A load-independent method for detecting network abuse
A network and behavior technology, applied in data exchange networks, digital transmission systems, electrical components, etc., can solve problems such as large amount of calculation, large system resources, violation of user privacy, etc., and achieve the effect of small amount of calculation and less computing resources.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0045] The method for detecting network abuse based on traffic information of the present invention will be described in detail below with reference to the accompanying drawings, but the present invention is not limited to the following embodiments.
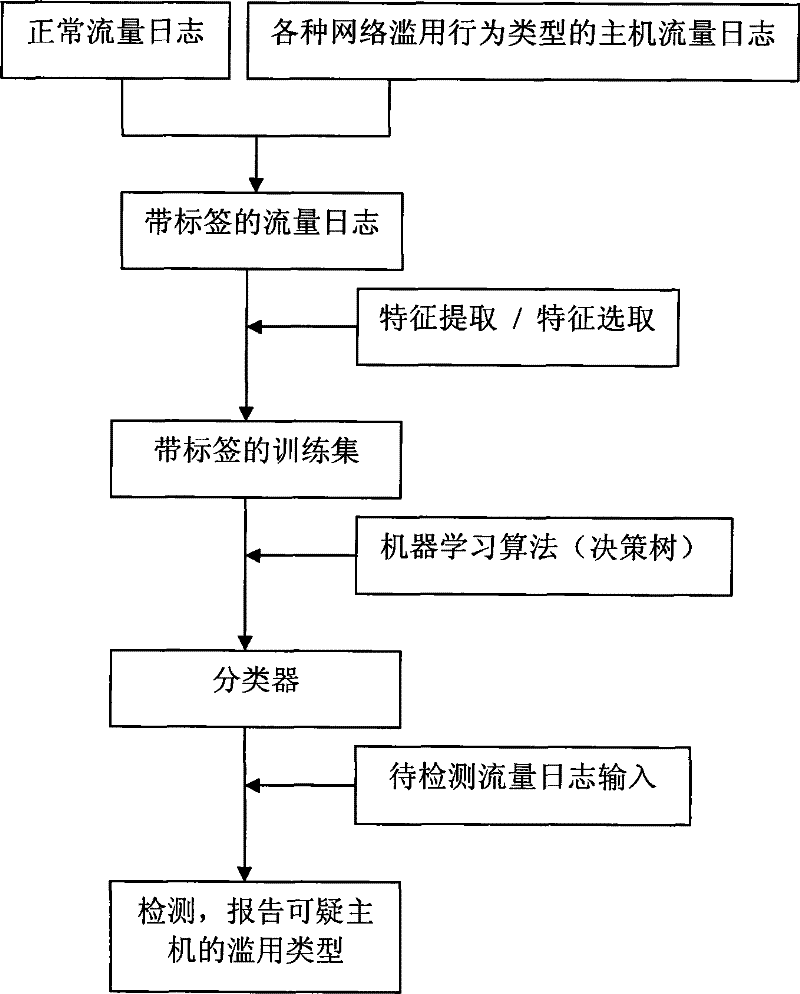
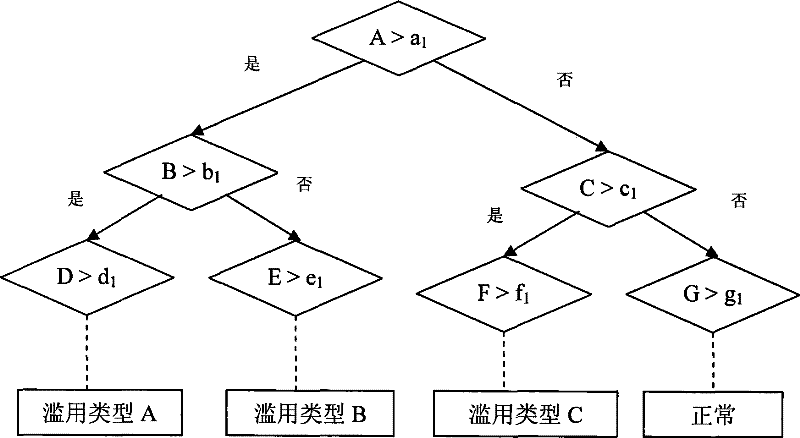
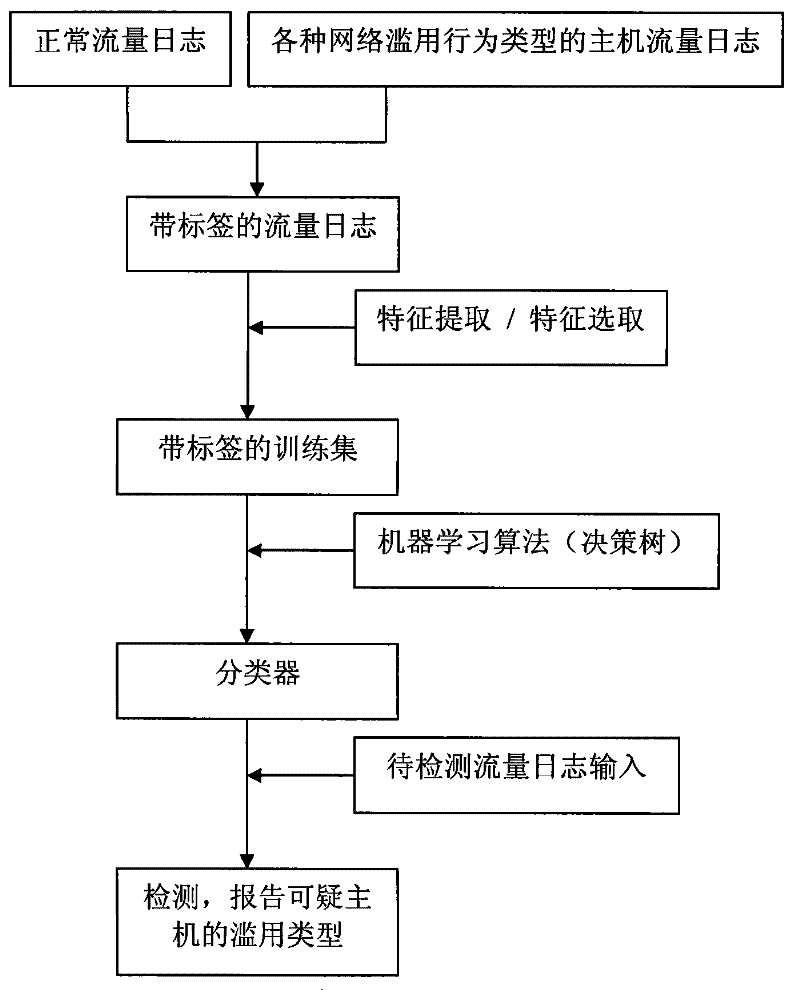
[0046] The flow process of the inventive method is as figure 1 As shown, its working process is as follows:
[0047] (1) Traffic log collection. Use gateway facilities such as firewalls to collect network traffic log information. This step includes two aspects of work, one is to collect normal traffic logs, and the other is to collect traffic logs of various types of network abuse behavior hosts. During the collection process, each type is marked with a type label, and then the normal traffic log and the traffic log with network abuse behavior are collected to form a traffic log information training set.
[0048] Sample traffic log:
[0049] 2007-10-19 00:00:04 Local7.Debug 172.31.4.44 id=firewall time="2007-10-19
[0050] 0...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com