Smart card and terminal capable of realizing machine card security authentication
A security authentication and smart card technology, applied in the field of smart cards and terminals, can solve the problems of inability to determine the party responsible for leakage, key leakage, damage to user terminals, etc., to improve the difficulty and cost of cracking, prevent key leakage, and ensure security. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
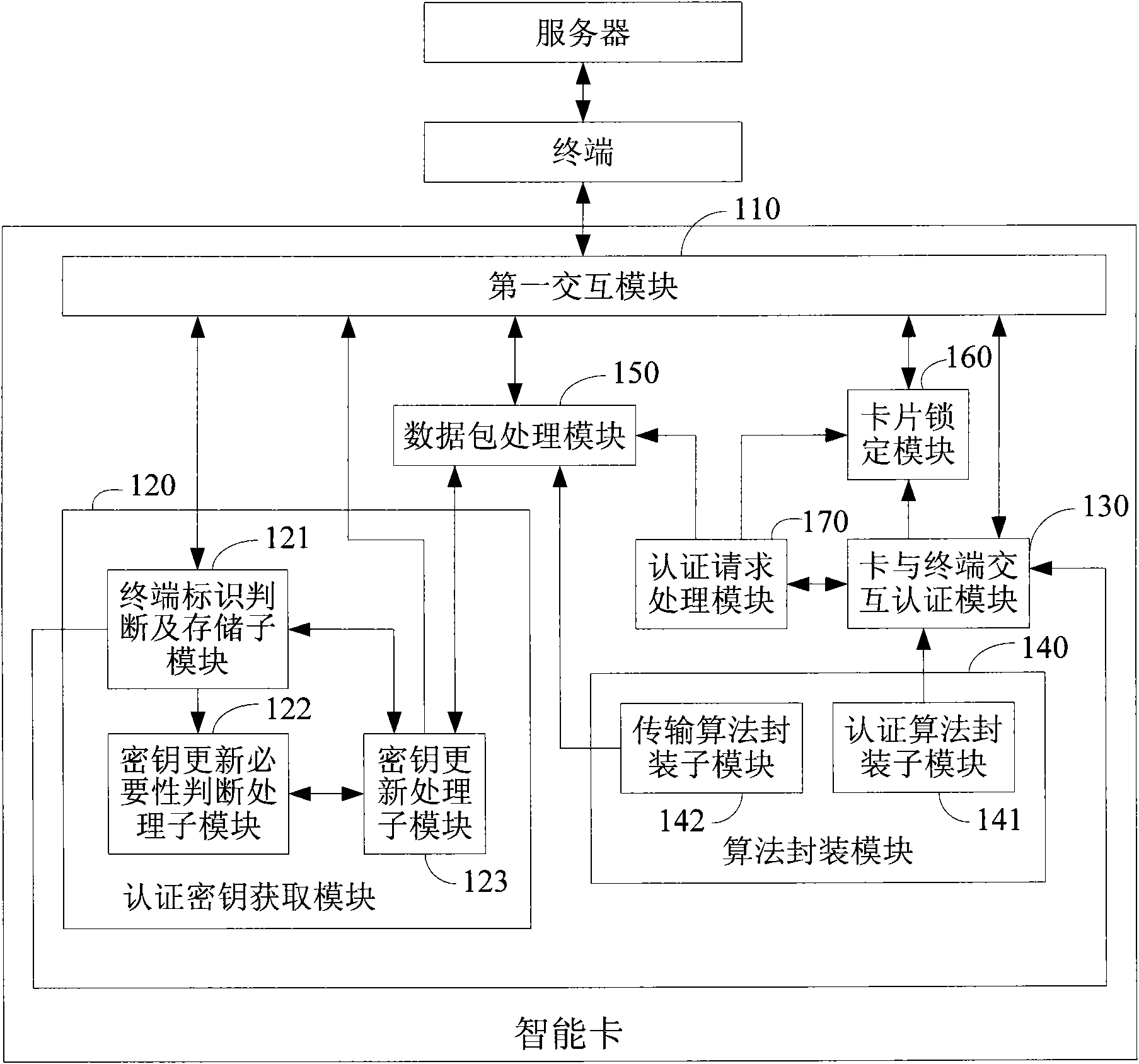
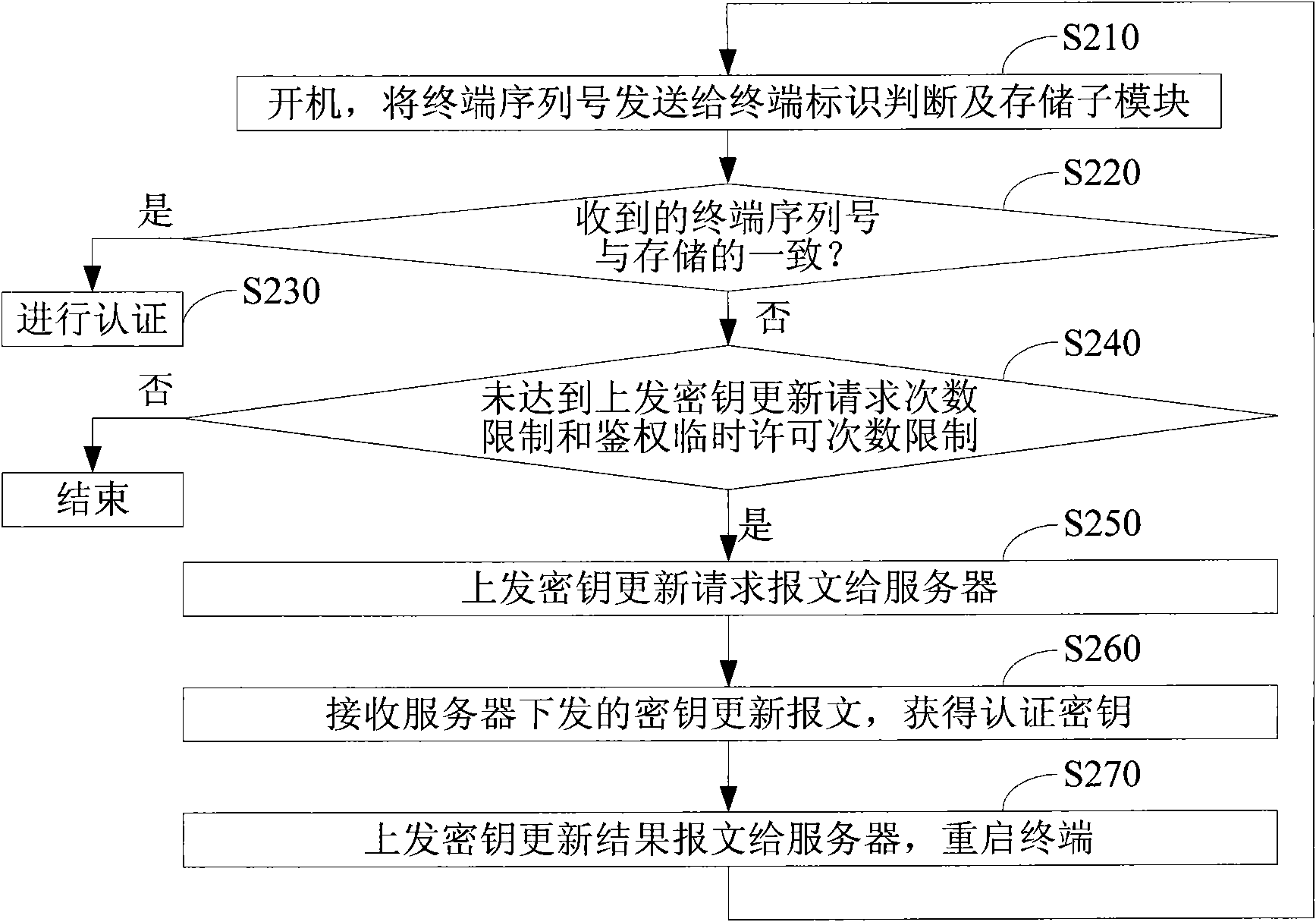
[0057] Embodiment 1, a kind of special-purpose smart card that can realize machine-card safety authentication, such as figure 1 As shown, in addition to supporting basic smart card COS and functional modules such as 2G or 3G authentication, SMS or GPRS BIP (these are not shown in the figure 1 Middle) and outside, there is a first interaction module 110 for interacting with the terminal; in order to support machine-card security authentication, an authentication key acquisition module 120, a card-terminal interaction authentication module 130, an algorithm encapsulation module 140, and a data packet processing module 150 are added , card locking module 160 and other new functional modules.
[0058] The first interaction module 110 is the main channel for data interaction between other modules in the card and the terminal. It can use SMS interaction mode or GPRS BIP to exchange data with the server through the terminal, and is also used to communicate with the terminal through S...
