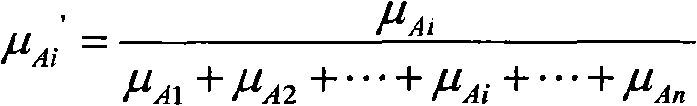Identity-based wireless sensor network security trust method
A wireless sensor and network security technology, applied in wireless communication, security devices, network topology, etc., can solve problems such as poor network operability, no multi-hop operation and solutions, trust information without considering message security and authentication, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
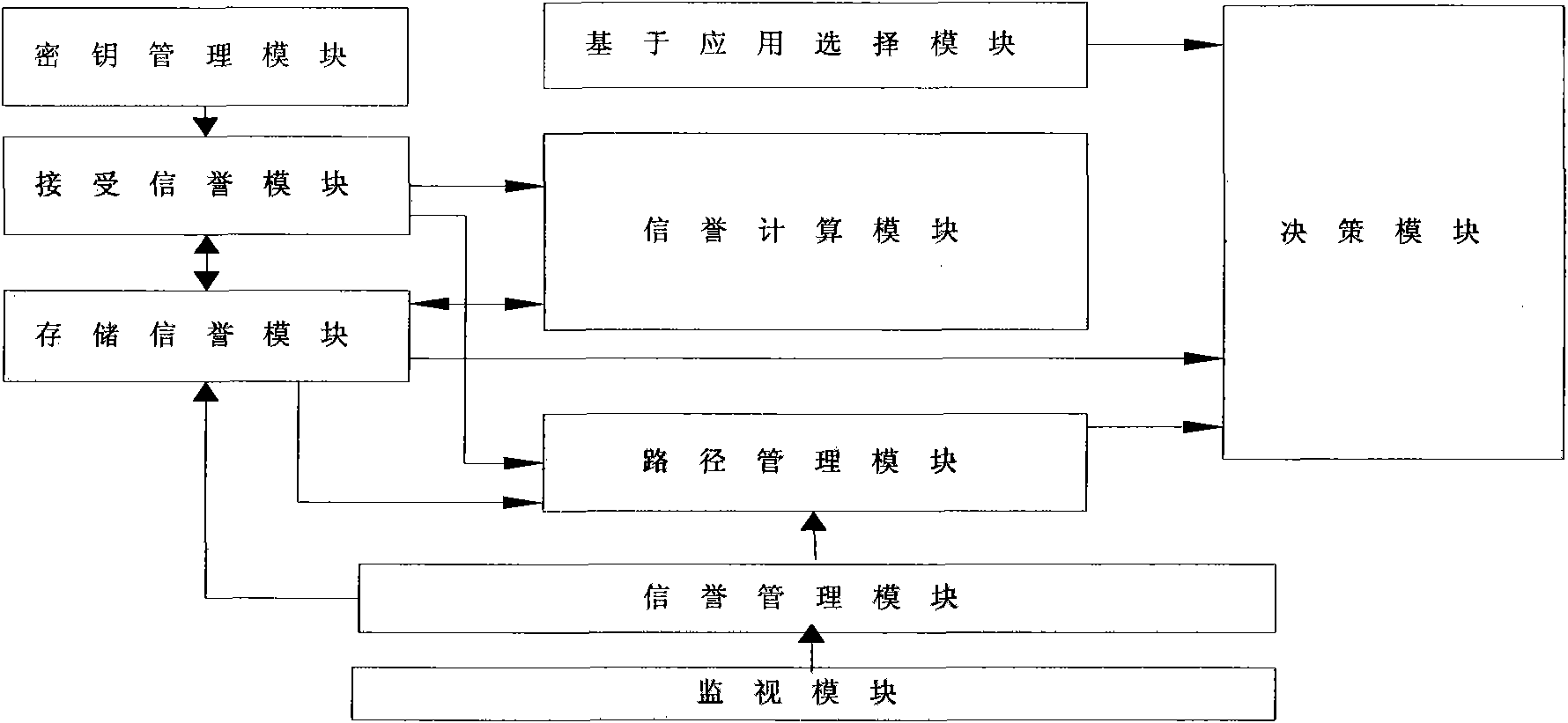
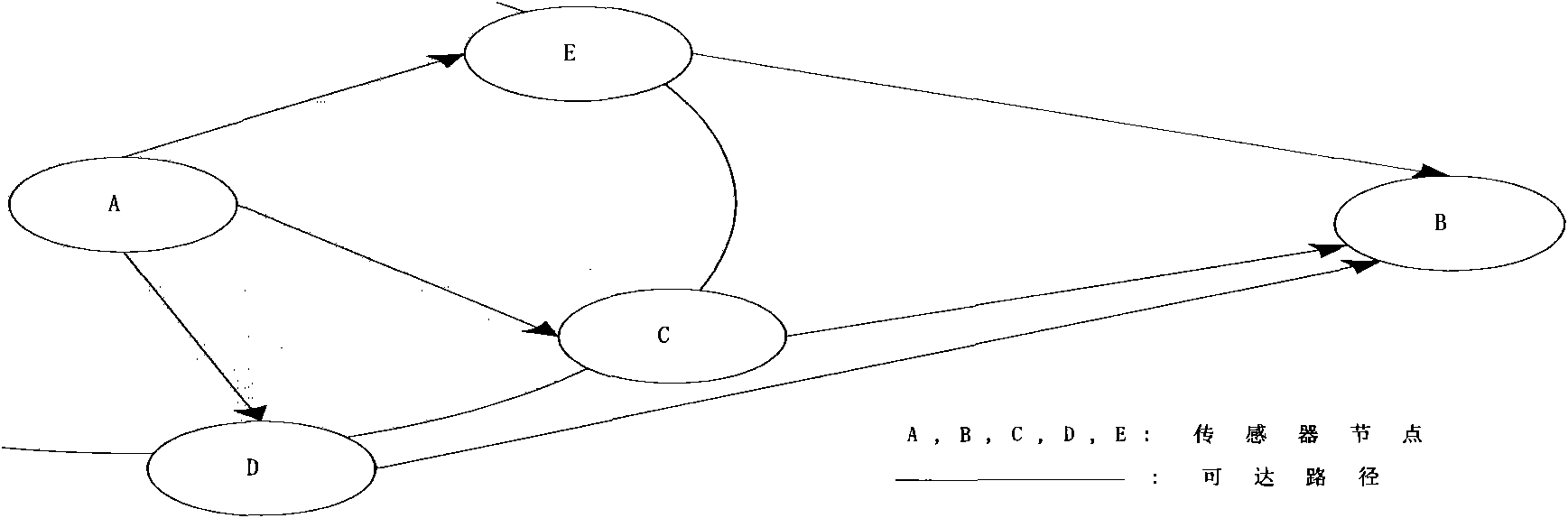
[0067] figure 2 The example topology structure of the identity-based wireless sensor network of the present invention is given, combined with figure 2 An implementation example of the topological structure, describing the working process of establishing a trust system;
[0068] 1. Build a network of trust
[0069] All nodes broadcast their IDs to surrounding neighbor nodes i , the node receiving the information knows the identity of its neighbor node, and uses its own private key and the identity of the neighbor node to calculate the shared key K ij Stored in the key management module, the node only saves the reputation of its neighbor nodes within one hop range;
[0070] In the first step, when node A tries to communicate with node B, it first broadcasts the information ID of the destination node B A ||ID B ;
[0071] In the second step, the next hop node of the neighbor nodes C, D, E of node A is the destination node B, then nodes C, D, E send query response informat...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com