Safe and effective privacy protection method of P2P system
A privacy protection and security technology, applied in the transmission system and key distribution, can solve problems such as complex algorithms, waste of bandwidth, and inconvenient implementation, and achieve the effect of privacy protection and privacy protection enhancement
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
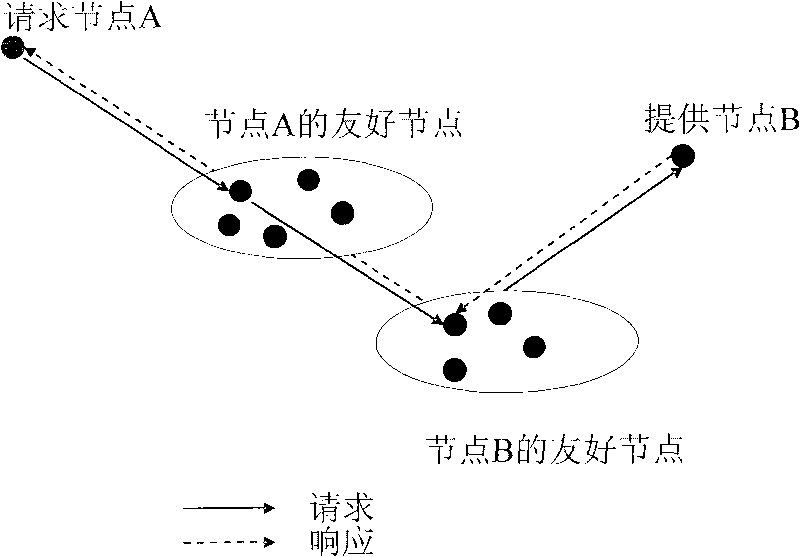
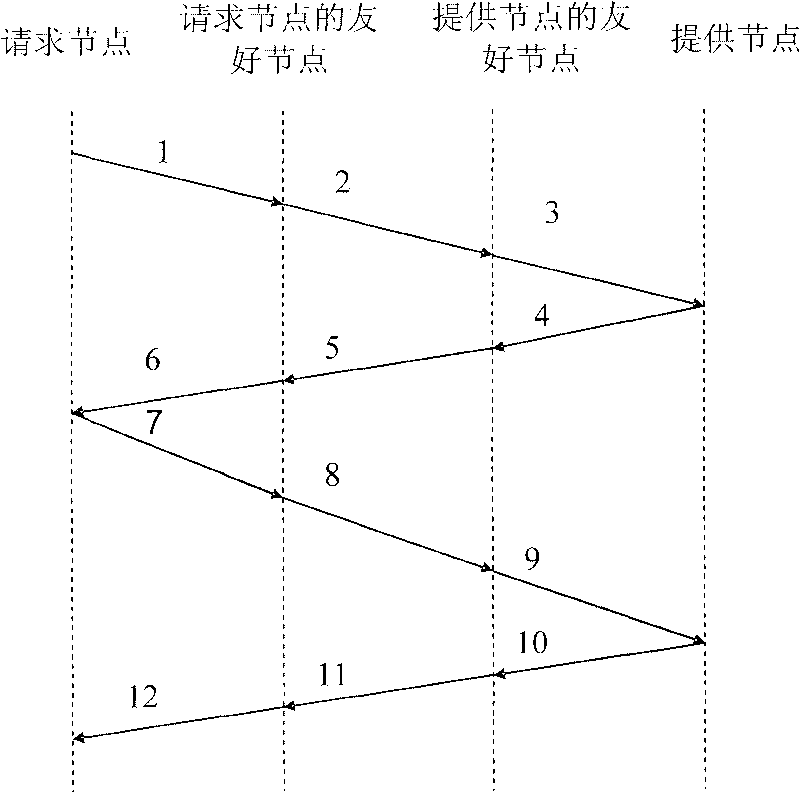
[0011] Specific implementation examples such as figure 2 As shown, it has the following characteristics:
[0012] The whole P2P system includes several resource providers, resource requesters and their friendly nodes.
[0013] The implementation of the present invention includes three stages: the resource provider, the trust establishment between the resource requester and its friendly nodes, the resource requester requesting resources and the resource provider providing resources.
[0014] Trust building phase:
[0015] Due to the need to establish a certain degree of trust relationship with friendly nodes in advance, some privacy of nodes will be leaked to their friendly nodes, so the reliability and credibility of friendly nodes are very important to the maintenance of node privacy. We adopt a recommendation-based trust mechanism. Calculated as follows:
[0016] R ( p i ) = ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com