Method for identification authentication of IPv6 broadcast source and inhibiting attack of malice/non-malice service
A technology of identity authentication and multicast source, applied in branch offices providing special services, data exchange details, digital transmission systems, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
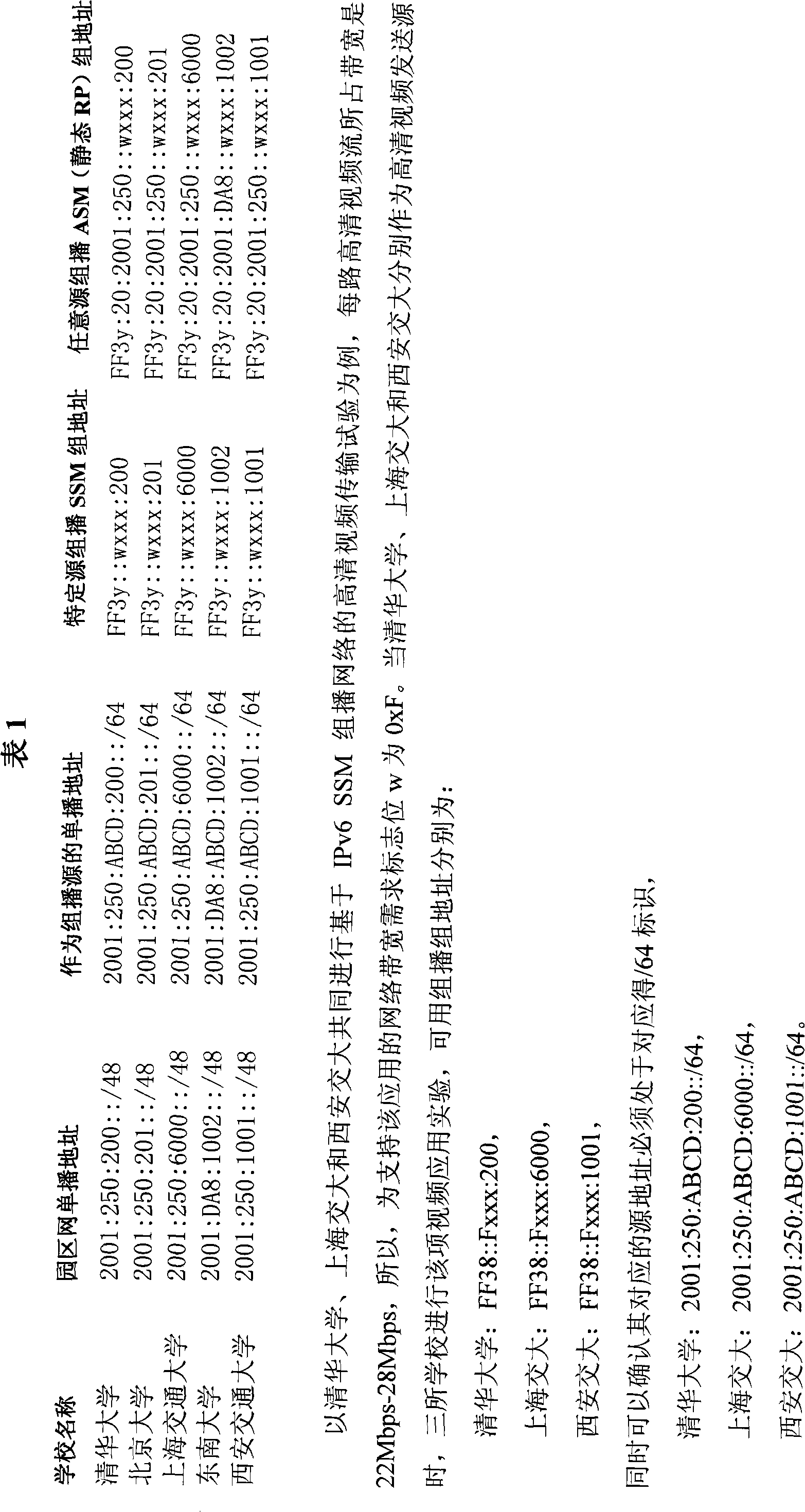
[0044] On CNGI-CERNET2, according to the above definition method, taking Tsinghua University, Peking University, Shanghai Jiaotong University, Southeast University, Xi'an Jiaotong University as an example, the campus network users of each school are assigned specific source multicast and arbitrary source multicast ( The static RP) group address scheme is shown in Table 1:
[0045]
[0046] The example of controlling the source address of Tsinghua University, Shanghai Jiaotong University, and Xi’an Jiaotong University multicast streams on the Cisco (CISCO) router is as follows:
[0047] ipv6 access-list multicast-source permit 2001:250:ABCD:200:: / 64 FF38:0:0:0:0:0:F000:: / 100
[0048] ipv6 access-list multicast-source deny any FF00:: / 8
[0049] The control configuration example of the source address of the Shanghai Jiaotong University multicast stream on the Cisco (CISCO) router is as follows:
[0050] ipv6 access-list multicast-source permit 2001:250:ABCD:6000:: / 64FF38:0:0...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com