Method for authenticating validity of self-contained software of equipment system
A legality certification and legality verification technology, applied in the field of software legality certification
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0035] The present invention will be further described below in conjunction with specific examples, but the present invention is not limited to these specific implementations. Those skilled in the art will realize that the present invention covers all alternatives, modifications and equivalents as may be included within the scope of the claims.
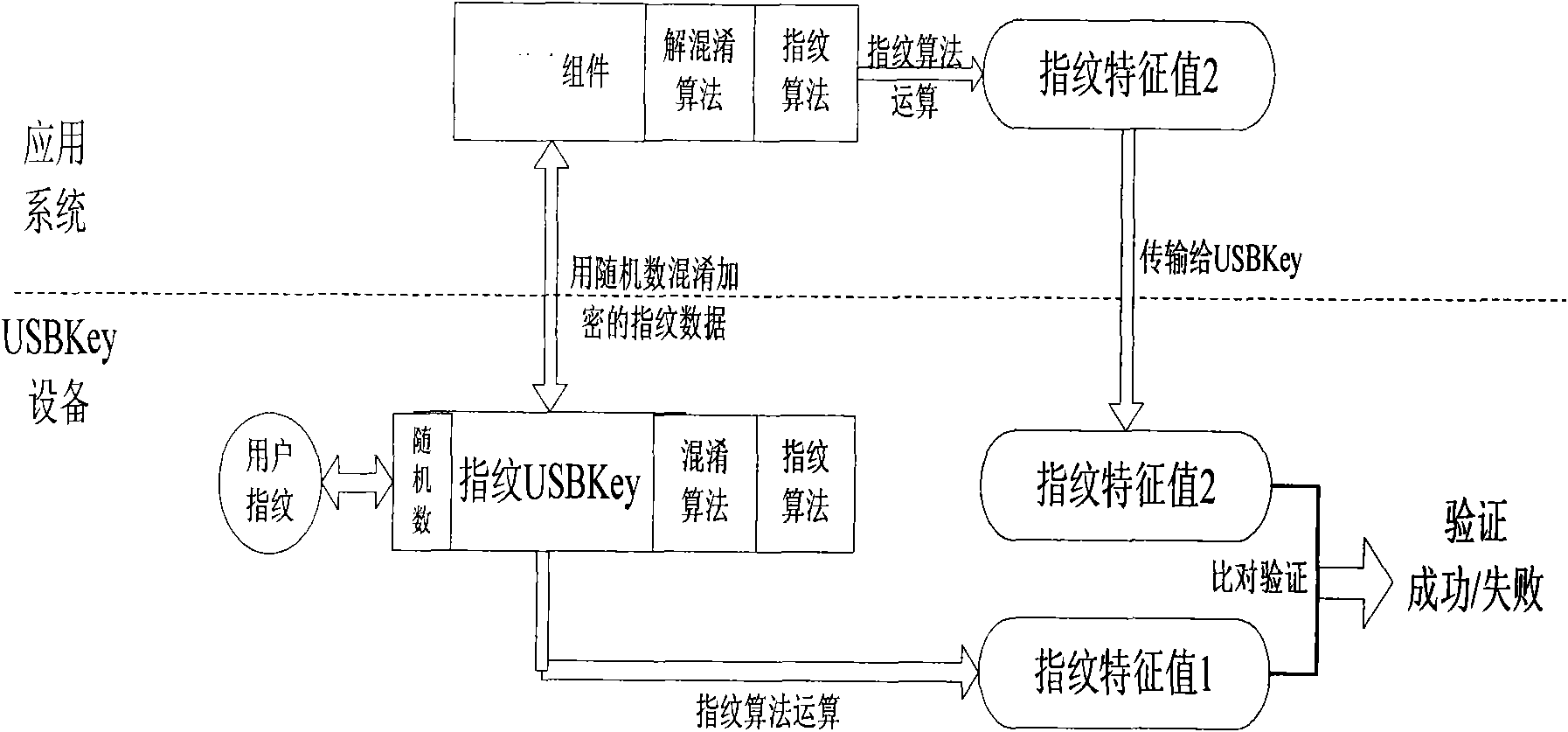
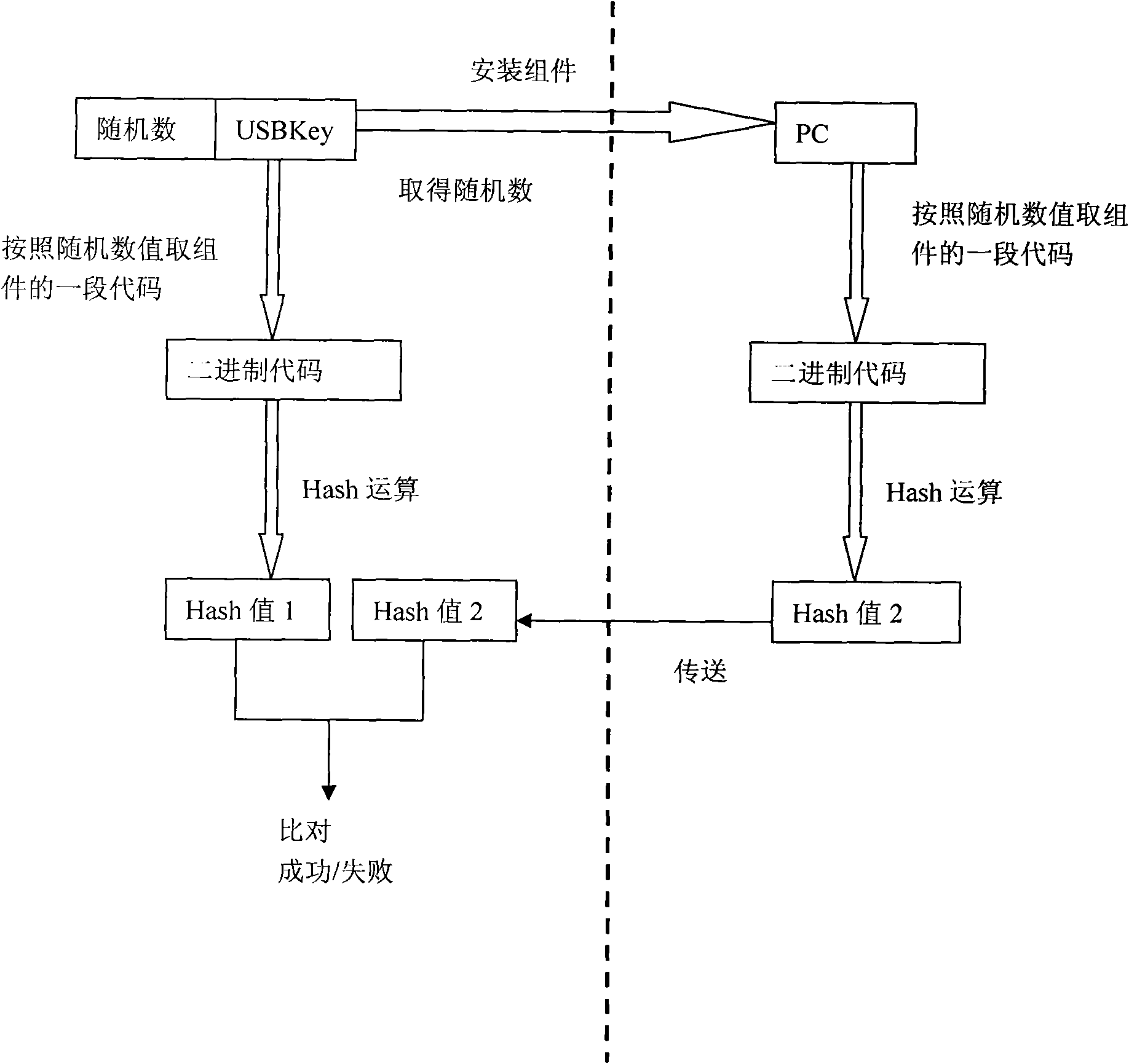
[0036] When leaving the factory, there is software (or components) used for signature authentication of online banking transactions stored inside the device. By binding the software (or components) with the device and using the shared key method, the system software is legalized when it is applied. certification, so as to ensure that the data received by the device comes from legal system software.
[0037] First of all, when the device leaves the factory, the system software has been stored in the secure storage space of the device, and the system software has a fingerprint algorithm and obfuscation key shared with the device, and al...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com