Method for setting data tunnel
A technology of data tunneling and tunnel information, applied in the direction of data exchange and network interconnection through path configuration, it can solve the problems of no description of carrying, establishment of data tunnels, and no description of tunnel information, etc., and achieve the effect of saving bandwidth resources.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
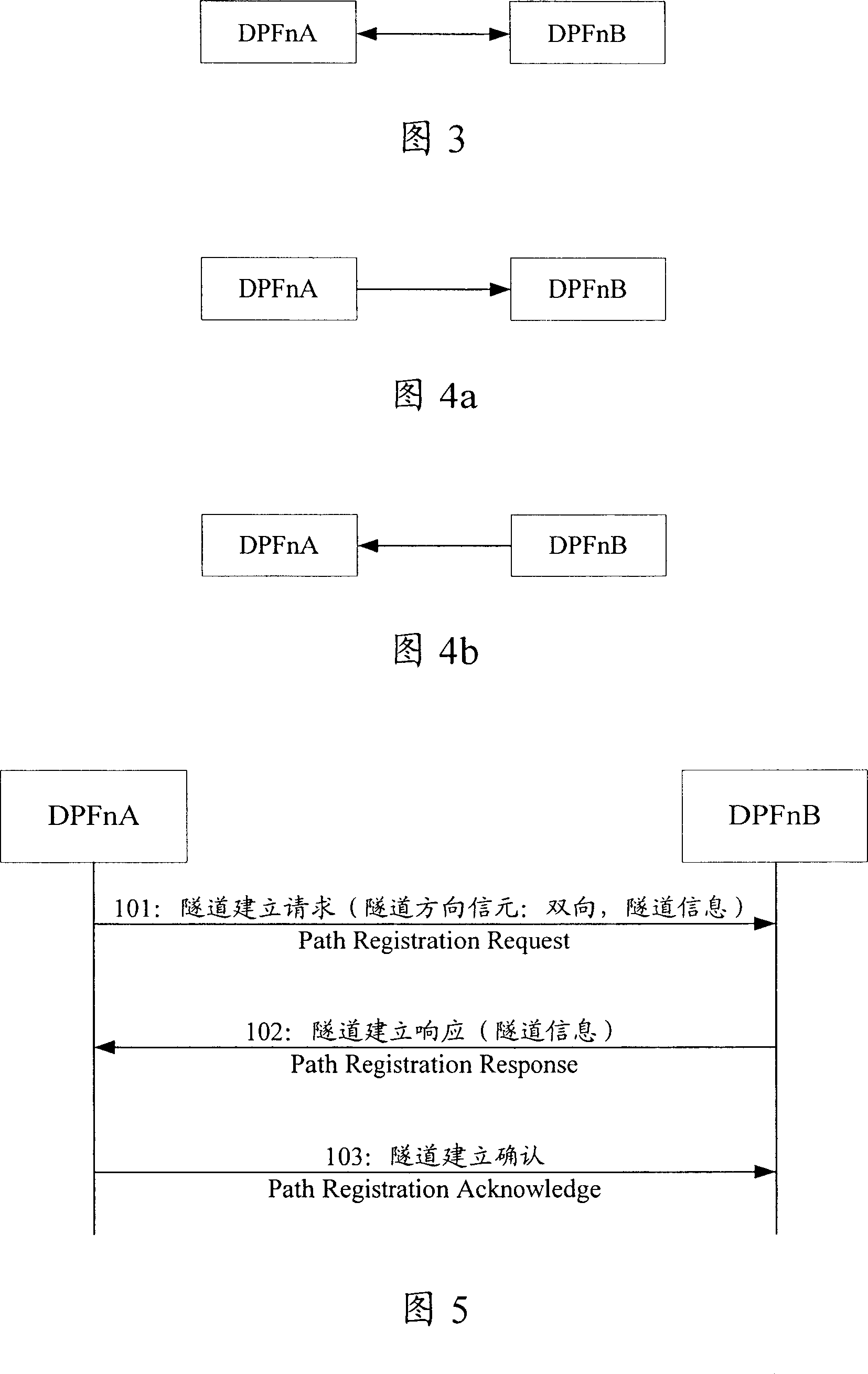
[0034] The first embodiment: establishing a bidirectional data tunnel between DPFnA and DPFnB.
[0035] Referring to Fig. 5, the flow chart of the first embodiment of the present invention is as follows:
[0036] Step 101, DPFnA sends a tunnel establishment request message to DPFnB, the message at least carries the tunnel information of DPFnA and the tunnel direction information element whose value is bidirectional.
[0037] Step 102: After receiving the tunnel establishment request message, DPFnB performs corresponding processing according to the tunnel direction information element, such as recording the tunnel information of DPFnA, reserving bandwidth resources, etc., and then returns a tunnel establishment response message to DPFnA, which at least carries DPFnB tunnel information.
[0038] Step 103: After receiving the tunnel establishment response message, DPFnA performs corresponding processing, such as recording the tunnel information of DPFnB, reserving bandwidth reso...
no. 2 example
[0039] The second embodiment: establishing a unidirectional data tunnel from DPFnB to DPFnA.
[0040] Referring to Fig. 6, the flow process of the second embodiment of the present invention is as follows:
[0041] Step 201, DPFnA sends a tunnel establishment request message to DPFnB, the message at least carries the tunnel information of DPFnA and the tunnel direction information element whose value is unidirectional.
[0042] Step 202: After receiving the tunnel establishment request message, DPFnB performs corresponding processing according to the tunnel direction information element, such as recording tunnel information of DPFnA, reserving bandwidth resources, etc., and then returns a tunnel establishment response message to DPFnA. Since the value of the tunnel direction information element in the tunnel establishment request message is unidirectional, the tunnel establishment response message does not carry the tunnel information of the DPFnB.
[0043] In step 203, DPFnA se...
no. 3 example
[0044] Embodiment 3: Establish a unidirectional data tunnel from DPFnA to DPFnB.
[0045] Referring to Fig. 7, the process of the third embodiment of the present invention is as follows:
[0046] In step 301, DPFnA sends a tunnel establishment request message to DPFnB, and the message carries a tunnel direction information element whose value is unidirectional. In addition, the message may also carry the tunnel direction information element whose value is bidirectional, and may further carry the tunnel information of the DPFnA.
[0047] Step 302: After receiving the tunnel establishment request message, DPFnB returns a tunnel establishment response message to DPFnA according to the tunnel direction information element. The message at least carries the tunnel information of DPFnB and the tunnel direction information element whose value is unidirectional.
[0048] If the tunnel establishment request message carries the tunnel direction information element whose value is bidirec...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com