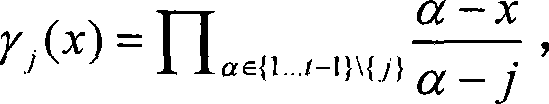Realizing method of general-purpose digital signing scheme
A digital signature and implementation method technology, applied in the field of information security, can solve problems such as unsatisfactory digital signature schemes and difficult implementation of threshold digital signature schemes, and achieve the effects of saving communication bandwidth, reducing signature length, and good scalability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
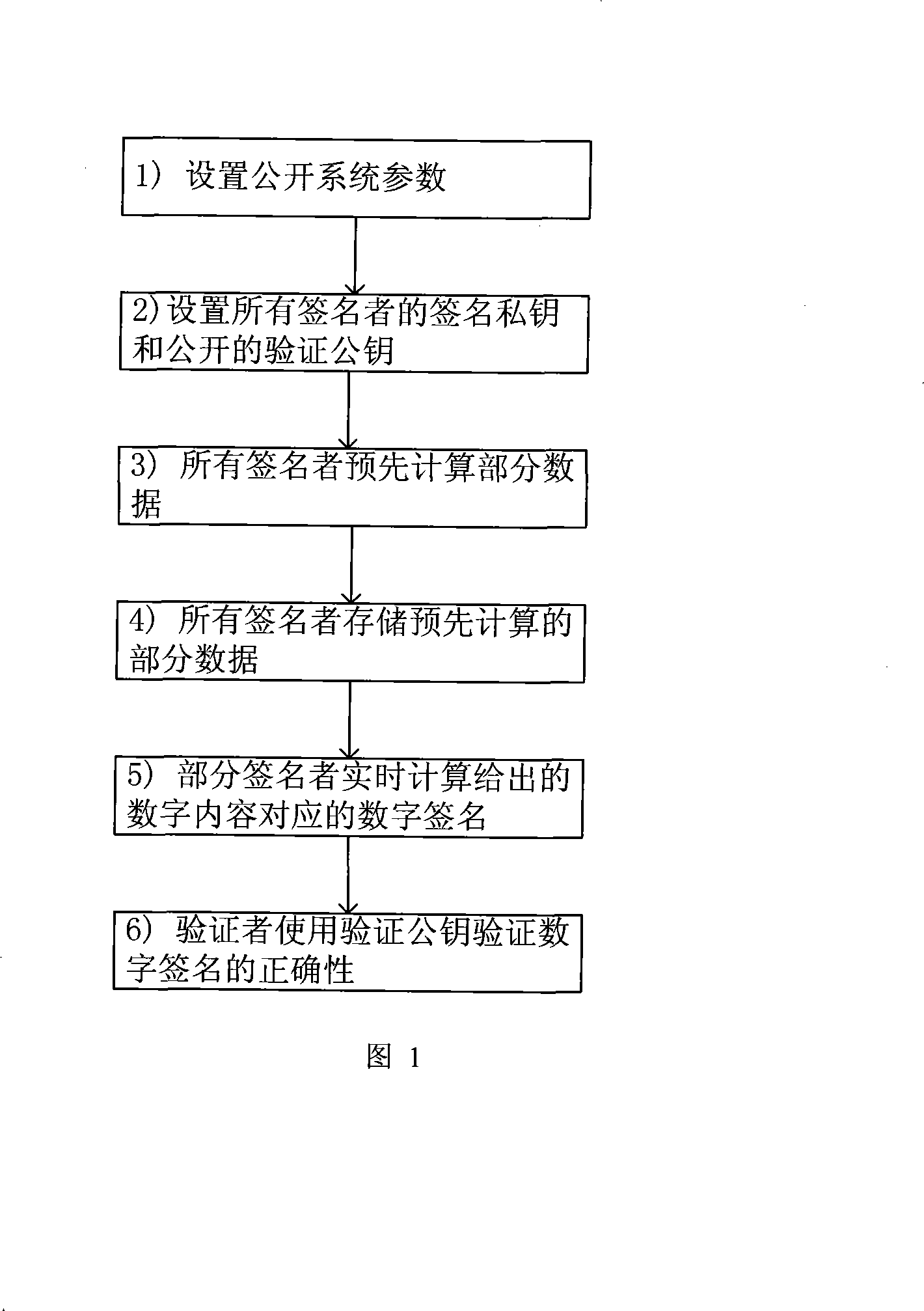
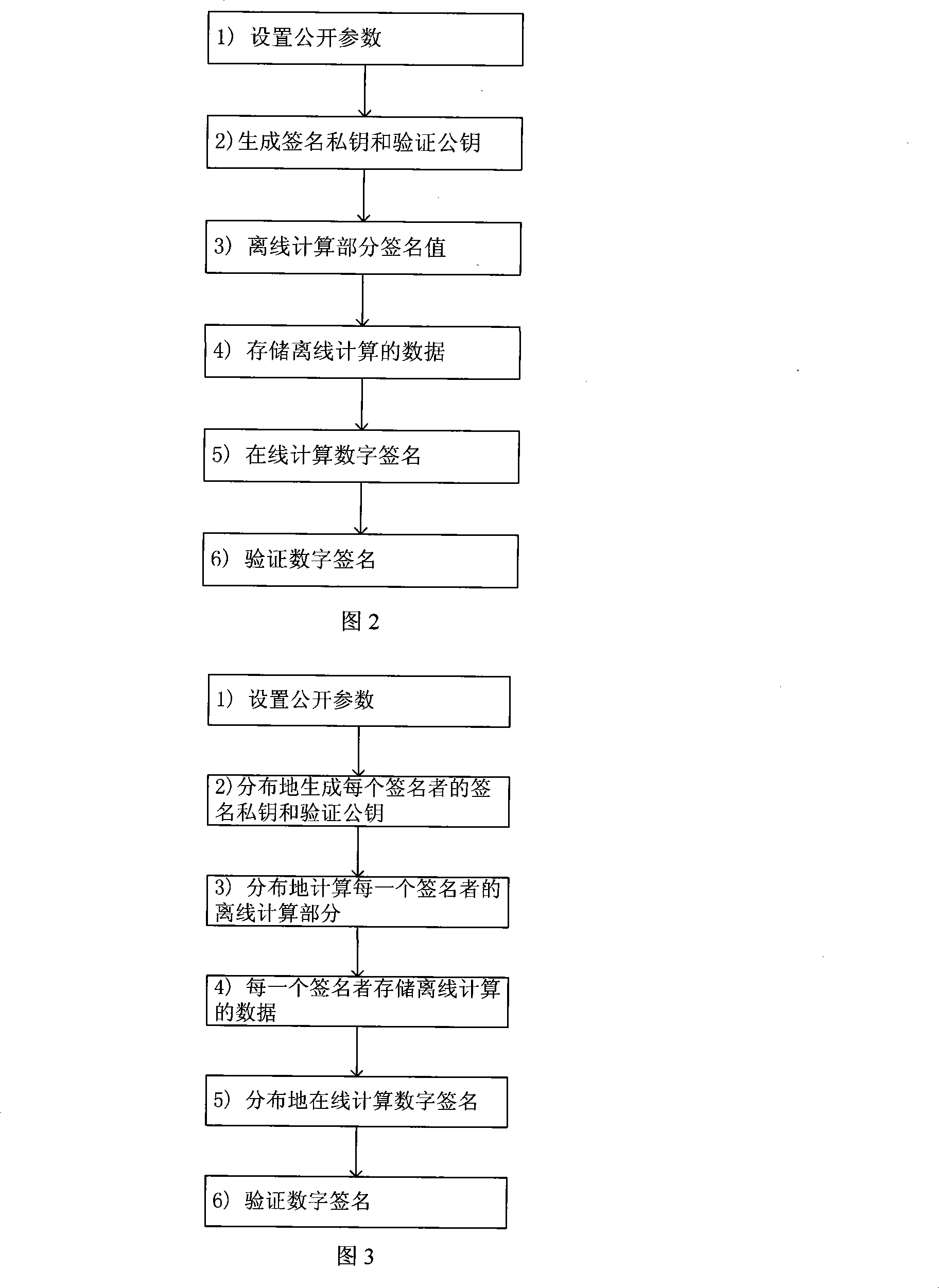
[0040] Taking the smart card as an example to illustrate the specific implementation of the digital signature scheme when n=1 and the safe storage area is 100 data pairs in the present invention.
[0041] 1. For the smart card implementing the digital signature scheme in the present invention, it is necessary to store the following public information {E, p, q, P, G, f, H, (JG, JS, JV), (VK, Y, h, σ) } and the following secret information {(SK, x, k * ), (k i , k i P), i ∈ {1...100}}
[0042] Among them, the public information (JG, JS, JV) is any provably secure digital signature algorithm, here selected as the Boneh-Lynn-Shacham short signature algorithm, the signature length is 160 bits, and the parameters of the signature algorithm (E, p, q, k, P, G) are suggested as follows:
[0043] E: y 2 =x 3 +3
[0044] Q=p=1461501624496790265145448589920785493717258890819
[0045] q=1461501624496790265145447380994971188499300027613
[0046] MOV degree k=12
[0047] P=(x,y)
...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com