Novel message signature method for sparse movable Ad Hoc network
A network message, sparse technology, applied in the direction of electrical components, wireless communication, security devices, etc., to achieve the effect of reducing the length
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0041] The present invention has no special requirements on the specific network topology structure of sparse Ad Hoc and the properties of network nodes, and the method of the present invention can be applied to any sparse mobile Ad Hoc network for message signature authentication, and can be widely used in various sparse Ad Hoc scenarios .
[0042] The following is a detailed introduction to the step process of the embodiment:
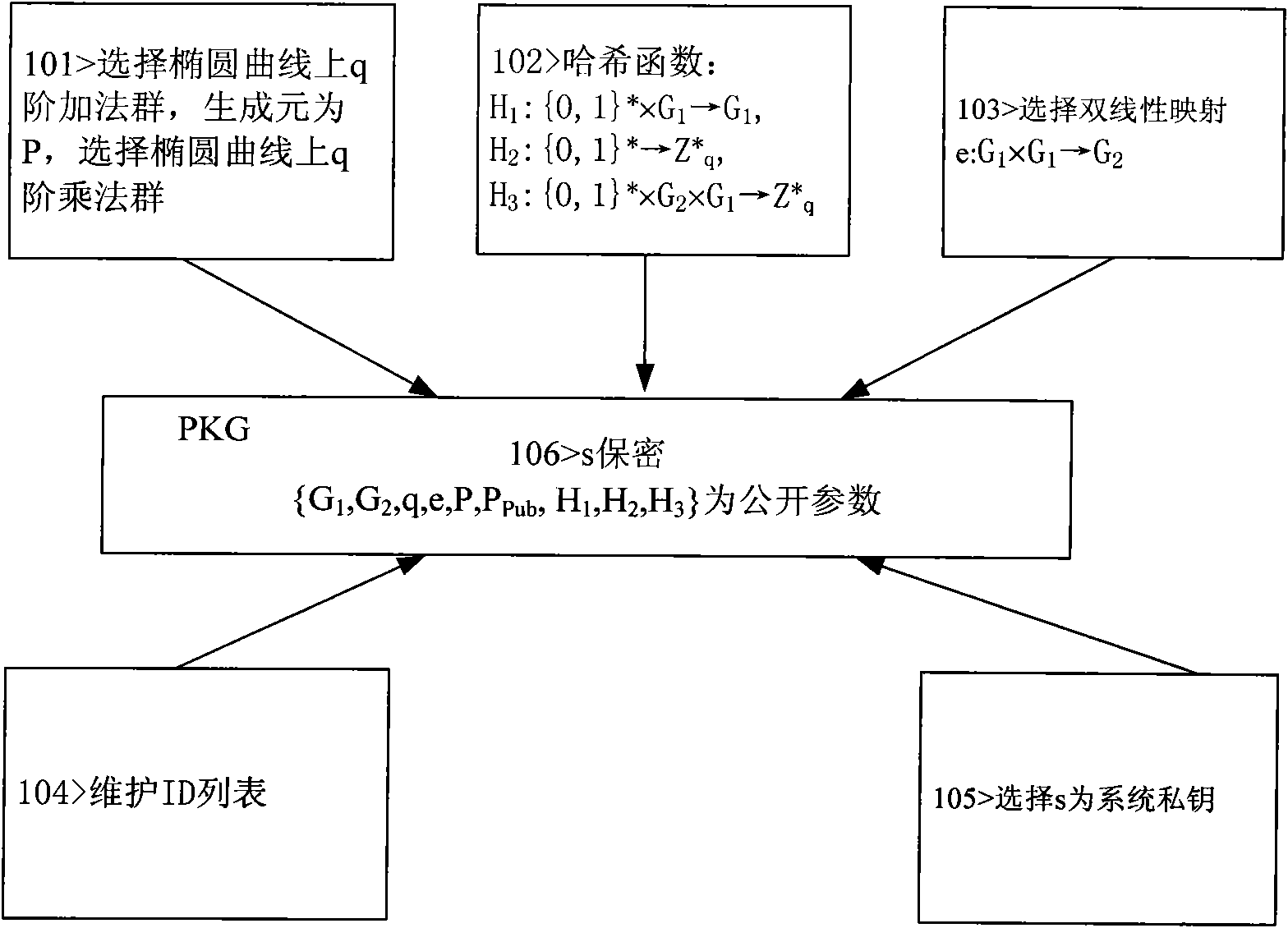
[0043] Such as figure 1 Shown, the system establishment step flow process of the present invention is as follows:
[0044] Step 101: PKG selects the additive group G whose upper order is q on the elliptic curve 1 , the multiplicative group G of order q 2 , G 1 The generator of is P, |G 1 |and|G 2 |both are 160, that is, the length of the elliptic curve key used is 160 bits;
[0045]Step 102: Select a hash function H 1 : {0, 1}*×G 1 →G 1 ,
[0046] Step 103: Select a bilinear map
[0047] Step 104: PKG maintains the ID list, records the...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com