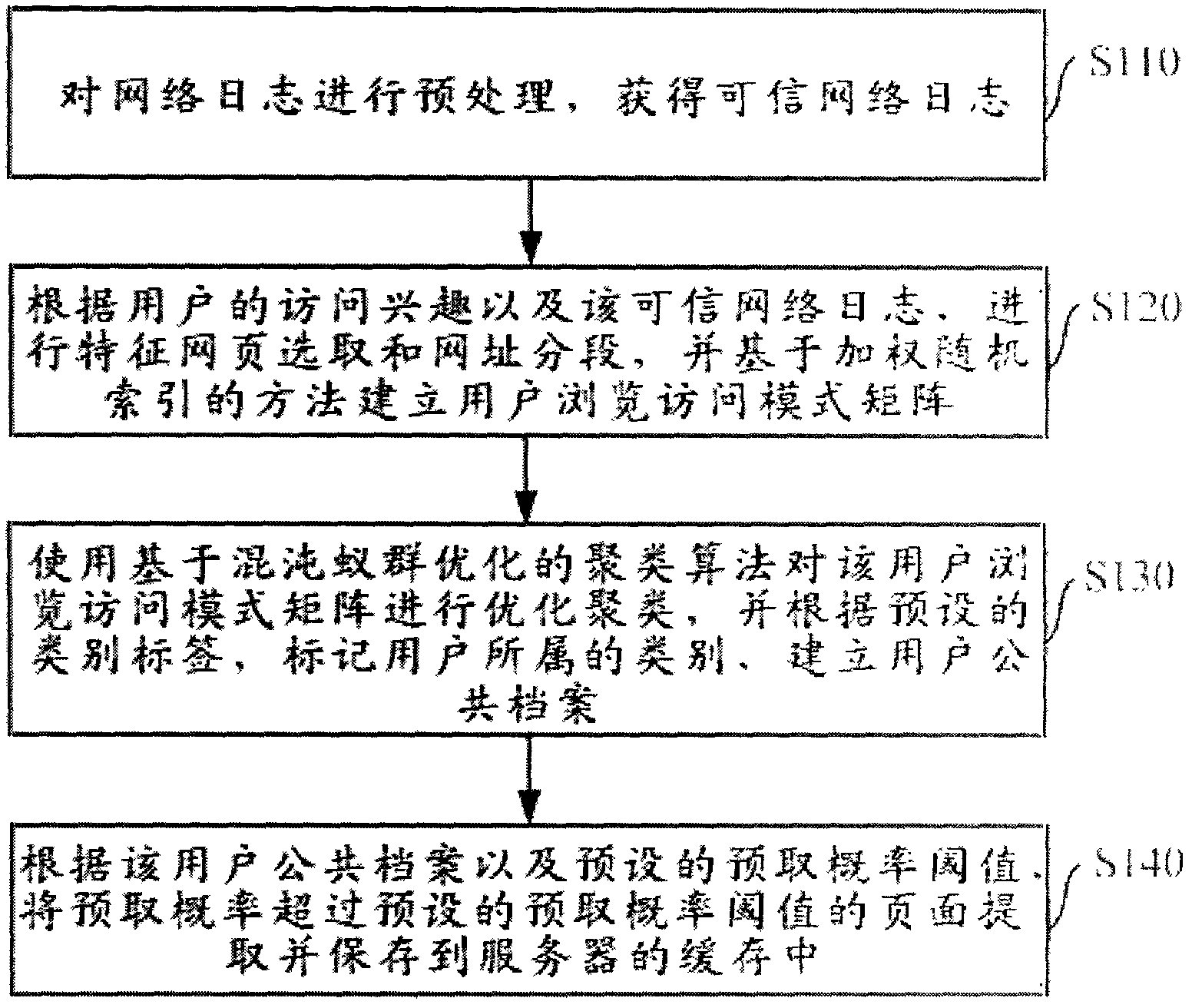
[0053] Such as figure 1 As shown, this embodiment mainly includes the following steps:
[0054] Step S110, preprocessing the network log to obtain a credible network log; the preprocessing mainly includes data cleaning, user identification and session identification; the data cleaning includes filtering pictures in web pages, filtering dynamic web pages and click rate lower than preset The webpage that sets the click threshold.
