Article identification system and authorization method thereof
A technology of identification and items, applied in the field of identification, can solve problems such as the inability to really solve the anti-counterfeiting problem, the use of anti-counterfeiting numbers by counterfeiters, and the product inquiry rate of the telephone anti-counterfeiting system being less than 1%.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
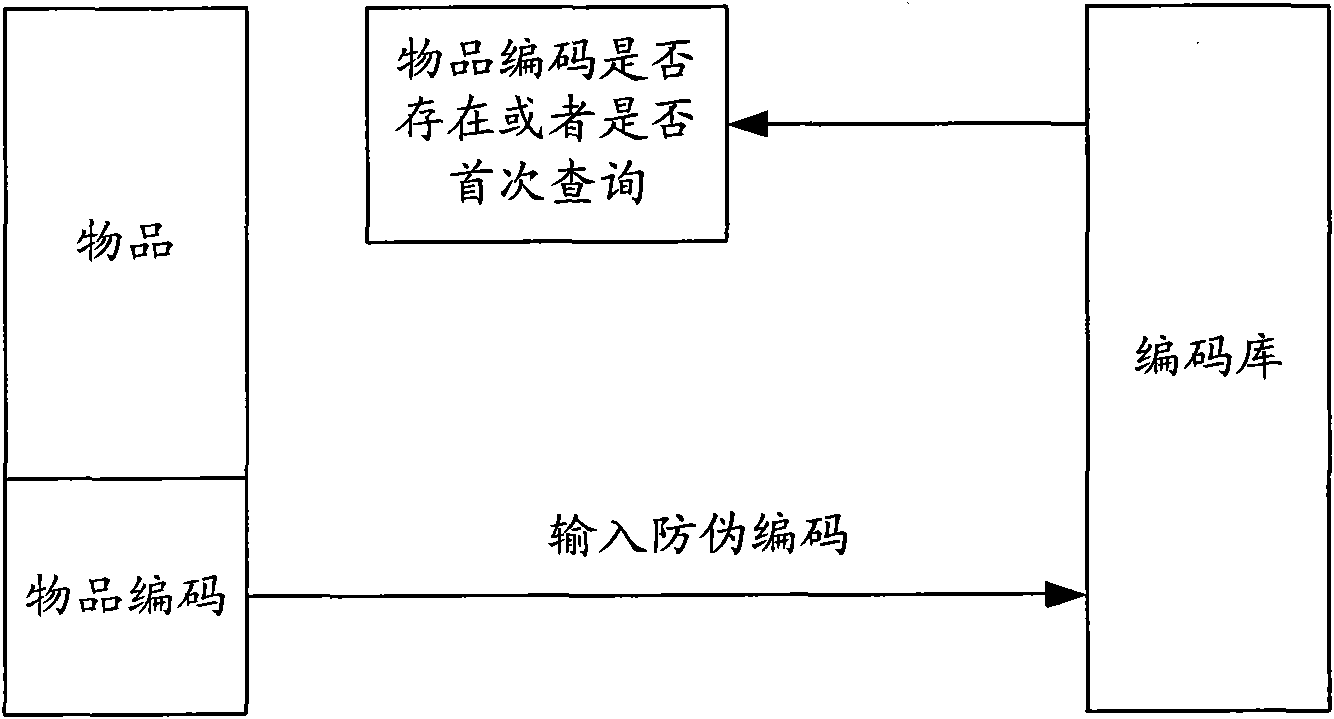
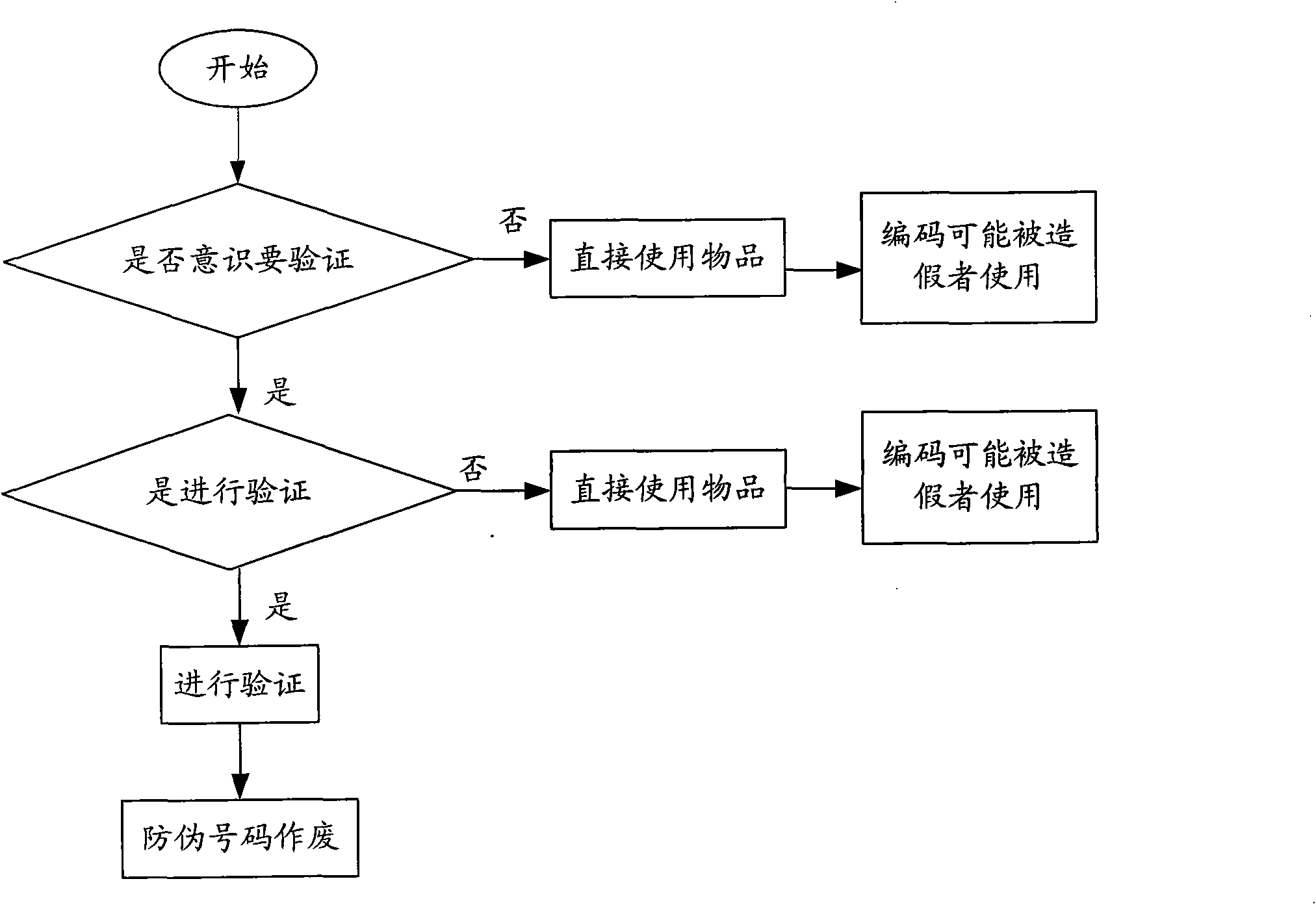
[0050]The technical side of the present invention has developed a brand-new anti-counterfeiting technology. The binding of the verified item with the password and the combination lock cannot or is not easy to separate. When using it, the identification of the authenticity of the item is realized while the item code is queried. , which revolutionized the way queries are done only on encodings.
[0051] The technical solutions of the present invention will be described in detail below with reference to the accompanying drawings and preferred embodiments.
