Memory encryption method, apparatus and system
An encrypted storage and storage module technology, applied in the storage field, can solve problems such as security, ciphertext cannot be decrypted, hidden dangers, etc., and achieve the effect of security protection and security sharing
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
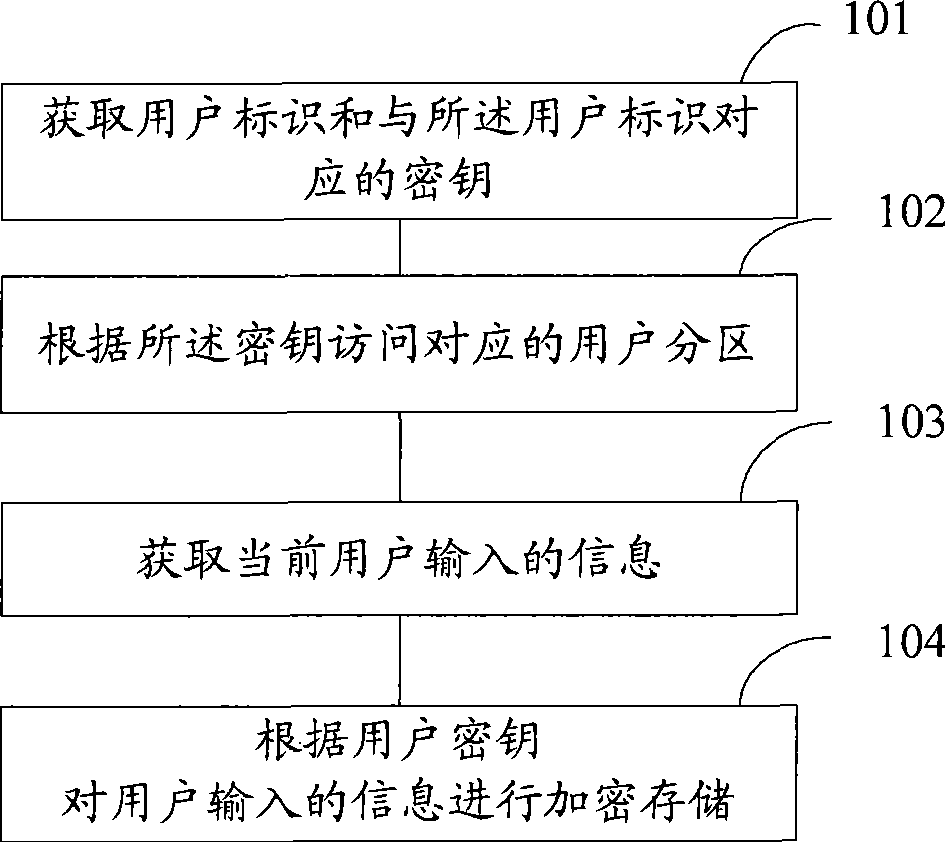
[0026] see figure 1 It is a flowchart of an encrypted storage method according to an embodiment of the present invention;
[0027] Step 101. Obtain a user ID and a key corresponding to the user ID;
[0028] In the embodiment of the present invention, the storage unit is divided into multiple user partitions, each user partition corresponds to a user ID, and each user ID corresponds to a key, that is, each user partition can use a different key to encrypt the stored data or decrypt.
[0029] When the storage unit needs to be read and written, the user ID of the current user is first obtained, and the corresponding key is obtained according to the user ID, and the storage unit can be read and written using the user’s key, for example, the input plaintext information Write it into the storage unit to become ciphertext, or read and encrypt the ciphertext stored in the storage unit to obtain plaintext data.
[0030] Further, when the user ID is obtained, but the key correspondin...
Embodiment 2
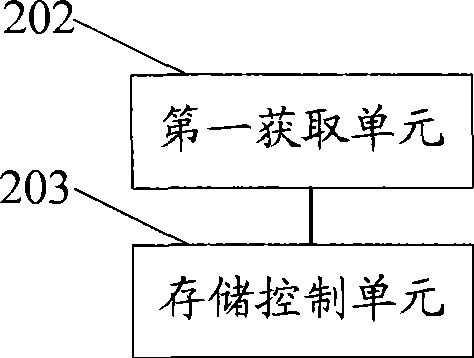
[0049] see figure 2 It is a structural diagram of an encrypted storage device according to an embodiment of the present invention;
[0050] The first acquiring unit 202 is configured to acquire a user identifier and a key corresponding to the user identifier;
[0051] After the first acquiring unit 202 acquires the user identifier, it acquires a corresponding key according to the user identifier.
[0052] The storage control unit 203 is configured to access the user partition corresponding to the user identifier according to the key.
