A system and method for authorizing access request
An access request and accessed technology, applied in the transmission system, digital transmission system, data exchange details, etc., can solve the problem of cumbersome and inconvenient authorization operation, and achieve the effect of flexible operation
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
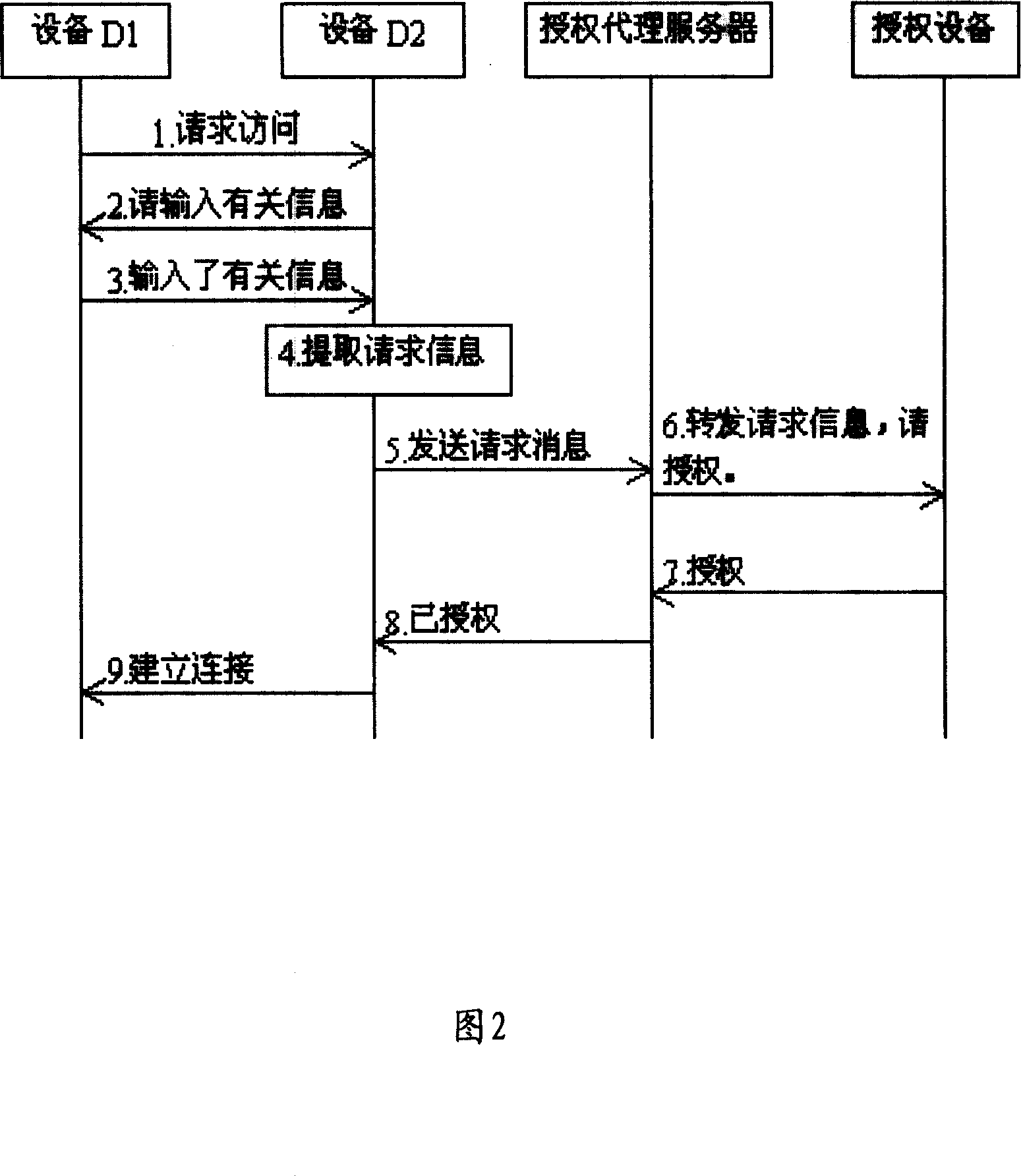
[0044] The core idea of the present invention is to forward the access request information and authorization information through the authorization proxy device, so as to achieve the purpose of temporarily authorizing the visitor during the access request, especially the remote access, and effectively overcome the problems existing in the prior art.
[0045] Firstly, the system of the present invention will be described in detail with reference to accompanying drawings 1 and 2 .
[0046] The system for authorizing an access request according to the present invention includes: at least one accessed device, an authorizing device and at least one authorized proxy server, and a connection request management module is set in the accessed device;
[0047] Connection request management module: responsible for obtaining access request information and sending it to the authorized proxy server;
[0048] That is, the connection request management module displays information such as serv...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com