Method and system for destroying electronic documents regularly
A technology of electronic documents and system parameters, applied in electronic digital data processing, instruments, calculations, etc., can solve problems such as complex management, achieve the effects of ensuring confidentiality, convenient user operation, and simple implementation methods
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
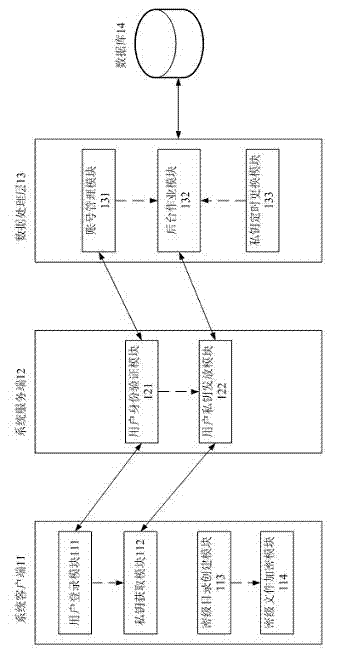
[0123] see figure 1 , the electronic document timing destruction system in the present embodiment can be divided into four layers as a whole, including system client 11, system server 12, data processing layer 13 and database 14; Wherein:
[0124] The system client 11 includes a user login module 111, a private key acquisition module 112, a secret directory creation module 113 and a secret file encryption module 114; the system client 11 is embodied as an application software, which provides a login interface and additional functions of the right button for ordinary users , the login interface provides the user with a visual interface to connect to the system server 12, which requires the user to input the user account number and protection password; the additional functions of the right button include primary encryption, secondary encryption, tertiary encryption and decryption; when selecting a After clicking the right button of the electronic document, you can select level 1...
Embodiment 2
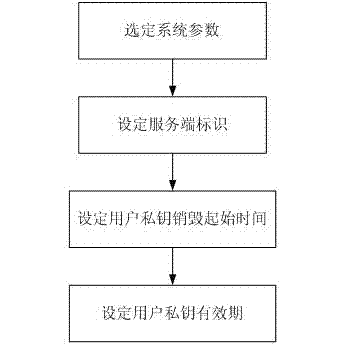
[0129] see figure 2 , the electronic official document timing destruction method server system initialization process of the present invention, concrete steps are as follows:
[0130] (1) Select the system parameter T S =(p,a,b,G,P pub ,q,h,H,I,H 1 , I 1 ), the parameter selection process is as follows:
[0131] a) Choose a prime number finite field F p , select domain elements a, b∈F p Satisfy the equation: E:y 2 ≡x 3 +a·x+b(modp). where 4·a 3 +27·b 2 ≠0(modp);
[0132] b) on curve E(F p ) to select a base point G=(x G ,y G ), and calculate the order q of point G, h=#E(F p ) / q. These parameters satisfy the following constraints: #E(F p )≠p; p B ≠1(mod q), where 1≤B<20; h≤4; p, q must also satisfy p=2mod3 and p=6q-1;
[0133] c) generate a random number s is the master key of the system, and calculate P pub =s·G;
[0134] d) Choose four hash functions: I: {0, 1} * → F p , H 1 :{0, 1} n × {0, 1} n → F q , I 1 :{0, 1} n → {0, 1} n ;
[0135] (...
Embodiment 3
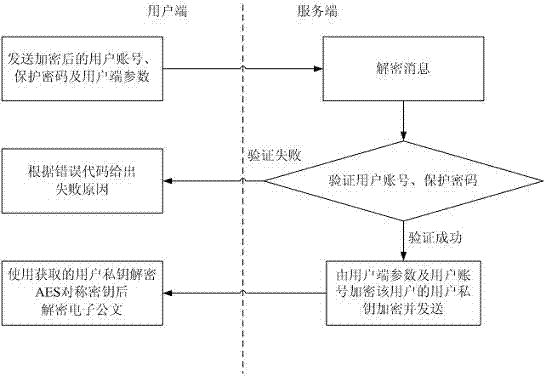
[0142] see image 3 , the user identity verification and the user private key distribution process of the method for regularly destroying electronic documents according to the present invention, the specific steps are as follows:
[0143] (1) Internal users of the organization enter the user account ID through the login interface of the client software U And protect the password pwd and submit;
[0144] (2) The client software uses the identification ID of the system server S Encrypt the following information: M=ID U ||pwd, where || means connection, ID U Represents the user account, that is, the user ID; pwd represents the protection password, that is, the user password; the encryption process is as follows:
[0145] a) Set the server ID to S Mapped to the elliptic curve E(F p ) on a point P of order q S ;
[0146] b) Choose a random string σ, set r=H 1 (σ,M);
[0147] c) Calculate the ciphertext C = rP , ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com