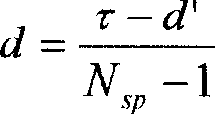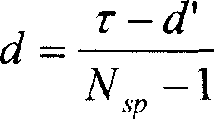Network security monitoring method based on the network life frequency spectrum
A network security and spectrum technology, applied in secure communication devices, data exchange networks, digital transmission systems, etc., can solve problems such as network unavailability, network congestion, and the inability of the network to provide normal services.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
[0084] The present invention will be described in detail below through specific embodiments and accompanying drawings.
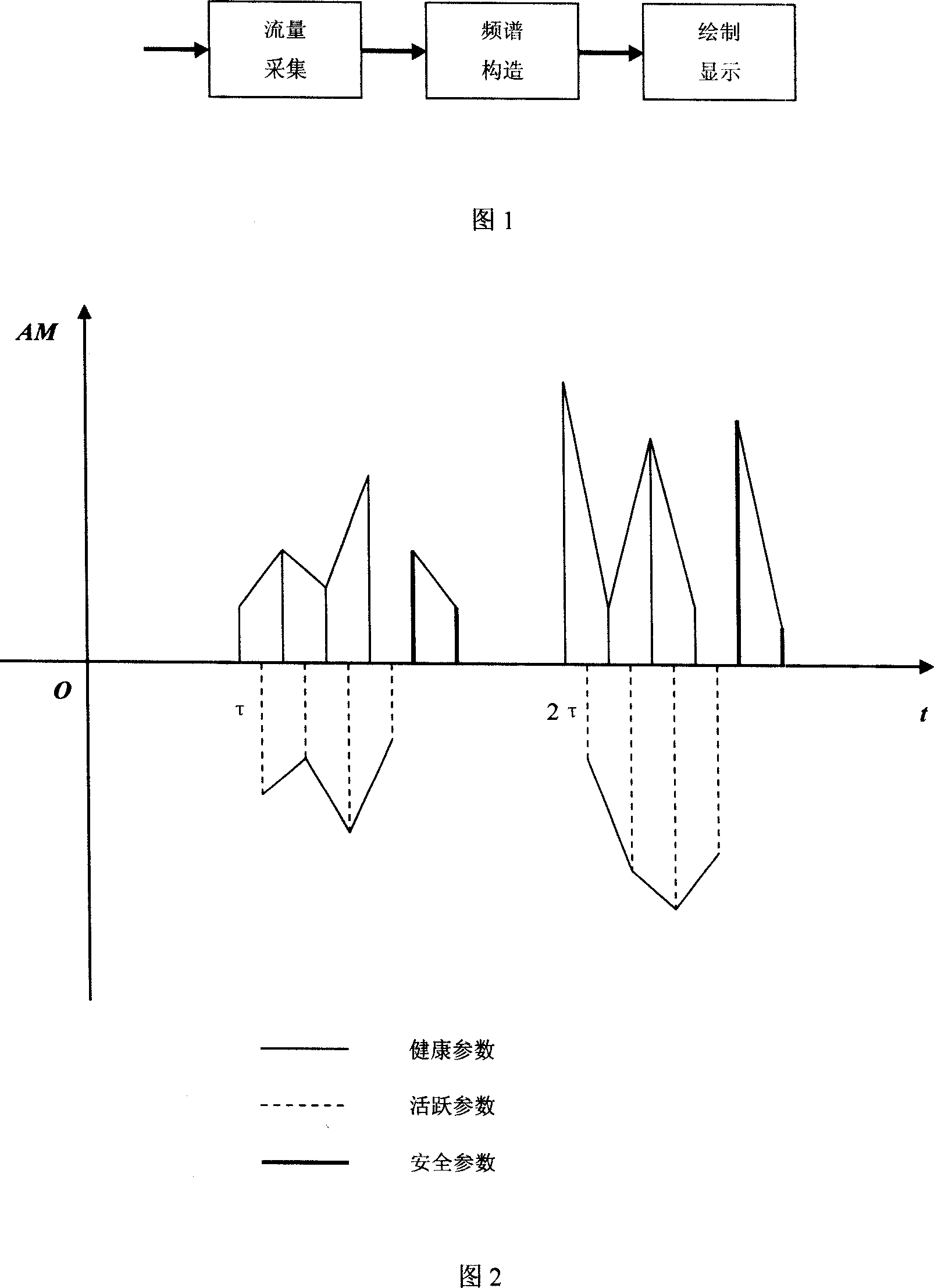
[0085] The system based on the method of the invention is composed of flow collection, frequency spectrum structure, drawing and display modules. The specific implementation and application of each module are as follows:
[0086] (1) Traffic collection: through hardware network devices integrated with security function chips, under the control of network traffic security policies, collect traffic information in the entire network environment with a fixed network traffic sampling cycle;
[0087] (2) Spectrum structure: extract the network security characteristic parameters that represent the network security and health degree, and assign different weight coefficients to the network security characteristic parameters according to their decisive role and influence degree on the network security and health degree, and perform normalization Process and construct...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com