Method, equipment and system for checking temporary key negotiation information
A technology of temporary keys and negotiation messages, which is applied in the field of communication, can solve problems such as failure to respond to negotiation messages, consumption, resource occupation of receiving devices, etc., and achieve the effect of avoiding denial of service attacks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
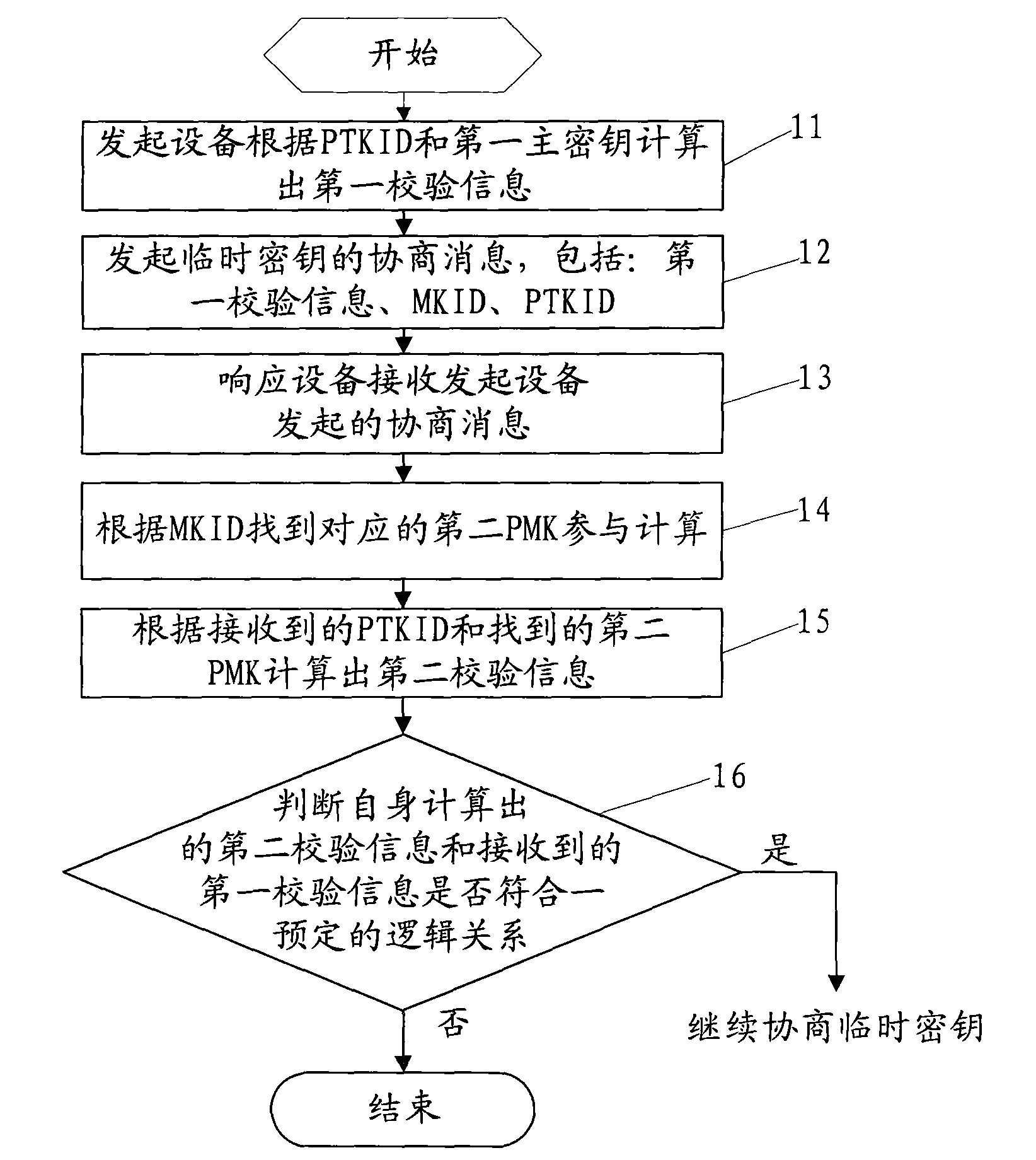
[0041] This embodiment provides a verification method for a temporary key agreement message, such as figure 1 As shown, in this method, when two devices want to communicate, first, both the initiator and the responder will be safely assigned at least one pair of master keys PMK, and each pair of master keys corresponds to a master key identifier ;
[0042] 11. The initiating device calculates the first verification information according to the temporary key identifier (PTKID) and the first master key (PMK).
[0043] It needs to be confirmed that in the embodiment of the present invention, the verification information does not necessarily have to be obtained through calculation, and can also be obtained by presetting optional items and according to the key identifier and the master key.
[0044] 12. Send a temporary key negotiation message to the responding device, the negotiation message includes the calculated first verification information and the master key identifier (MKI...
Embodiment 2
[0061] This embodiment also provides a verification method for a temporary key agreement message, such as Figure 5 As shown, the verification method of the temporary key agreement message in this embodiment includes the following steps:
[0062] 501. Both the initiating device and the responding device are securely distributed to the first and second master keys PMK.
[0063] 502. The initiating device selects a first master key PMK, pre-allocates a temporary key identifier PTKID, and generates a 128-bit random number I-Nonce.
[0064] 503. The initiating device calculates the first derived key PMK' according to the first master key PMK. In this embodiment, calculating the first derived key includes but is not limited to the following methods:
[0065] Define function S=S(PMK, OtherElement), wherein S represents the first derivation key PMK ', the method of derivation can be but not limited to select part of the data bit information from PMK as the first derivation key PMK '...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com