Ship invisibility and management method
A management method and ship technology, applied in the information field, can solve the problems that the law enforcement monitoring management center cannot manage
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
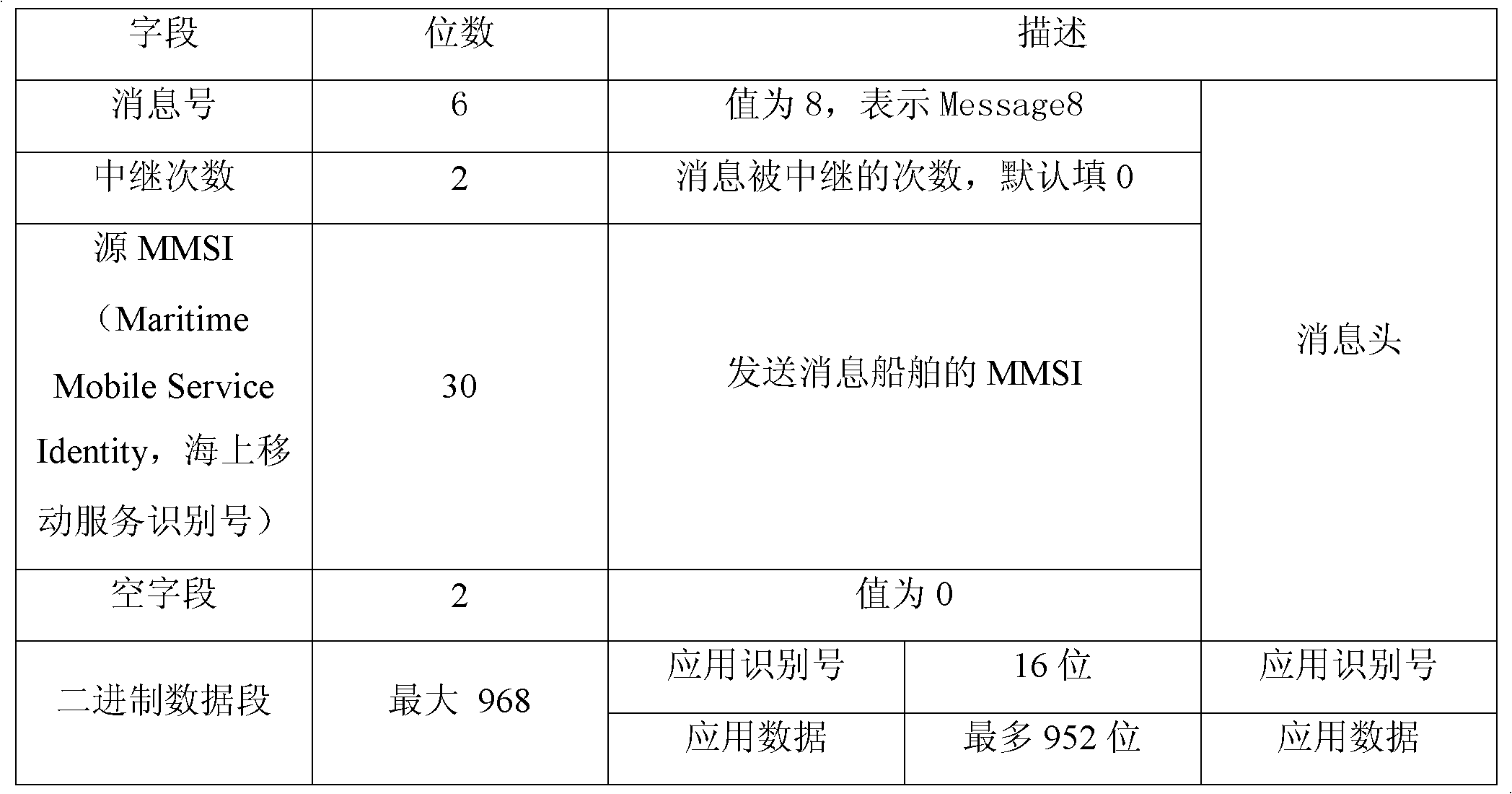
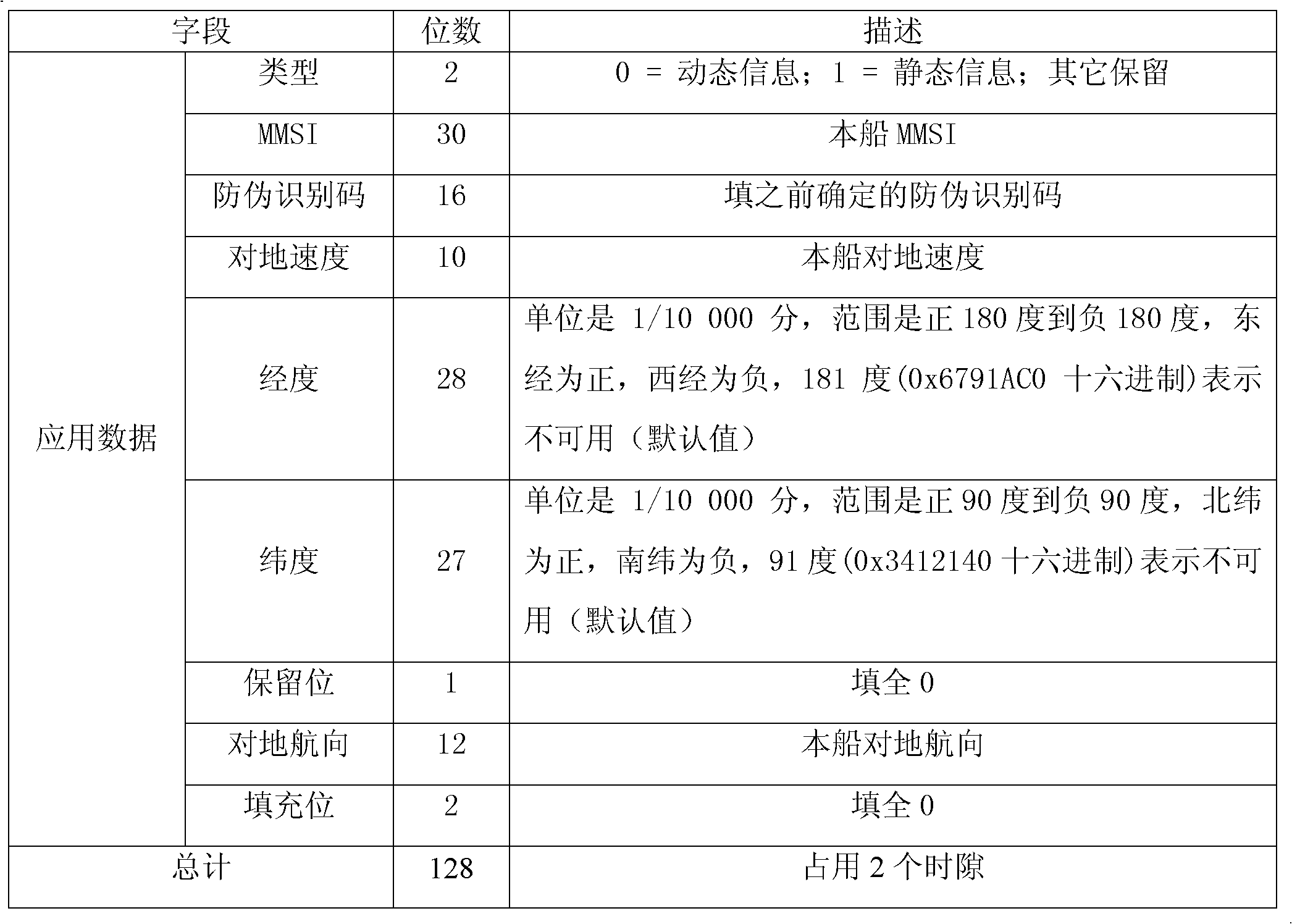
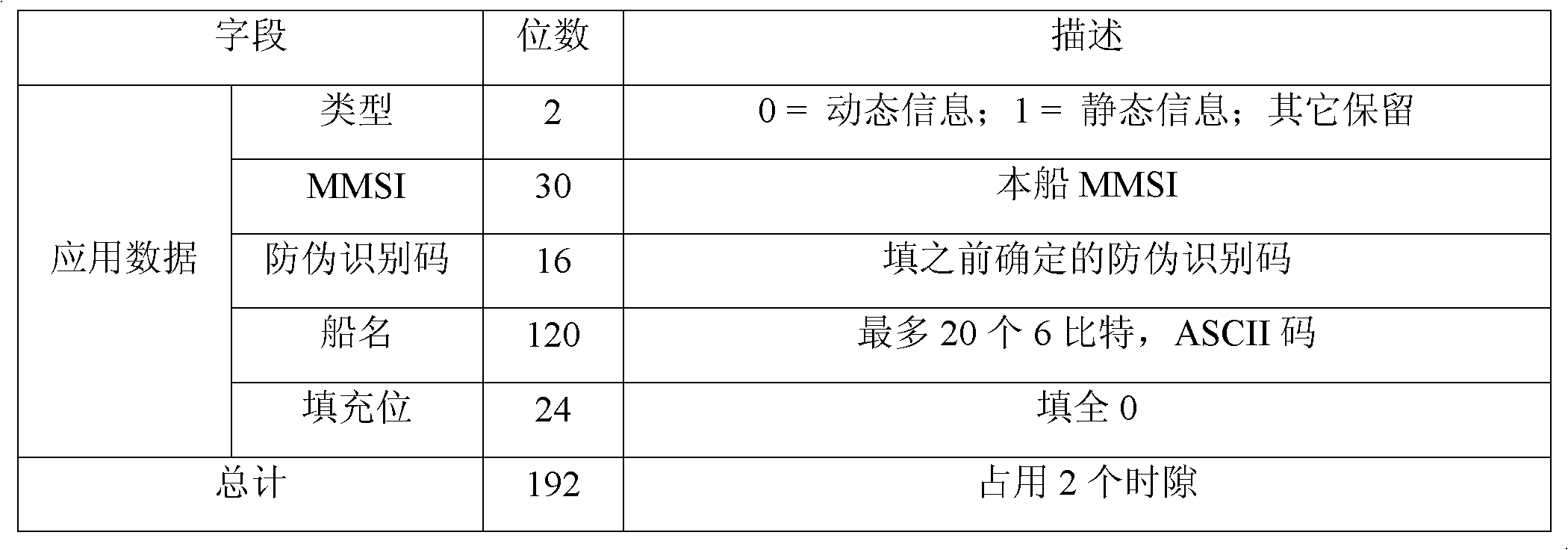
[0025] In this example, the method for encrypting dynamic and static messages and anti-counterfeiting identification codes is to use the RC2 block encryption algorithm.
[0026] First, set the same key in the law enforcement monitoring management center and the AIS ship-borne equipment of each law enforcement ship, and determine the application identification number and anti-counterfeiting identification code in the stealth mode, and then set the AIS ship-borne equipment of each law enforcement ship to provide normal mode And the switching function of the stealth mode, when the AIS shipboard equipment of the law enforcement ship is in the normal mode, it will normally send the normal message message corresponding to the model of the AIS shipboard equipment, when the AIS shipboard equipment of the law enforcement ship is in the stealth mode , to determine whether the ground speed of the law enforcement ship is greater than 2 knots, and if so, the dynamic and static messages and ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com