[0055] In this embodiment, the preset click-through rate threshold for a web page is 2, and a web page with a click-through rate lower than the click-through rate threshold generally reflects the user's transient action, but cannot represent the user's attention and browsing interest.
[0056] Step S120, according to the user's access interest and the trusted web log, select the characteristic web page and segment the URL, and establish a user browsing access pattern matrix based on ...
Embodiment 2
[0078] Embodiment 2, a Web modeling system in network log mining
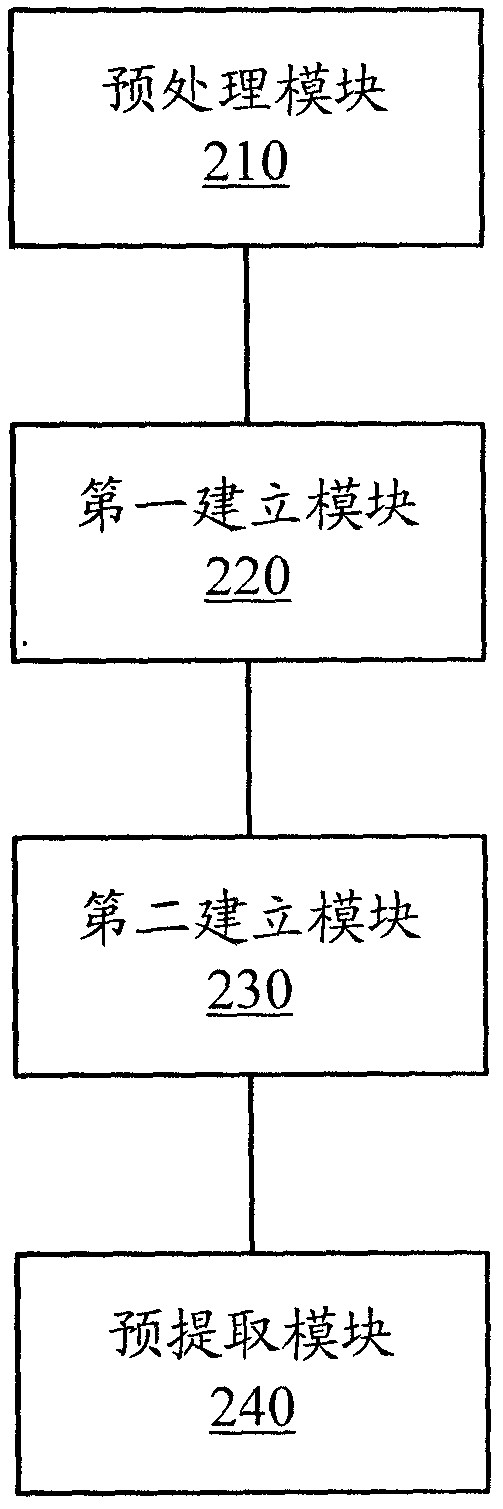
[0079] to combine figure 1 Examples shown, such as figure 2 The shown embodiment mainly includes a preprocessing module 210, a first building module 220, a second building module 230 and a pre-extraction module 240, wherein:
[0080] A preprocessing module 210, configured to preprocess the network log to obtain a trusted network log;
[0081] The first building module 220 is connected with the preprocessing module 210, and is used for selecting characteristic web pages and segmenting URLs according to the user's access interest and the credible web log, and establishing a user browsing access pattern matrix based on a weighted random index method;
[0082] The second building module 230, connected with the first building module 220, is used to optimize the clustering of the user's browsing access pattern matrix using a clustering algorithm based on chaotic ant colony optimization, and mark the user's categor...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com