Method for implementing subscriber terminal access control
A user terminal and access control technology, applied in the field of CDMA mobile communication, can solve the problems of reduced normalized throughput rate of access channels, reduced access success rate of user terminals, and reduced access reliability, etc., so as to improve access. Time slot length, the effect of improving access success rate and reducing transmission time
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
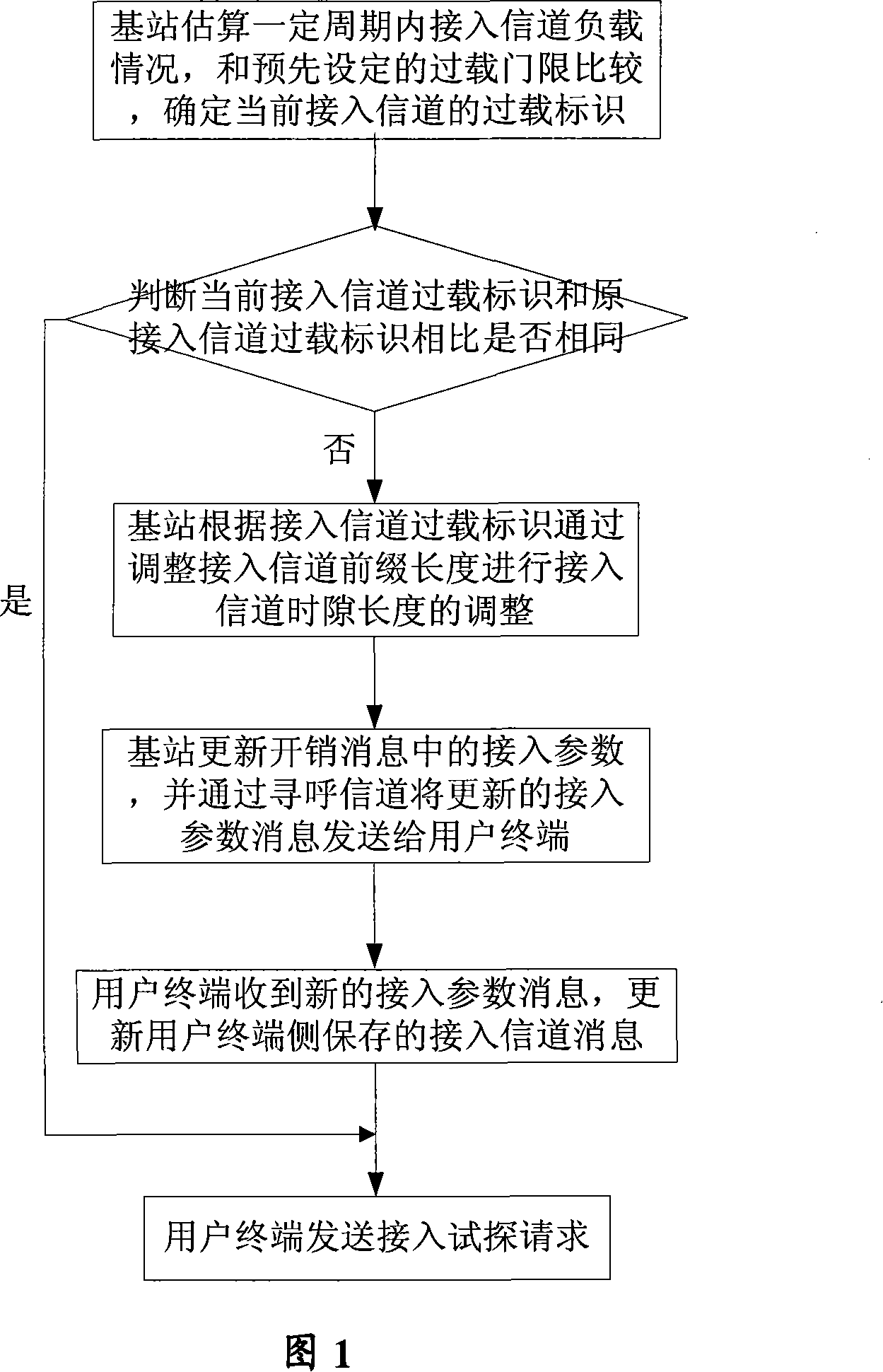
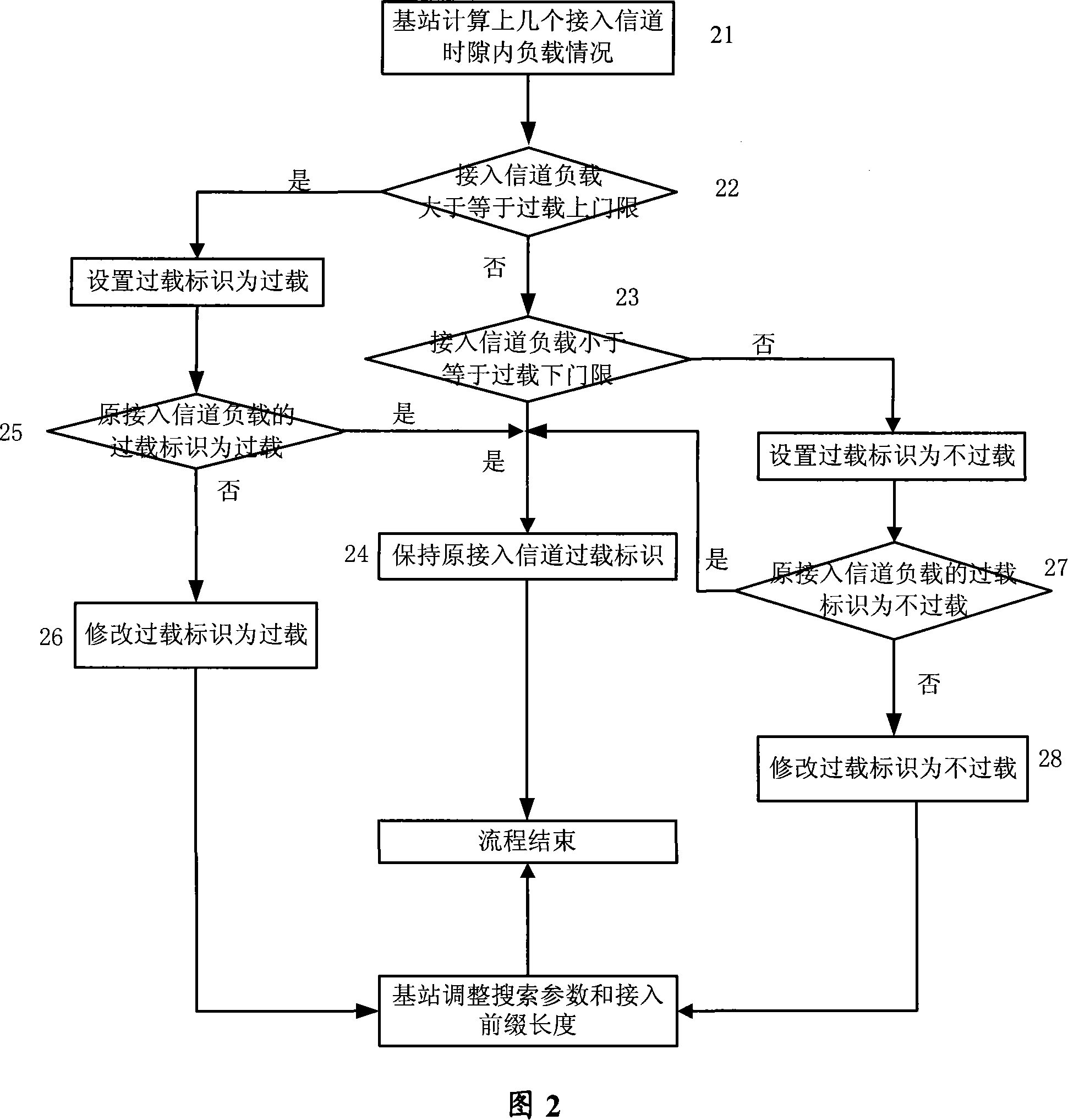
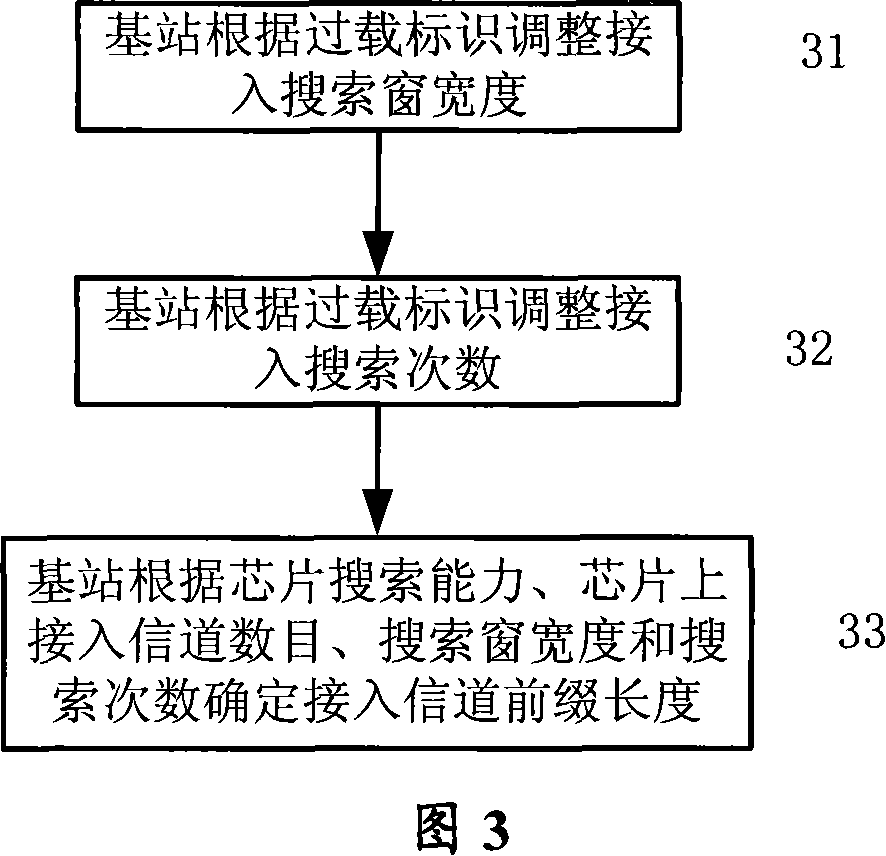
[0035] When using the ALOHA protocol, when the load of the access channel is constant, the probability of user terminal collision is proportional to the length of the access channel time slot. The shorter the length of the access channel time slot, the higher the probability of collision. On the contrary, when the length of the access channel time slot is longer, the probability of collision will be greater. Therefore, if the length of the access channel time slot can be dynamically adjusted according to the load of the access channel, the access channel can be reduced. The probability of access conflicts and improve the success rate of access.
[0036] When the access load is overloaded, the probability of user terminal collisions increases greatly, but when the access load is not overloaded, since the length of the access channel time slot is proportional to the ability of the base station to capture access channel messages, the longer the length of the access channel time sl...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com