Power station automation system data network security monitoring method
An automation system and data network technology, which is applied in the field of data network security monitoring of power station automation systems, can solve the problem that the massive data transmission of the power station network cannot be effectively controlled, the non-important data occupies limited bandwidth resources, and the real-time important data transmission is affected, etc. problem, to achieve the effect of less vulnerable to attack, short delay, and fast processing speed
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0043] The present invention will be described in further detail below in conjunction with the accompanying drawings and specific embodiments.
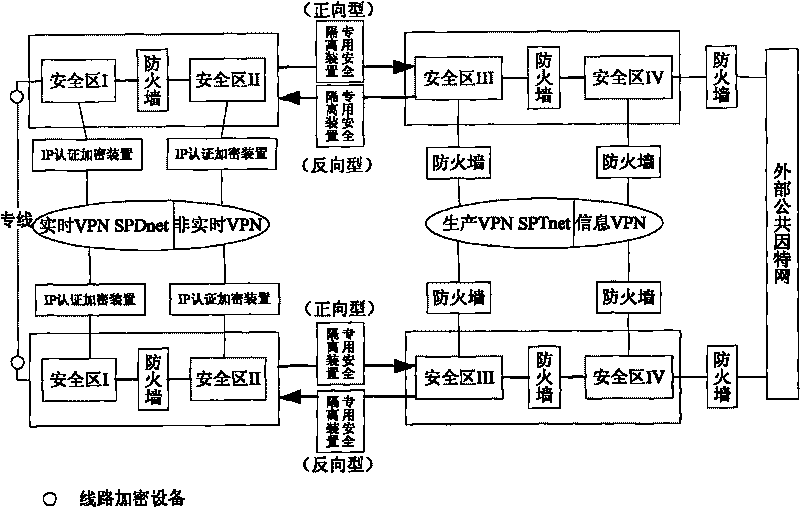
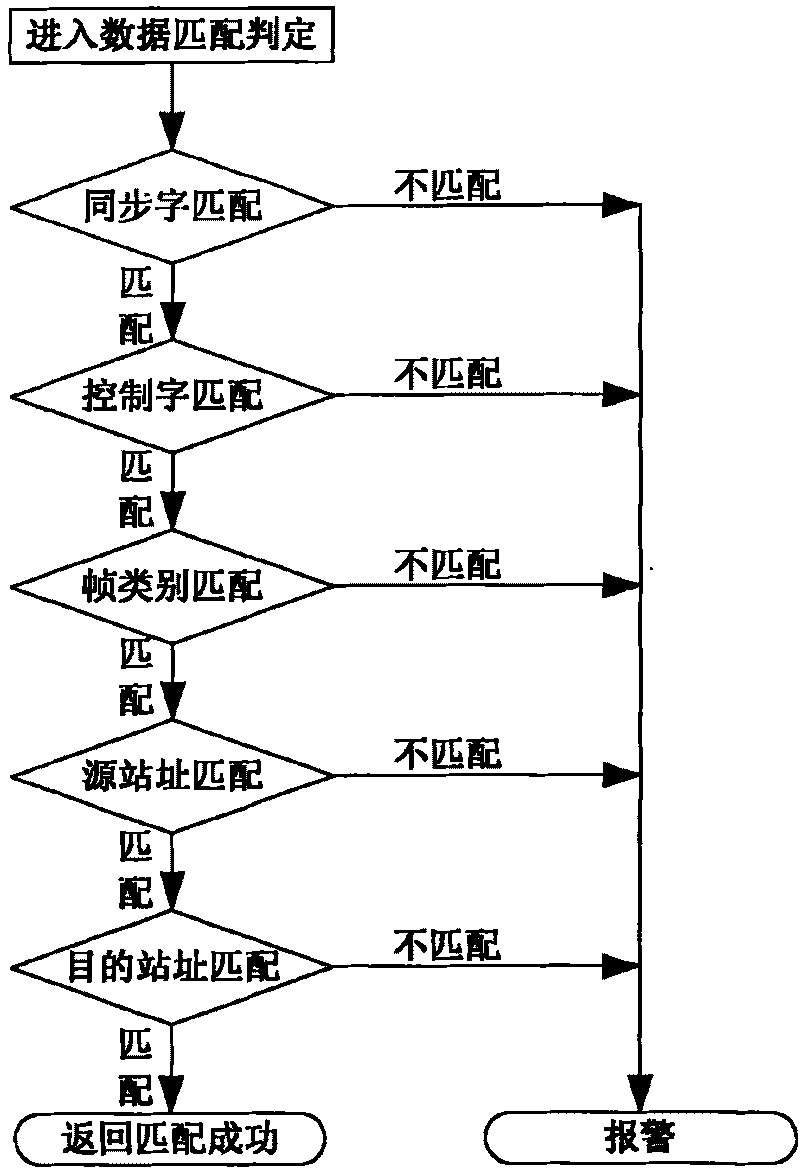
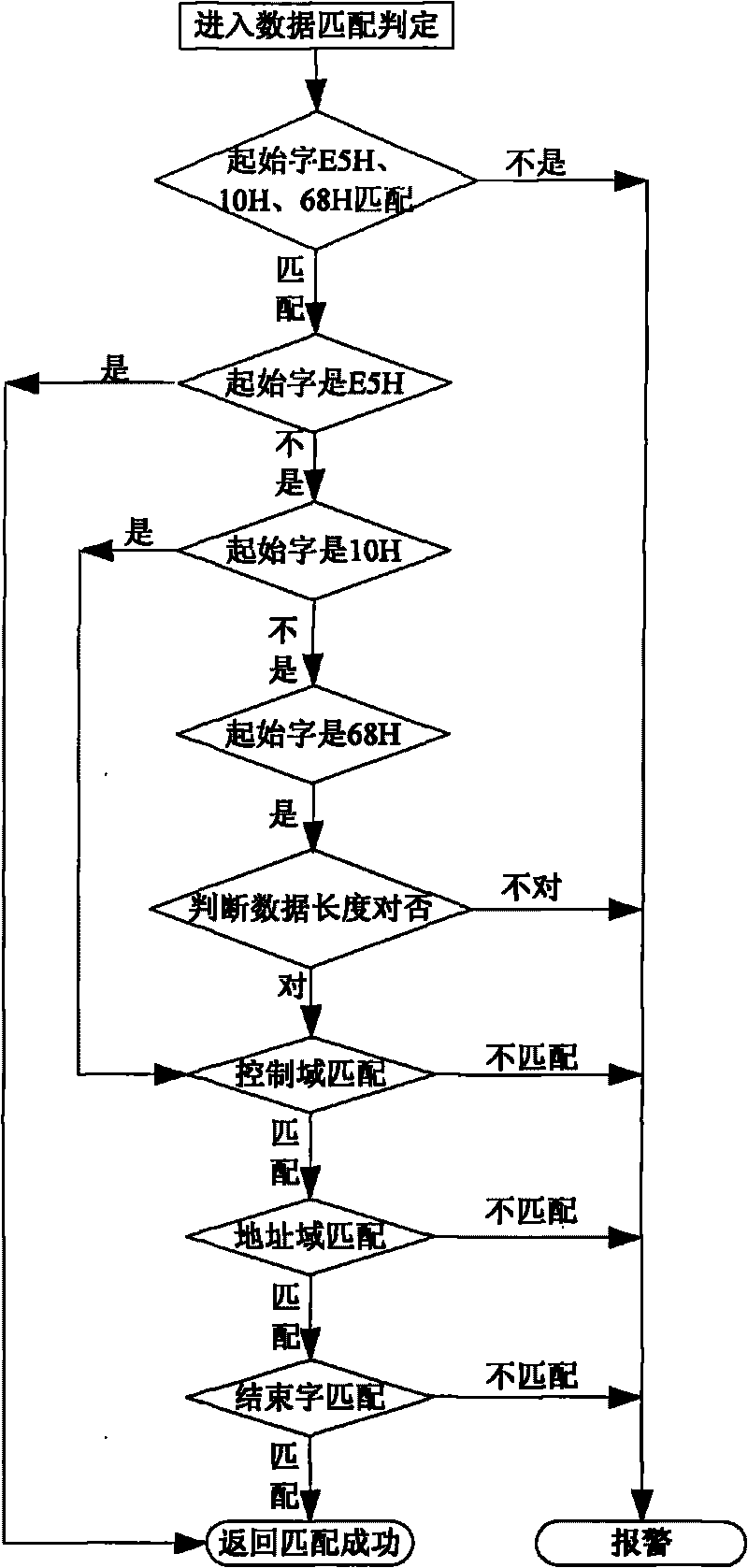
[0044]A power station automation system data network security monitoring method, which uses the Snort detection engine to monitor the power station automation data network on the existing power system computer network system. The protocols embedded in the engine include CDT, IEC-60870-101 and IEC - The communication protocol including 61850 uses the frame format of the protocol itself to establish engine matching conditions. The operating platform of the monitoring device used in the present invention adopts Sis550CPU as the processor, selects Vortex6082 of ICOP Company as the integrated main board, the memory configuration is 128MB onboard, and the hard disk selects 32MB DOM electronic disk for use. The device uses a streamlined Linux operating system and uses the Snort intrusion detection system (IDS) to complete the detection of il...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com