Method for attacking Fourier transform quantum secret sharing systems
A Fourier transform and quantum secret technology, which is used in the field of attacks on Fourier transform quantum secret sharing systems, and can solve problems such as lack of security testing methods
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0070] In order to express the purpose and technical solution of the present invention more clearly, further detailed description will be given below in conjunction with the accompanying drawings and specific implementation methods.
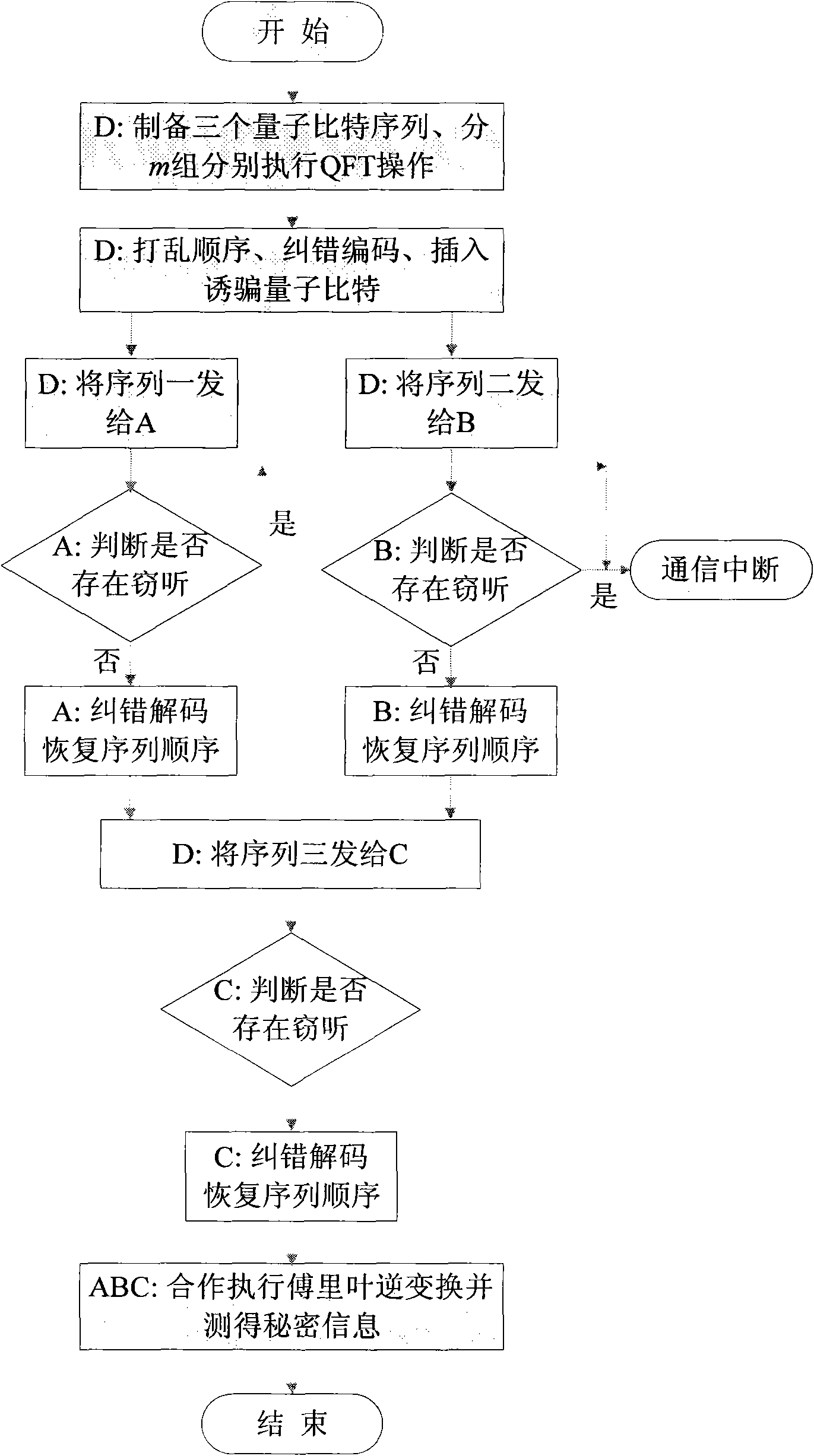
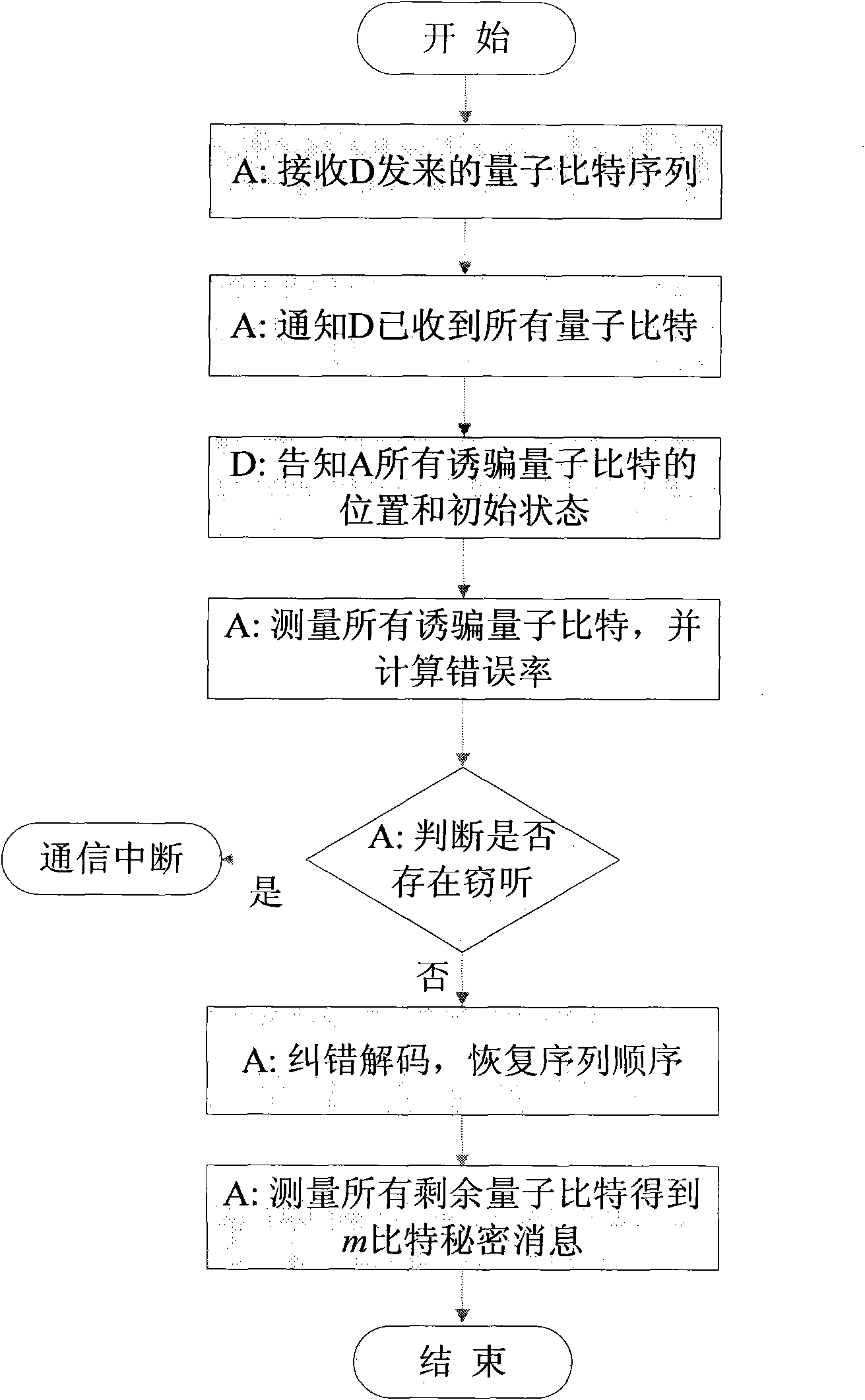
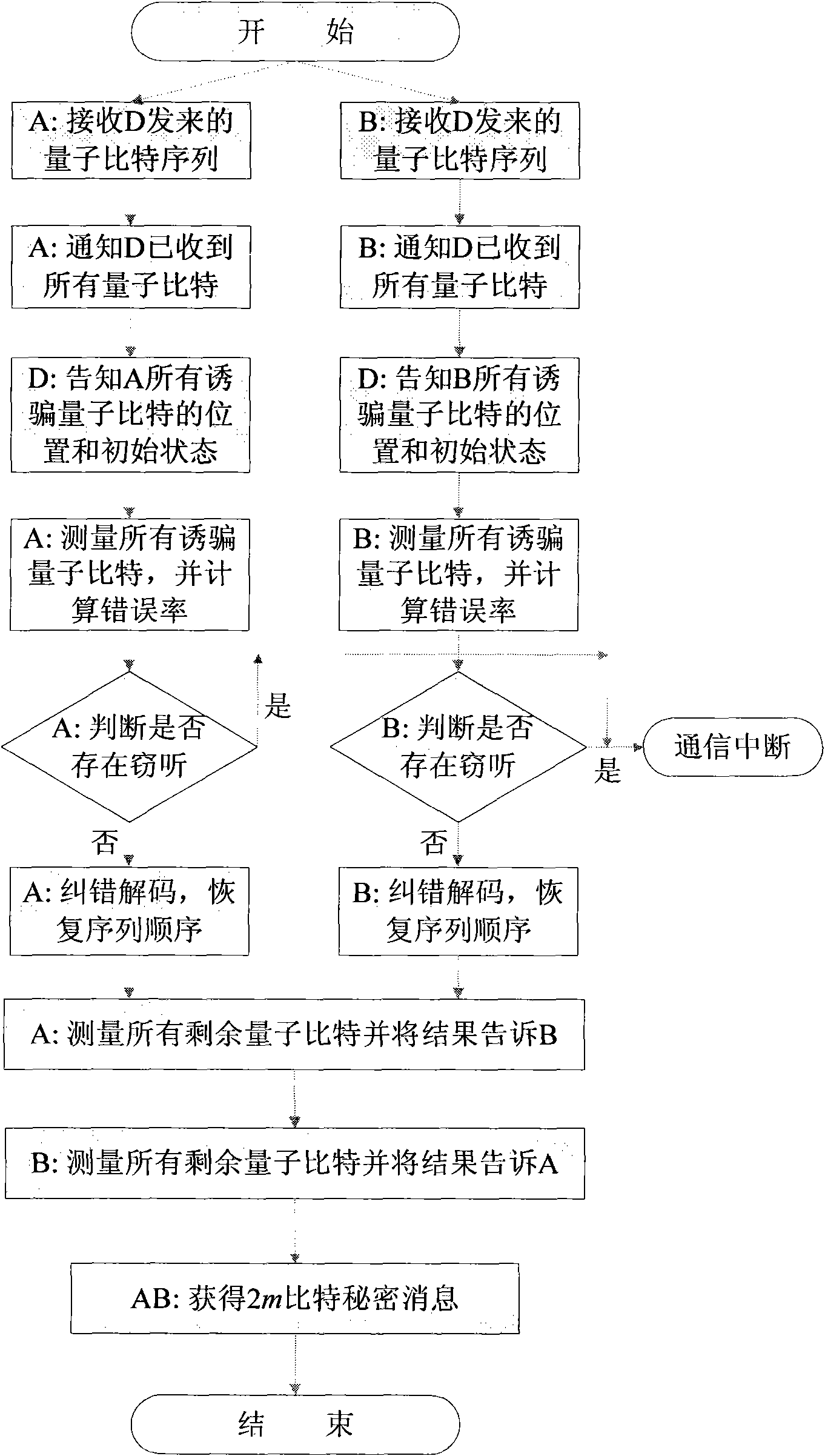
[0071] The invention provides an attack method on the Fourier transform quantum secret sharing system. This method allows agent Alice to obtain m bits of a 3m-bit secret message by single-event measurement alone, or enables agent Alice and Bob to cooperate to obtain 2m bits of a secret message. In this way, a dishonest agent can obtain part of the secret message, and will not introduce any disturbance to the quantum state, which will not be discovered by the distributor. This attack method is simple and effective, and it can be used as a security testing method for this kind of QSS system.
[0072] Still taking the (3,3) Fourier transform QSS system as an example, the attack method of the present invention will be introduced respectively in two ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com