Method and device for processing service key
A technology of service key and processing method, which is applied in the field of service key processing, can solve problems such as different user identities, attacks, and illegal viewing of TV programs, and achieve the effect of ensuring user experience and preventing attacks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
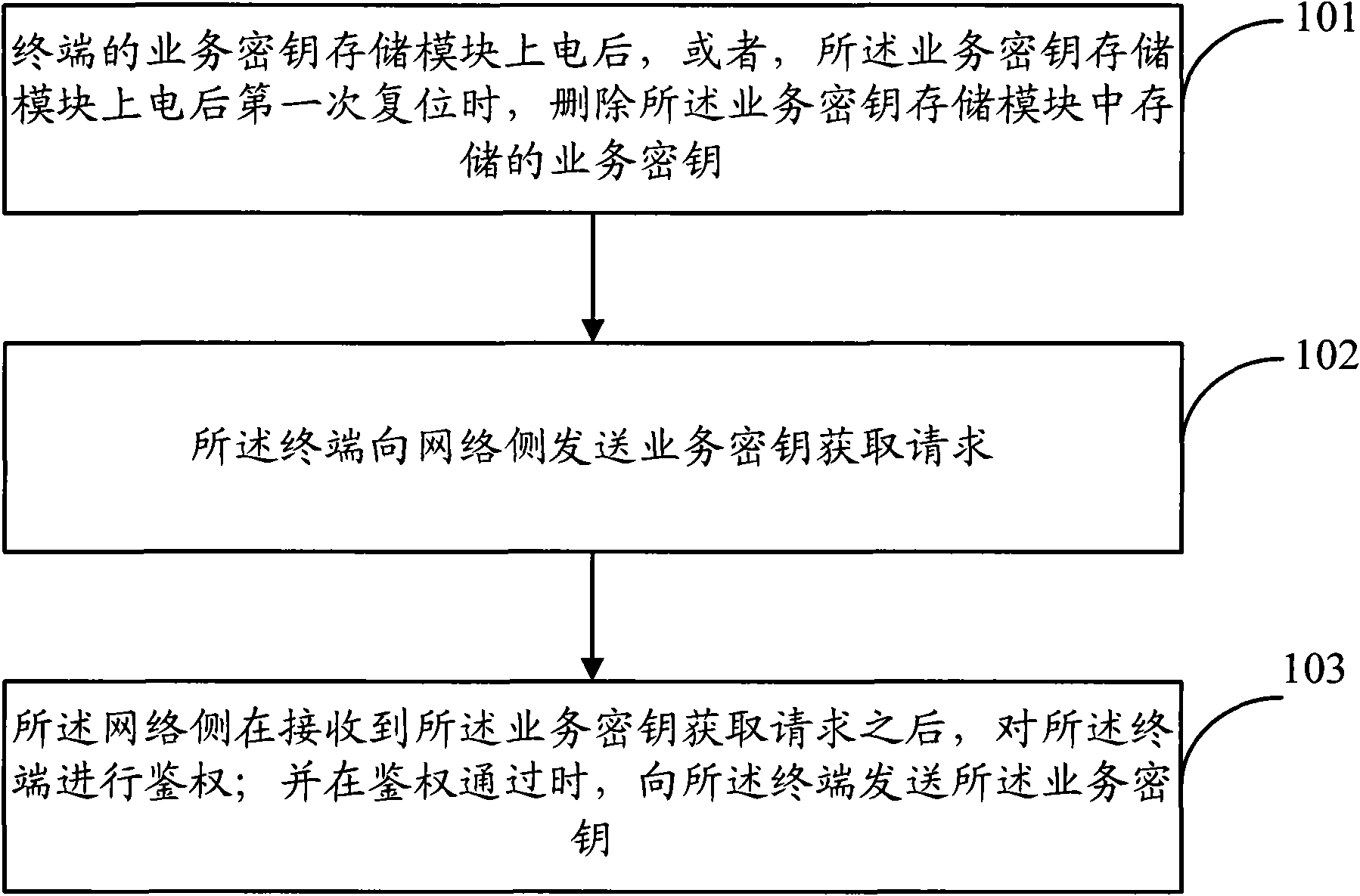
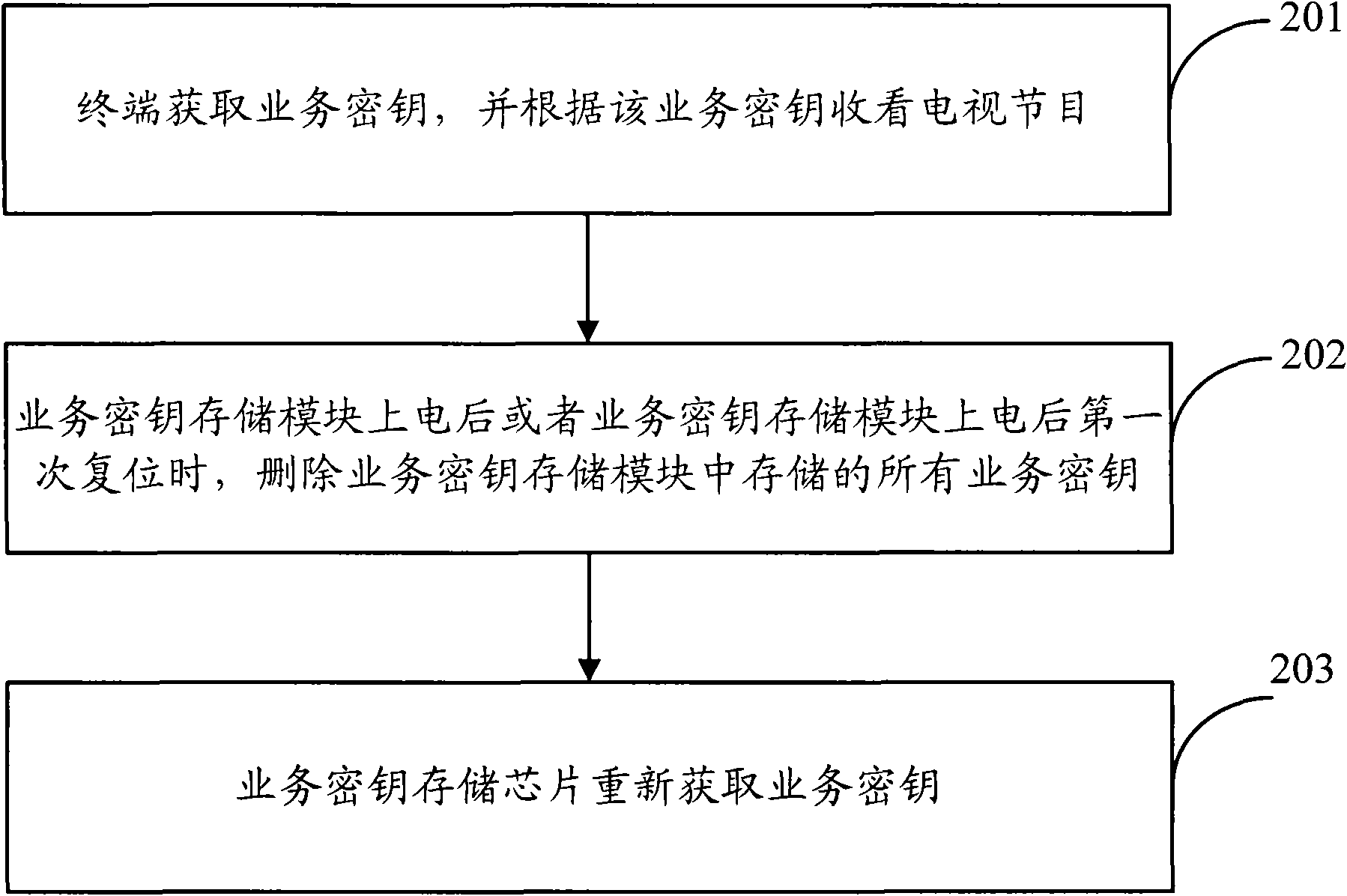
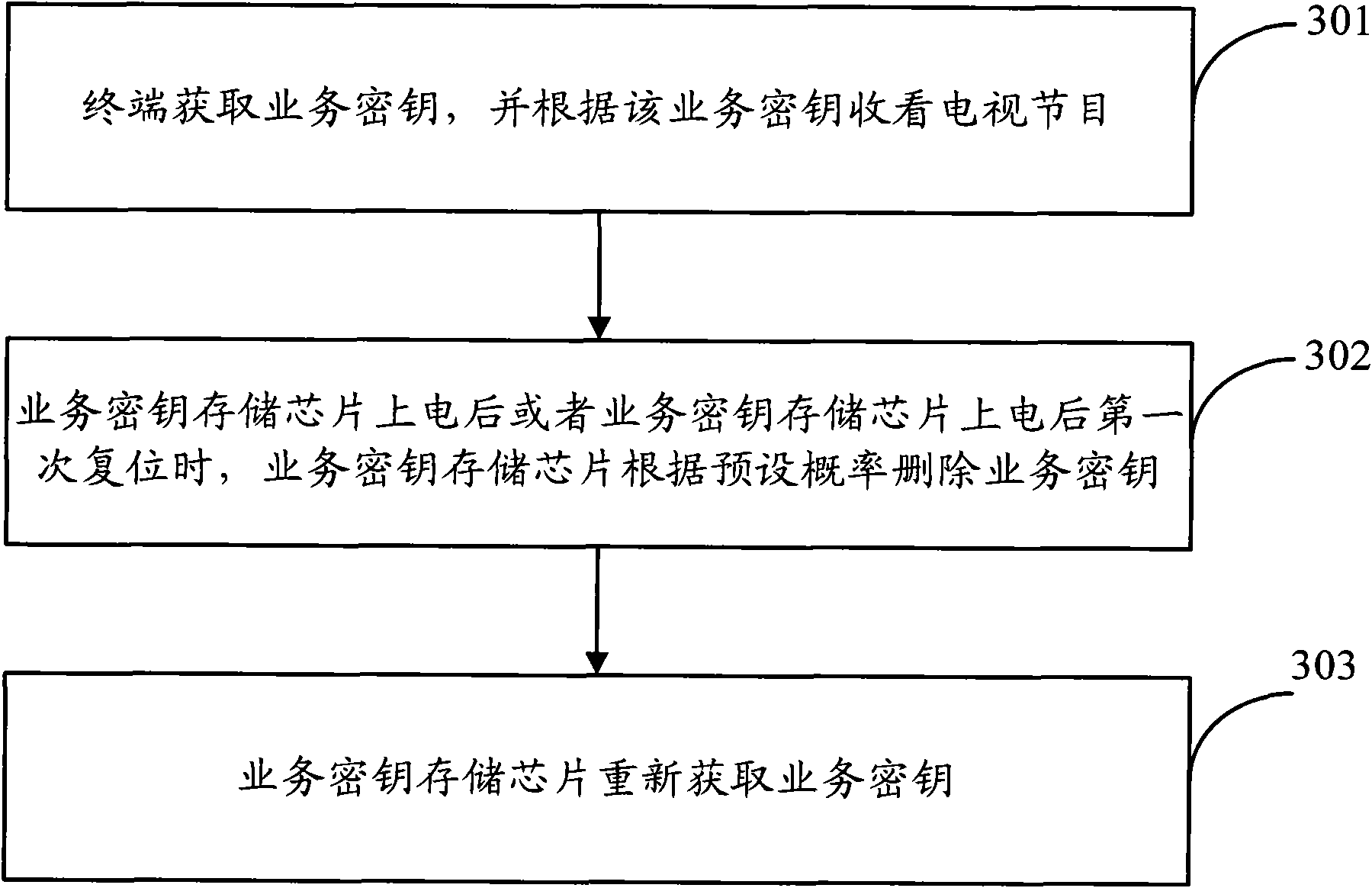
[0047] In the embodiment of the present invention, when the terminal is powered on, the service key stored in the service key storage module is deleted, thereby making up for the service security loophole caused when the service key storage chip is separated from the user authentication module, and preventing illegal users The attack behavior, as far as possible to ensure the user experience of legitimate users. Moreover, the present invention only needs to make a small amount of changes to the service key storage chip, and does not affect the service process and service logic of the terminal and the platform, thereby ensuring the service key security requirements at a relatively small cost.
[0048] The technical solutions of the present invention will be clearly and completely described below in conjunction with the accompanying drawings in the present invention. Obviously, what is described is only a part of the present invention, but not all of it. Based on the present invent...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com