Method for insulating inside and outside networks, authentication server and access switch
An access switch and authentication server technology, applied in the field of network access control, can solve the problems of doubling the maintenance workload, increasing the terminal cost, complex network topology, etc., achieving the effect of low management and maintenance difficulty, reduced equipment cost, and simple network topology
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
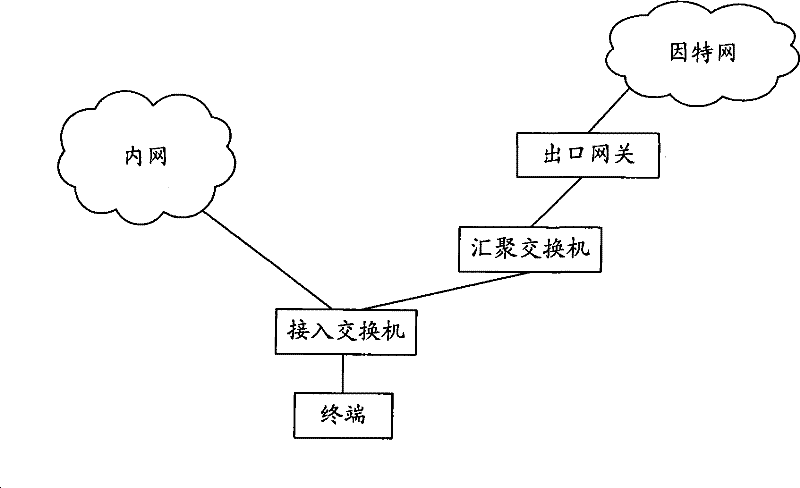
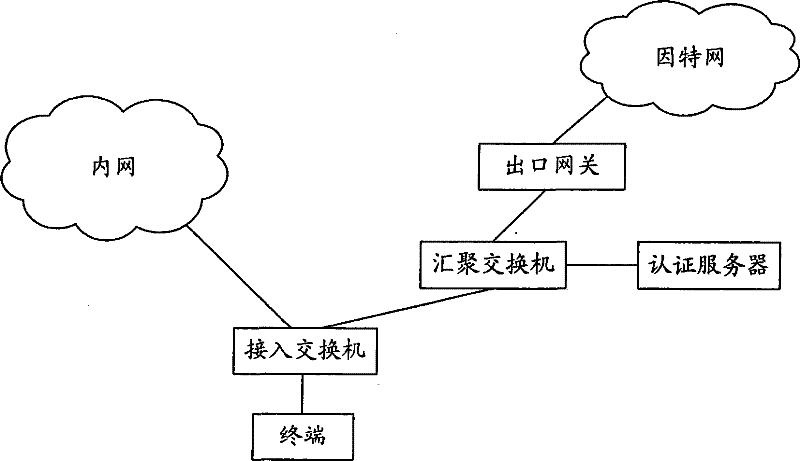
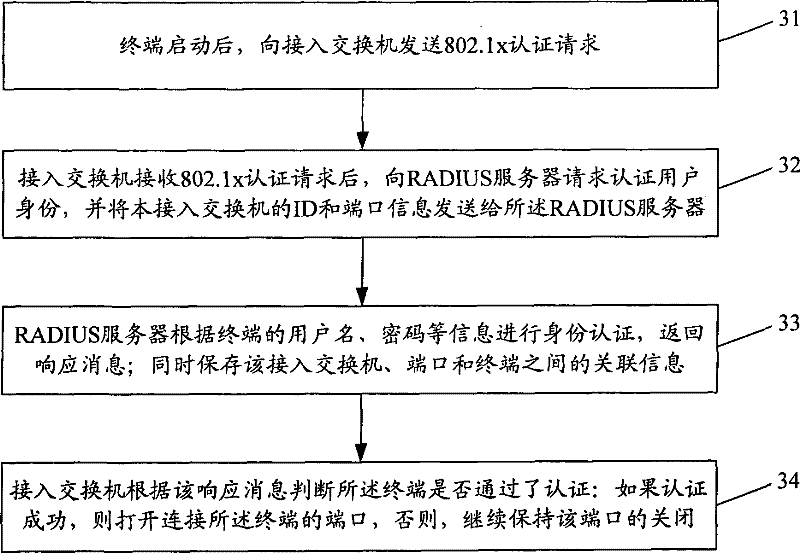
[0054] figure 2 It is a schematic diagram of an application environment of the method for isolating internal and external networks described in this embodiment. figure 2 In this method, the terminal is connected to the intranet through an access switch, specifically, the terminal is connected to a port on the access switch. At the same time, the access switch is also connected to the Internet through the egress gateway. An aggregation switch may also be connected between the access switch and the egress gateway, and the aggregation switch is connected to an authentication server. Specifically, the authentication server may be a Remote Authentication Dial-In User Service (RADIUS, Remote Authentication Dial-In User Service) server or a Terminal Access Controller Access Control System (TACACS, Terminal Access Controller Access Control System) server. In this embodiment, the RADIUS server is taken as an example for illustration, and the implementation principles of authenticat...
Embodiment 2
[0095]In Embodiment 1, the terminal needs to pass 802.1x authentication to access the intranet, which can improve the security of intranet access and prevent unauthorized terminals from accessing intranet resources. Portal authentication is required for terminals to access the extranet to prohibit unauthorized users from accessing the extranet. In this embodiment, identity authentication is not performed for the terminal to access the internal network, that is, the terminal can access and access the internal network after startup. For accessing the external network, similar to Embodiment 1, Portal authentication is required.
[0096] The method of isolating internal and external networks described in this embodiment is still applied in figure 2 environment shown. Described method specifically comprises the following steps:
[0097] Step S81, pre-configure and save the association information between the terminal in the intranet, the access switch connected to the terminal, ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com