Microprocessor system for controlling or regulating at least partly security-critical processes
A microprocessor and security technology, applied in response to error generation, hardware redundancy for data error detection, redundant code for error detection, etc., can solve problems such as non-symmetrical design of memory
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
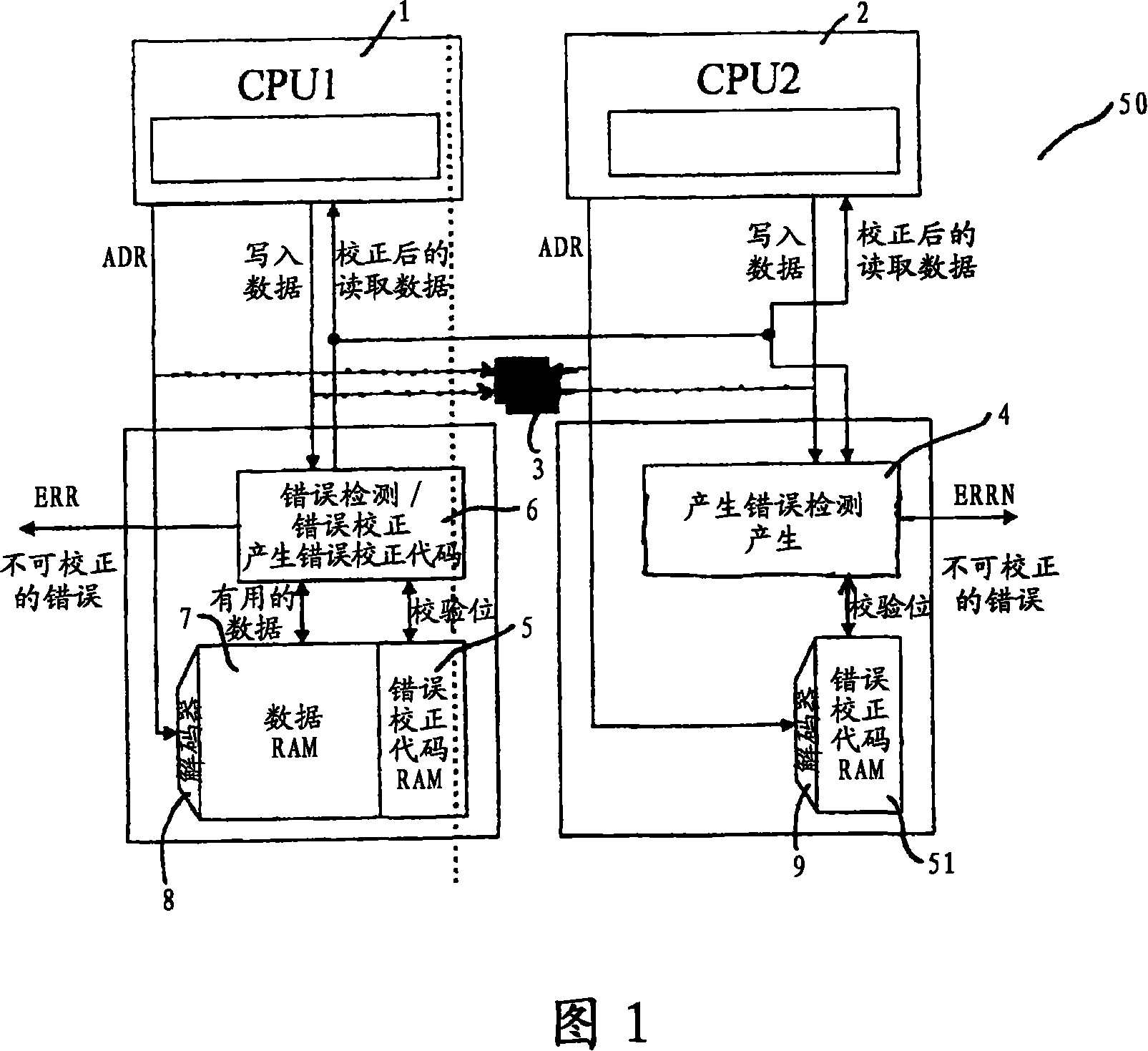
[0034] The microcontroller in Fig. 1 comprises two central processing units (CPUs) 1, 2, which operate in a clock-synchronized fashion. Both microcomputers execute the same program. Each unit has its own separate associated address and data bus. The CPU 1 has a full data storage 7 connected thereto, which is partially backed up using a test data storage 51 on the second bus. In addition, the microprocessor system contains a comparator 3 which takes the form of a hardware unit and is used to continuously compare the queued addresses and data on the two bus systems with each other. If there is a mismatch, an error signal is generated. For the purpose of simplifying the illustration, the figures do not show in more detail components that are typically found in a microprocessor system, such as input / output units, read-only memory, etc. These not shown components are essentially based on the redundant core microcontroller described in WO99 / 35543.
[0035] The test data storage ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com