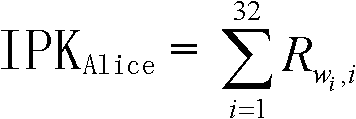Generation method of bimatrix combined public key
A technology of combining public keys and matrices, applied to the public key and key distribution of secure communication, it can solve the problems of collusion attack, difficulty in proof, inability to realize digital signature, etc., and achieve the effect of reducing storage amount and increasing variation amount.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
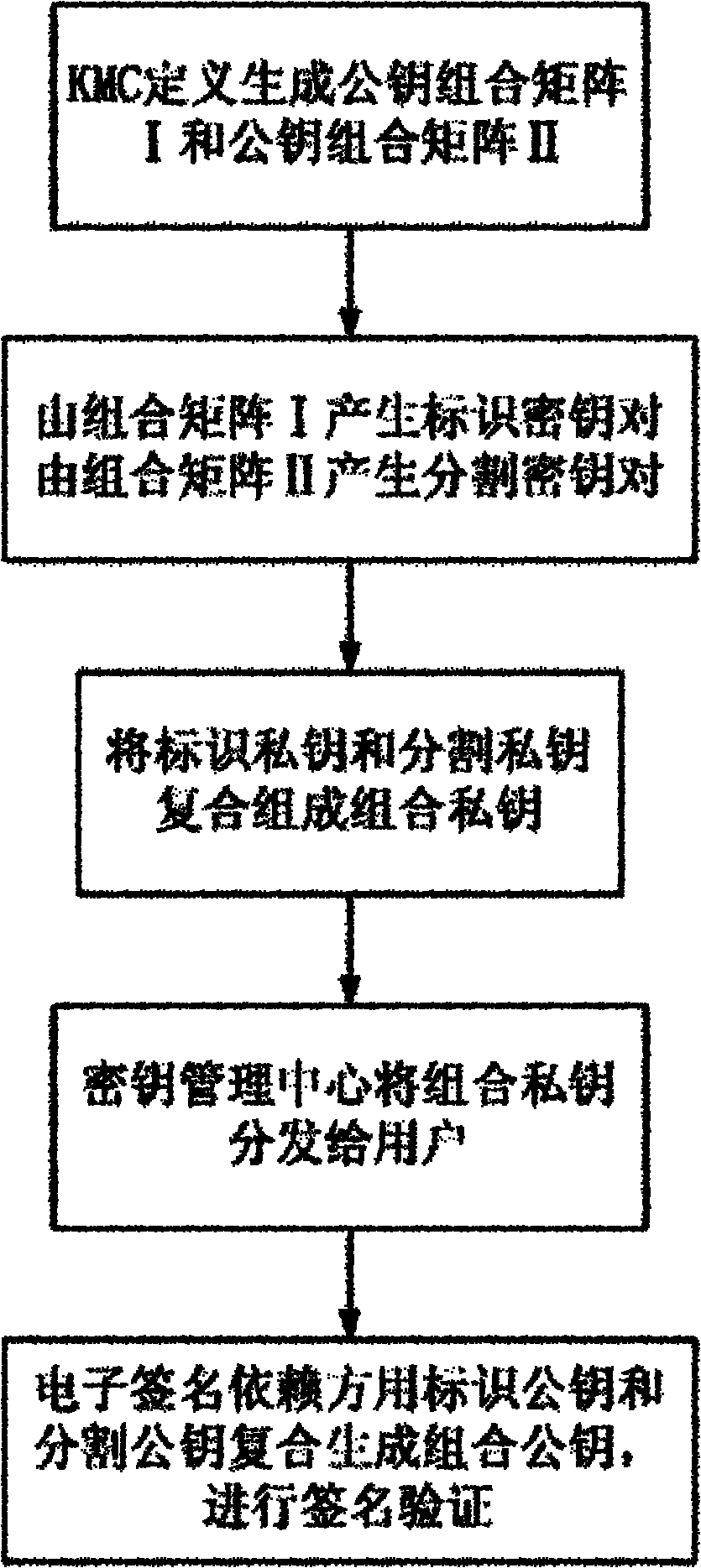
[0037] The public key system is a technical means to realize digital signature and key exchange. In the identification system, identification identification is the core of identification. The specific implementation of the identification authentication system according to the present invention will be further described in detail from the aspects of system, protocol, etc. below. It should be noted that the specific implementation of the double-matrix combined public key technology and identification authentication system according to the present invention is only an example, but the present invention is not limited to this specific implementation.
[0038] The following is a detailed description of the double-matrix combined public key system:
[0039] The dual-matrix combined public key is implemented on the basis of the combined public key (CPK). For details, please refer to the applicant's prior application 200510002156.4 "Key Generation Method Based on Identification".
...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com