System and method for preventing vicious code attach
A malicious code and operating system technology, applied in the field of systems that prevent malicious code intrusion, can solve problems such as the inability to prevent attacks, and achieve the effect of defending attacks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
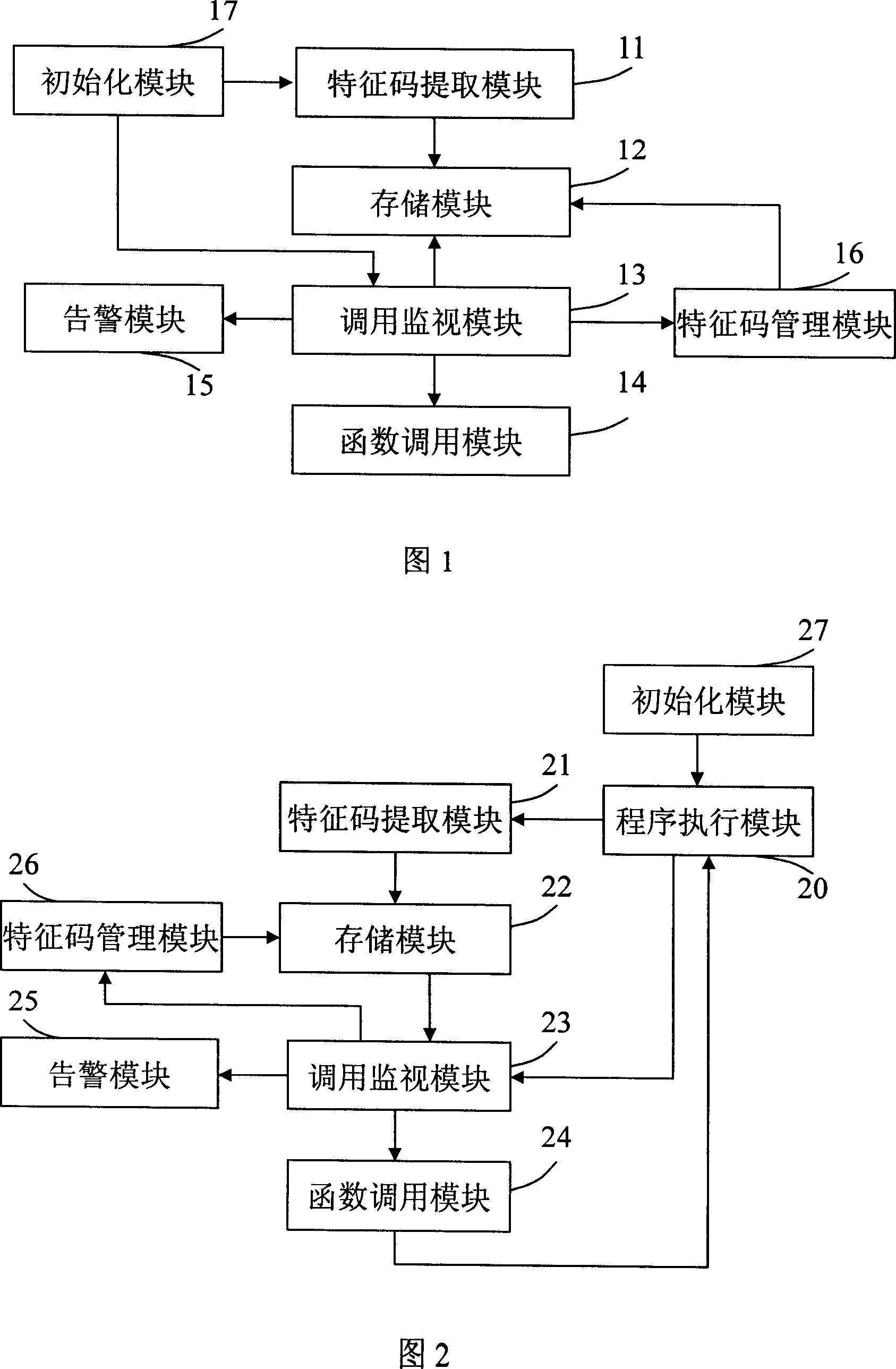
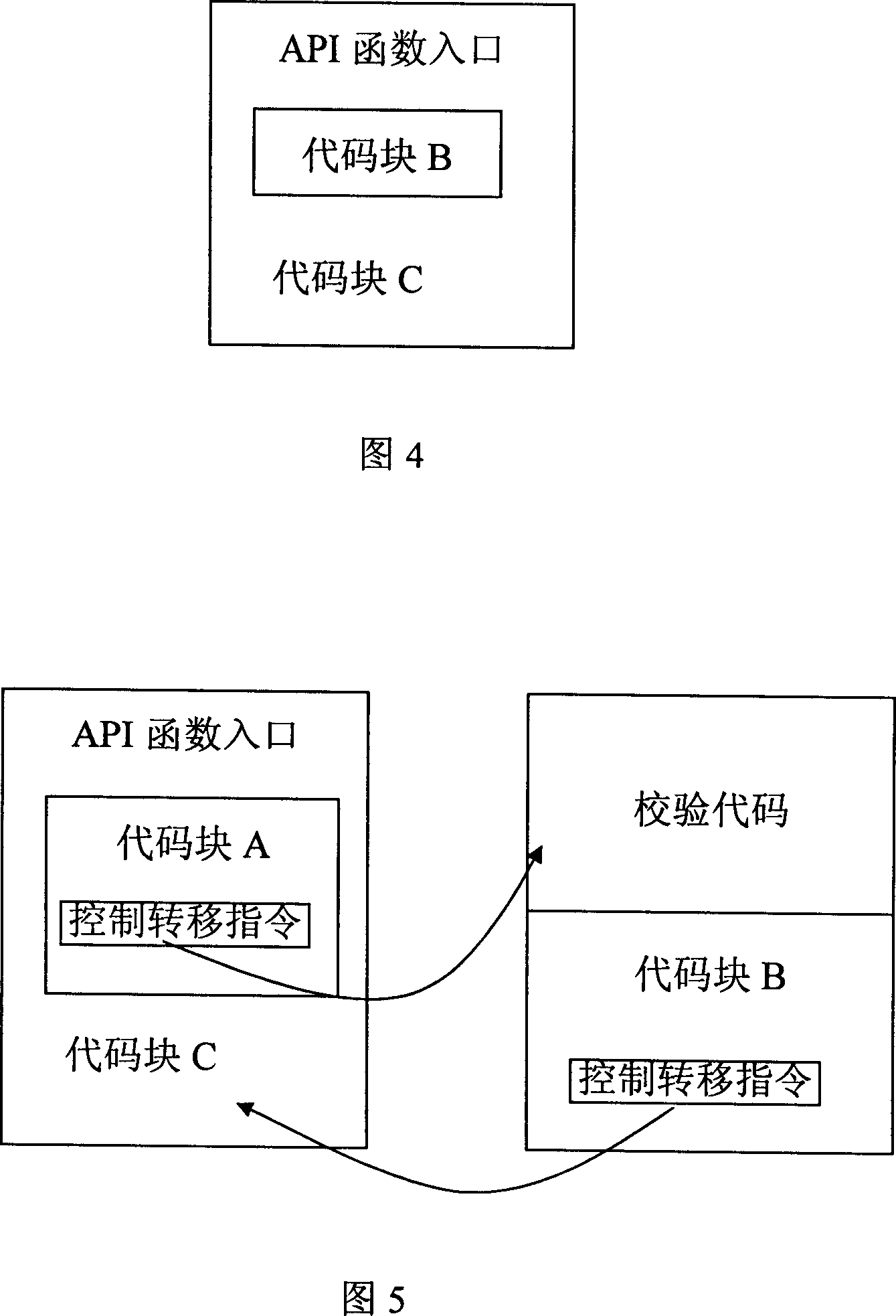
[0038] Generally, malicious code intrusion is mainly divided into two stages: the stage of obtaining the execution capability (AttackVector) and the stage of executing the attack (Exploit payload). After the malicious code obtains execution permission through methods such as dynamic link library (DLL) injection or buffer overflow, it must go through the execution attack stage to complete the attack. Existing ways to prevent malicious code intrusion start from preventing malicious code from obtaining execution capability, while the present invention starts from the execution attack stage to prevent malicious code from intruding.
[0039] In common intrusion attack methods, whether it is simply generating a super user or generating a remote user interface (Shell), whether it is a primary remote shell using passive mode, or a reverse remote shell for the purpose of bypassing the firewall, etc., The intrusion code must finally use system resources to complete its attack goal, that...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com