Method for implementing secured electronic charging
An electronic payment and security technology, applied in payment architecture, instruments, data processing applications, etc., can solve the problems of being stolen and lost, and achieve the effect of increasing security and easy operation
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
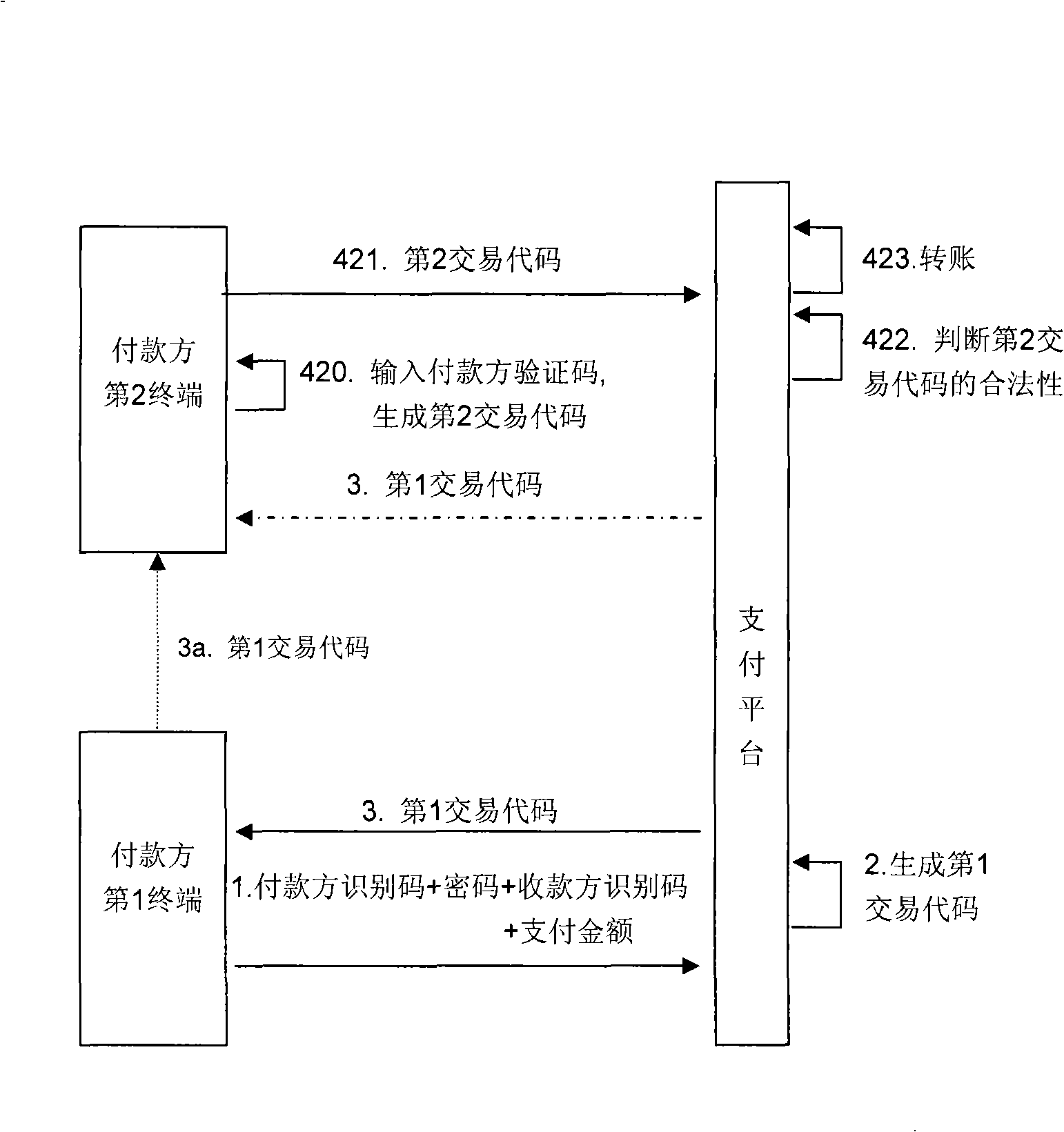
[0081] Such as figure 1 It is a flow chart of an embodiment of transfer based on the second transaction code;
[0082] In the payment platform, store the payer identification code and the payer verification code and establish an association between them;
[0083] When the payer makes payment to the payee, the following steps are included:
[0084] 1. On the payment platform, receive a signal from the first terminal of the payer, including the payer identification code, password, payee identification code and payment amount;
[0085] 2. In the payment platform, generate the first transaction code for the payment; and store the association between the payer identification code and the first transaction code;
[0086] 3. In the payment platform, send the first transaction code to the first terminal of the payer or the second terminal of the payer;
[0087] 3a. If the payment platform sends the first transaction code to the first terminal of the payer, then input the first tran...
Embodiment 2
[0093] Such as figure 2 It is a flow chart of the transfer embodiment based on the first transaction code and the payer verification code;
[0094] In the payment platform, store the payer identification code and the payer verification code and establish an association between them;
[0095] When the payer makes payment to the payee, the following steps are included:
[0096] 1. On the payment platform, receive a signal from the first terminal of the payer, including the payer identification code, password, payee identification code and payment amount;
[0097] 2. In the payment platform, generate the first transaction code for the payment; store the association between the payer identification code and the first transaction code;
[0098] 3. In the payment platform, send the first transaction code to the first terminal of the payer or the second terminal of the payer;
[0099] 3a. If the payment platform sends the first transaction code to the first terminal of the payer,...
Embodiment 3
[0105] image 3 It is a flow chart of an embodiment of a payment method based on the second transaction code with the participation of merchants;
[0106] In the payment platform, store the payer identification code and the payer verification code and establish an association between them;
[0107] 1. On the payment platform, receive a signal from the first terminal of the payer, including the payer identification code, password, payee identification code and payment amount;
[0108] 2. In the payment platform, generate the first transaction code for the payment; store the association between the payer identification code and the first transaction code;
[0109] 3. In the payment platform, send the first transaction code to the first terminal of the payer or the second terminal of the payer;
[0110] 3a. If the payment platform sends the first transaction code to the first terminal of the payer, you need to input the first transaction code into the second terminal of the pay...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com