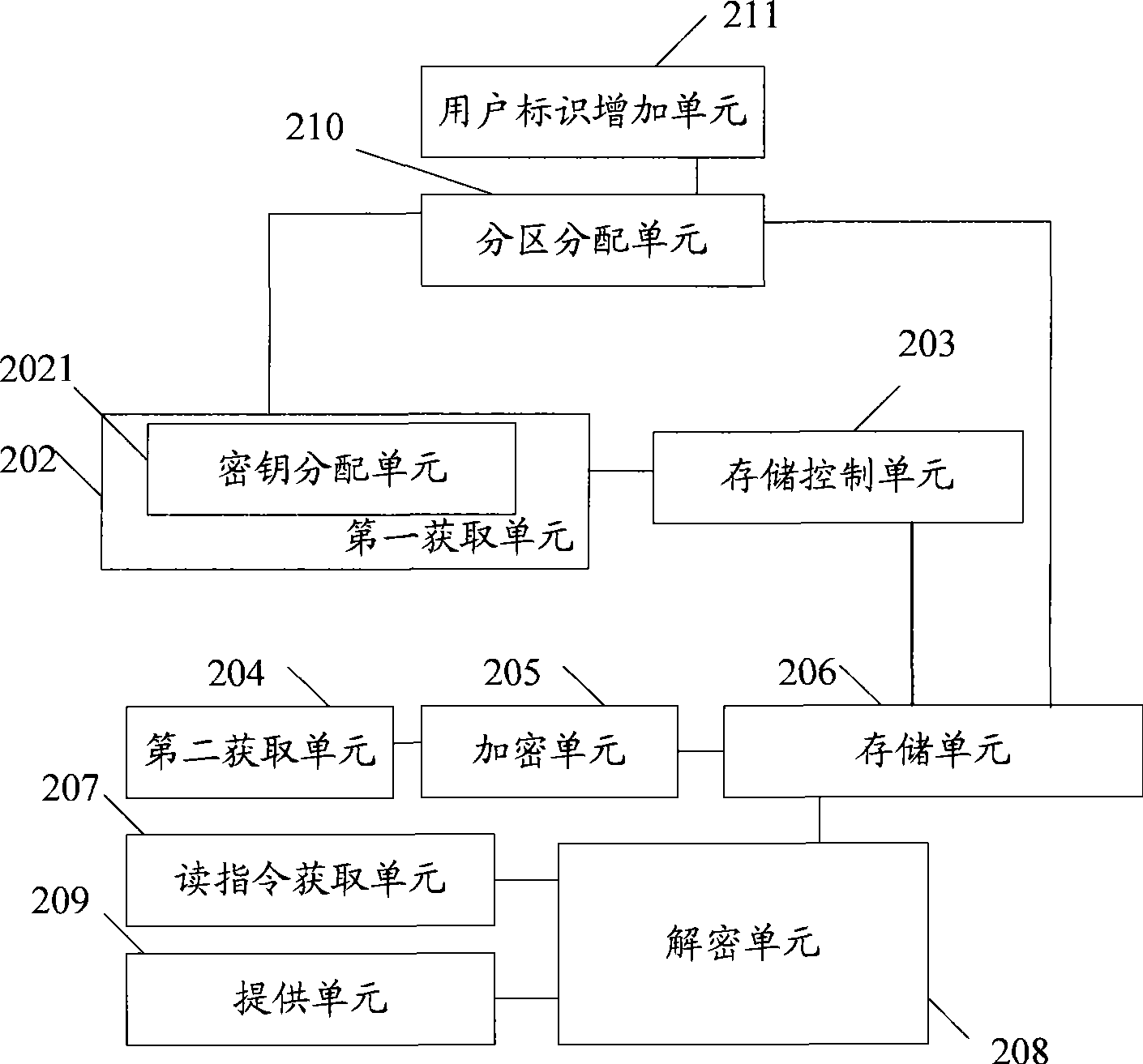
[0053] see image 3 , the first acquisition unit 202 may include:
[0054] The key allocation unit 2021 is configured to allocate a key to the current user when the user ID has not allocated a key.
[0055] After the user ID is obtained, if the user ID has not been assigned a key, a key may be assigned to the user ID, which is equivalent to assigning a key to a new user.
[0056] If data needs to be written and encrypted, the device may al...
Embodiment 3
[0070] see Figure 4 It is a structural diagram of a data processing system of the present invention;
[0071] The host 401 is configured to send a read operation request or a write operation request to the control module;
[0072] The storage module 402 is used to store user data, and the storage module includes multiple user partitions, each partition corresponds to a user ID, and each user ID corresponds to a key.
[0073] The control module 403 is configured to receive the read operation request after obtaining the user ID of the current user and the key corresponding to the user ID, and access the corresponding user partition according to the key, and use the current user's key to key to encrypt the input information of the current user and store it in the current user partition of the storage module, or,
[0074] The write operation request is received, the data requested by the current user is obtained from the current user partition of the storage module, and the obt...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com