Wireless mesh network access security authentication method based on WLAN
A security authentication and network access technology, applied in the fields of access security authentication and wireless mesh network access security authentication, it can solve problems such as feasibility doubts, authentication failures, and reduced network performance to ensure compatibility and flexibility. The effect of stability, ease of implementation, and good compatibility
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
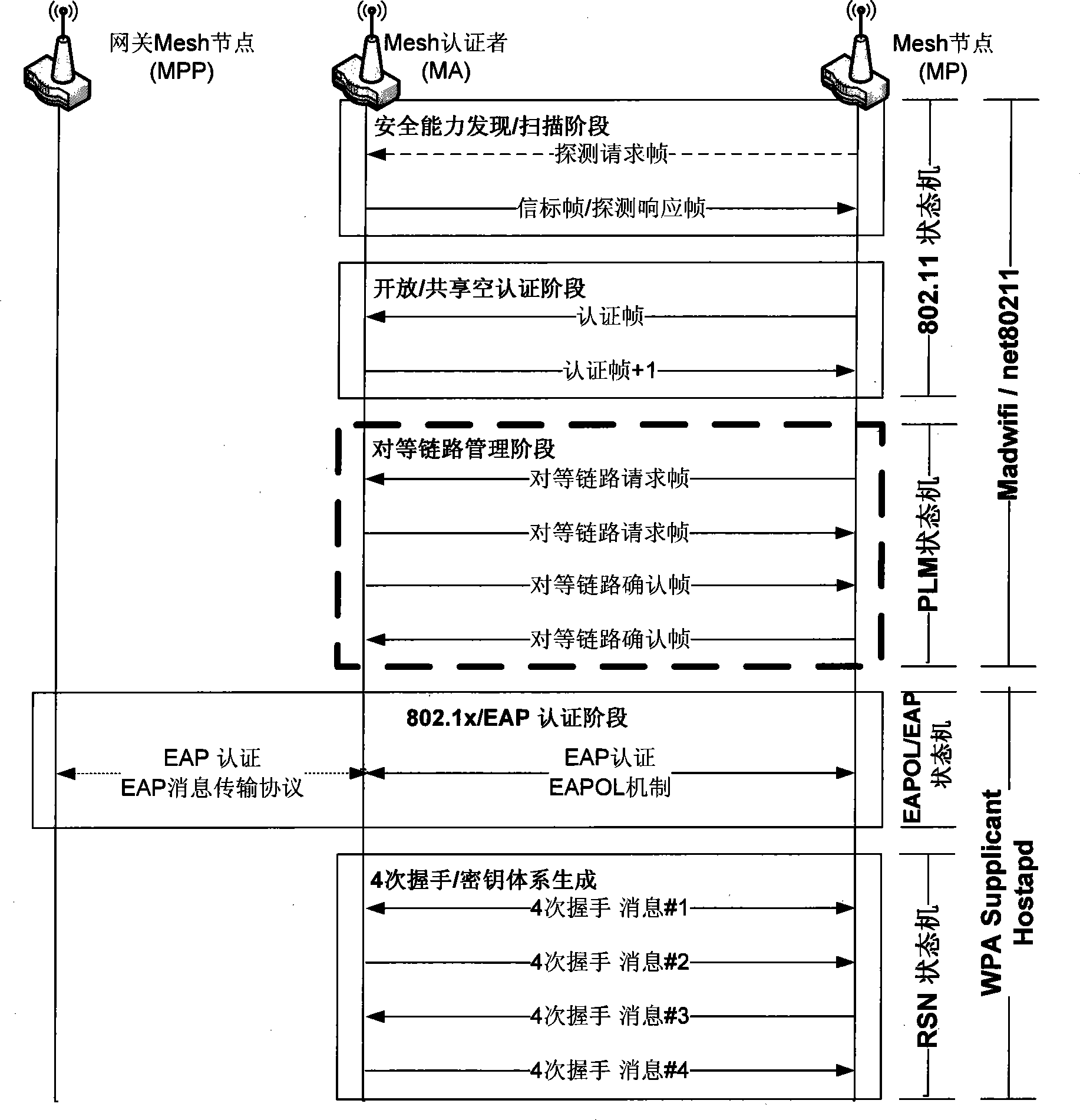
[0022] The embodiments of the present invention are described in detail below in conjunction with the accompanying drawings: this embodiment is implemented on the premise of the technical solution of the present invention, and detailed implementation methods and specific operating procedures are provided, but the protection scope of the present invention is not limited to the following the described embodiment.