Embodiment 2
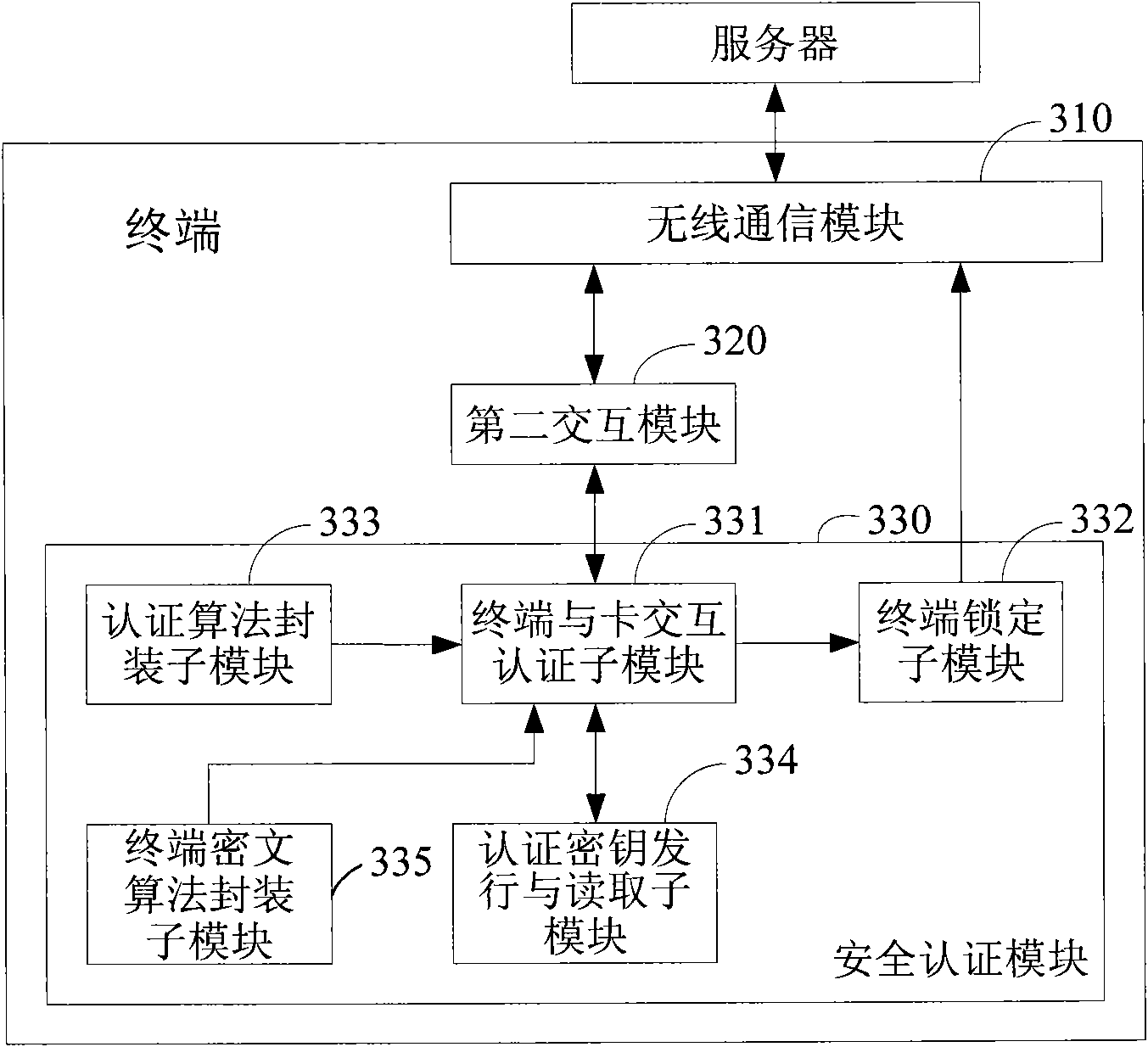
[0095] Embodiment 2, a terminal capable of implementing machine card security authentication, such as image 3 As shown, in addition to the commonly used wireless communication module 310 and the second interaction module 320 (such as the STK function processing module) for interacting with the card, a security authentication module 330 related to machine-card authentication is added.
[0096] The security authentication module 330 includes: a terminal-card interaction authentication submodule 331 , a terminal locking submodule 332 , an authentication algorithm packaging submodule 333 and an authentication key issuing and reading submodule 334 .
[0097] The wireless communication module 310 is used to enable the terminal to exchange data with the server through wireless communication methods such as SMS and GPRS.
[0098] The second interaction module 320 is a processing module for the terminal to support the STK command interaction function with the card. The incoming key u...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com