Method and device for identifying business data in peer-to-peer network
A technology of business data and peer-to-peer network, applied in the direction of data exchange network, digital transmission system, electrical components, etc., can solve the problems of low work efficiency, time-consuming and labor-consuming developers, etc., and achieve the goal of improving work efficiency and realizing regularization Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
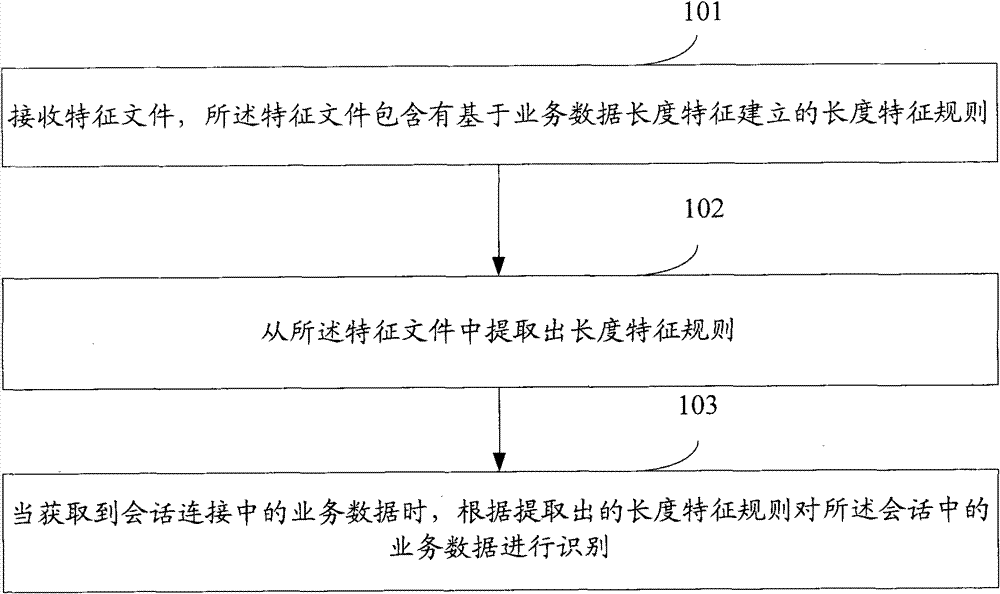
[0026] see figure 1 , which is a method for identifying business data in a peer-to-peer network in the present application, the method includes the following steps:
[0027] Step 101: receiving a feature file, the feature file includes a length feature rule established based on the length feature of business data;
[0028] Wherein, the length feature includes: the number of identified packets, the length feature of the identified packets, and the sequence of the length feature.
[0029] The identified length feature includes: any one or any combination of a preset fixed value, a preset interval value, and preset discrete values.
[0030] For example, the session types in the current P2P technology include: BT, eMule and Vagaa, etc. When identifying the service data whose session type is BT based on the feature of service data length, the corresponding length rule is: in any three consecutive messages in a session connection, if the length of the first message is 56 character...
Embodiment 2
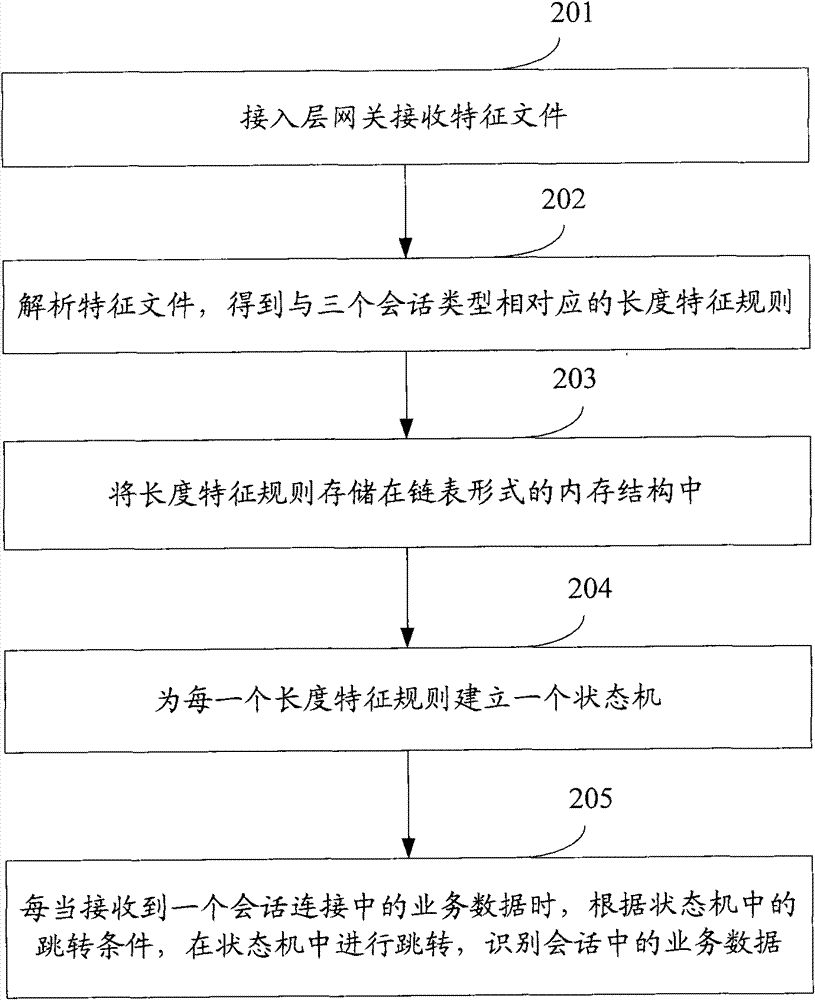
[0043] The method for identifying service data in the peer-to-peer network will be described in detail below by taking a peer-to-peer network structure as an application scenario. see figure 2 , which is a flow chart of another embodiment of a method for identifying service data in a peer-to-peer network of the present application, and the identification method specifically includes the following steps:
[0044] Step 201: the access layer gateway receives the feature file;
[0045] Among them, see image 3 , which is a schematic structural diagram of a peer-to-peer network in the present application, such as image 3 As shown, the P2P network structure is different from the traditional C / S structure and B / S structure. There is no central node or central server in the entire network, and each node in the network has three functions: information consumer, information provider and information communication. aspects of the function. In order to realize the identification of b...
Embodiment 3
[0072] Corresponding to the foregoing method for identifying service data in a peer-to-peer network, an embodiment of the present application further provides an apparatus for identifying service data in a peer-to-peer network. see Figure 5 , which is a structural diagram of an embodiment of an apparatus for identifying service data in a peer-to-peer network in the present application, and the apparatus includes a receiving unit 501 , an extracting unit 502 and an identifying unit 503 . The internal structure and connection relationship of the device will be further introduced below in conjunction with the working principle of the device.
[0073] The receiving unit 501 is configured to receive a feature file, the feature file includes length feature rules established based on service data length features;
[0074] An extraction unit 502, configured to extract length feature rules from the feature file;
[0075] The identification unit 503 is configured to identify...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com