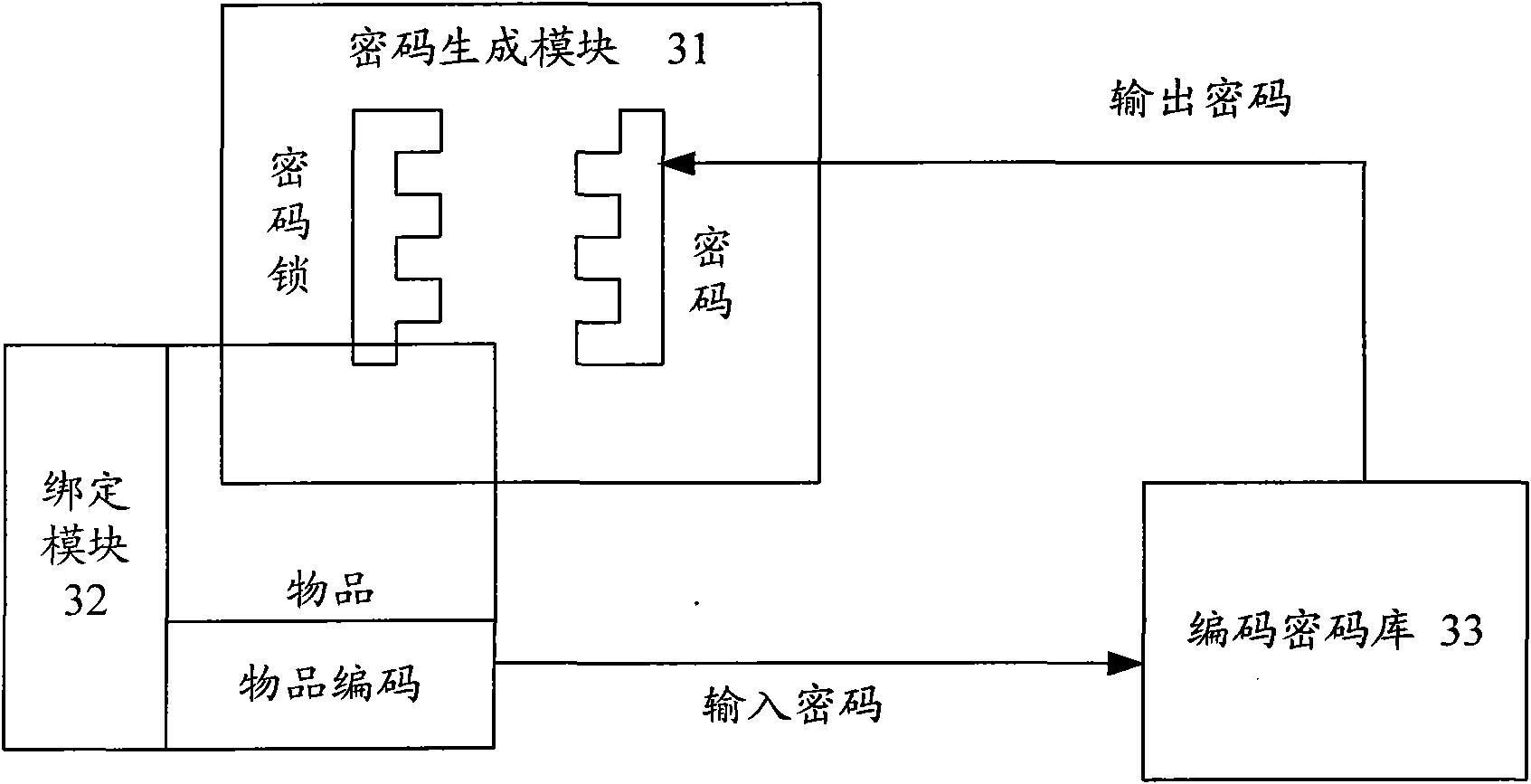
[0052] Such as image 3 Shown is the principle diagram of the item identification system in the present invention. The structure of the item identification system includes: a code generation module 31 , a code generation and binding module 32 and a code code library 33 .
[0053] Wherein, the password generation module 31 is used to generate a password and carry out password setting to the combination lock, then, the passwor...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com