[0023] In this embodiment, a new node MP joins the network and authenticates with a Mesh node MA with authentication capability as an example:
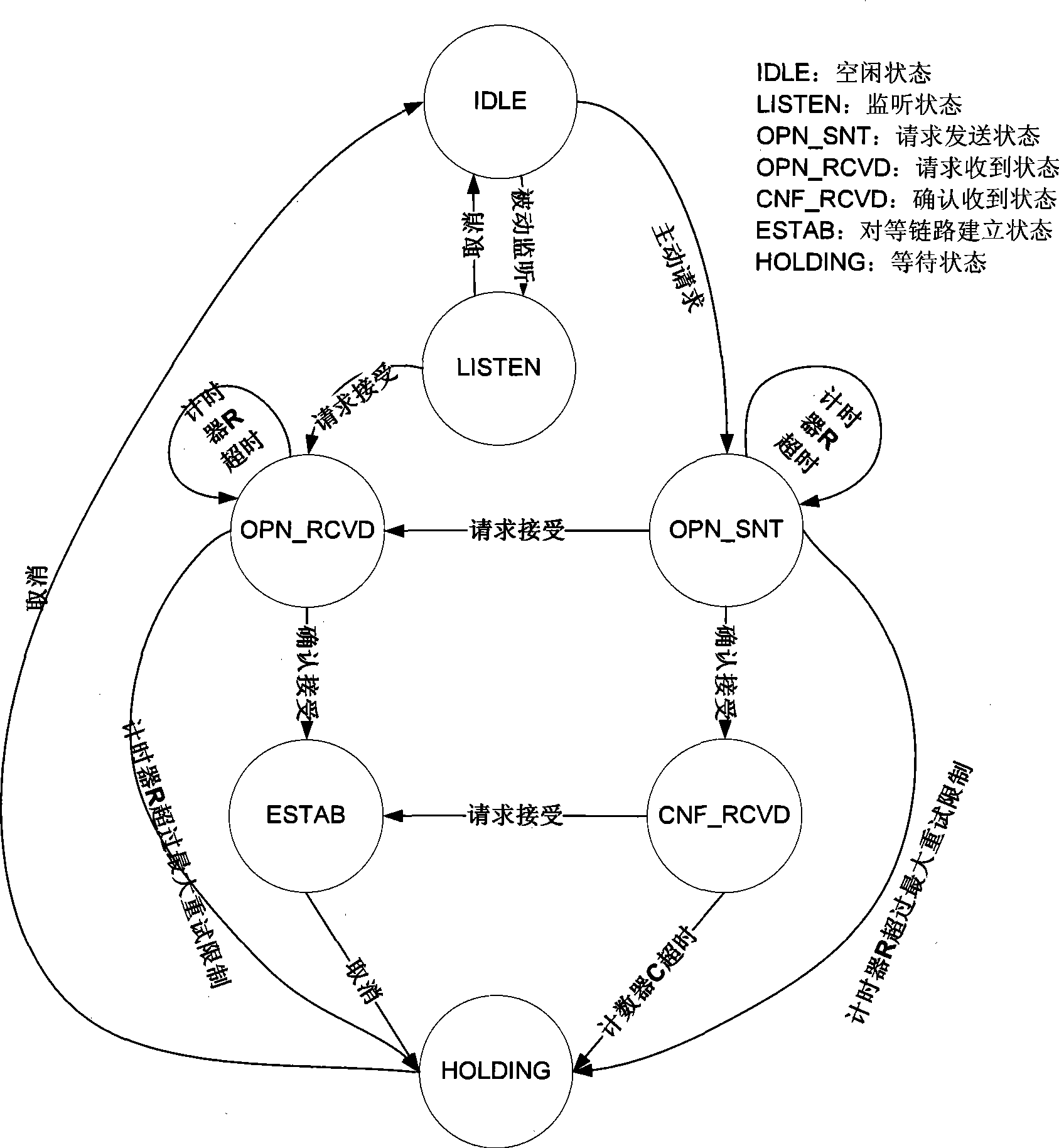
[0024] The first step is to initialize the MSA related parameters, data structure and PLM state machine while the Madwifi driver is initialized.
[0025] The MSA parameter is an extension of the RSN parameter in 802.11i, including whether to use the MSA function, whether to require EAP authentication, supported EAP methods, and so on. It can be roughly divided into two types determined by configuration and dynamically determ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com