Method to virtualize large files in a sandbox
a virtualization and large file technology, applied in the field of virtualization large file in a sandbox, can solve the problems of downgrading achieve the effects of reducing the overall performance of the sandbox, reducing the duplication of data, and facilitating the use of virtualization
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
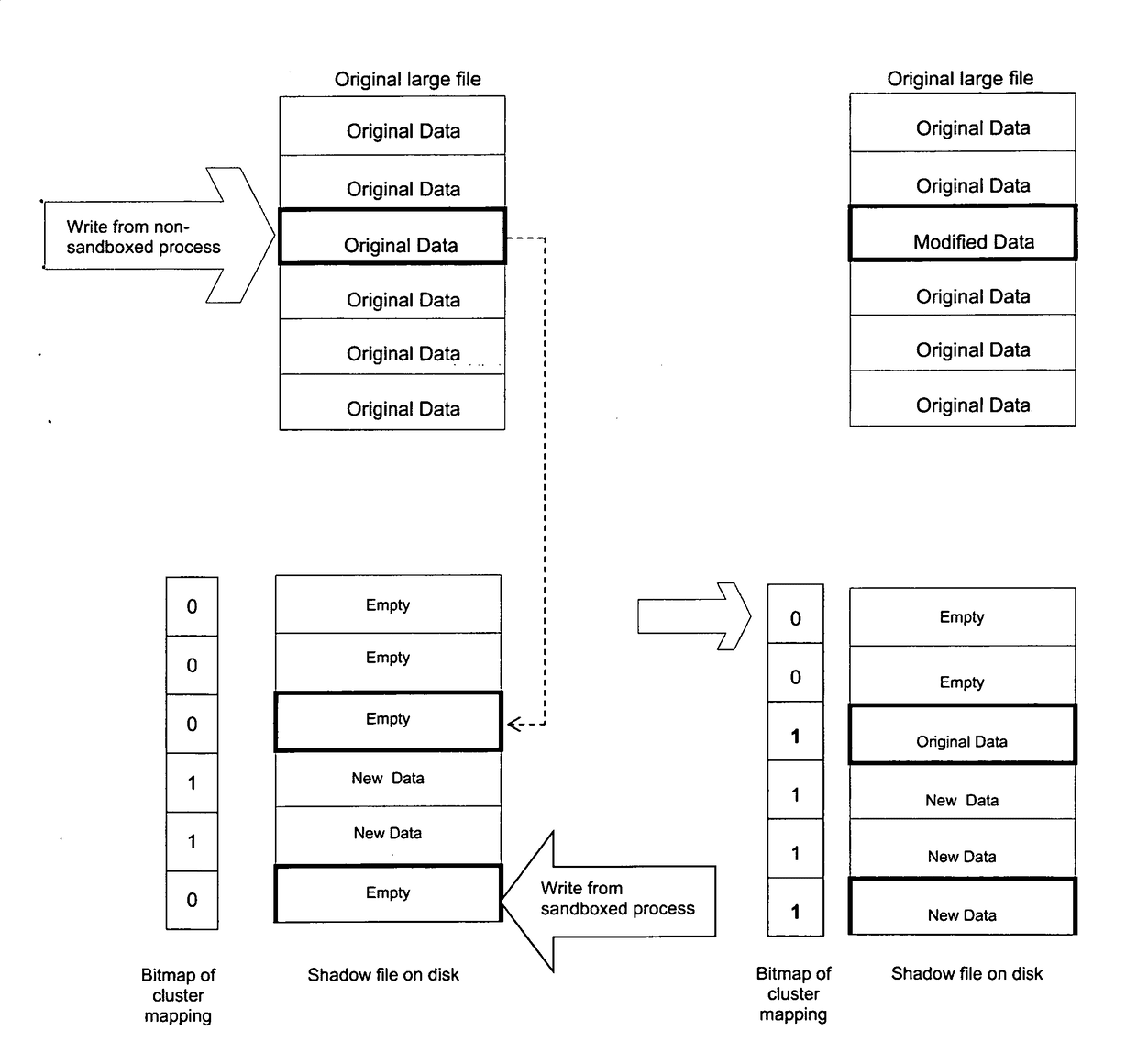
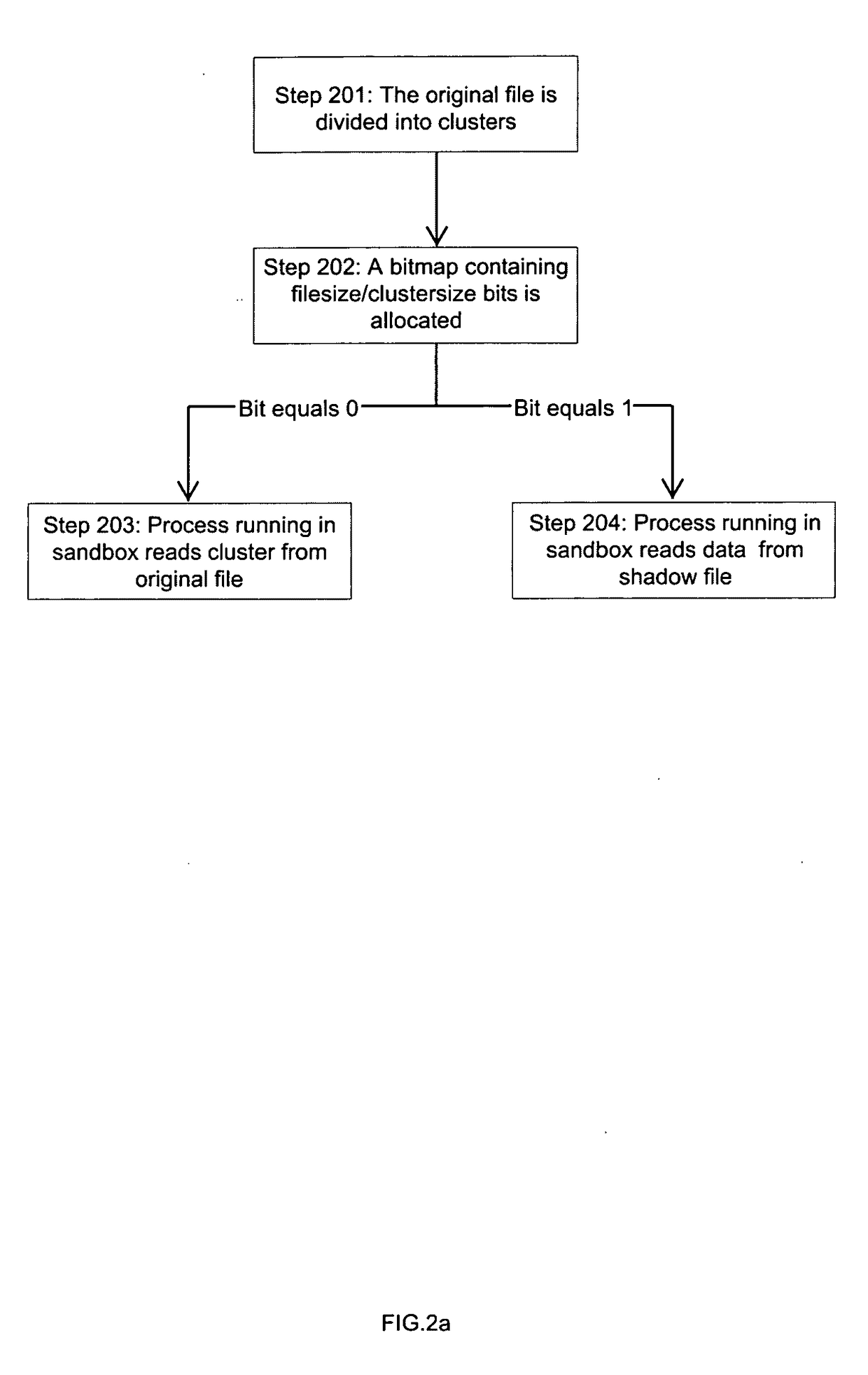
[0014]The present invention discloses the method of large file Virtualization in sandbox. The new method according to the present invention divides large file into pieces clusters by fixed byte counts, building a mapping relationship between logical view of sandboxed file and physical shadow file on disk.
[0015]The invention is not restricted to the details of the foregoing embodiments. The invention extends to any novel one, or any novel combination, of the features disclosed in this specification (including any accompanying claims, abstract and drawings), or to any novel one, or any novel combination, of the steps of any method or process so disclosed.
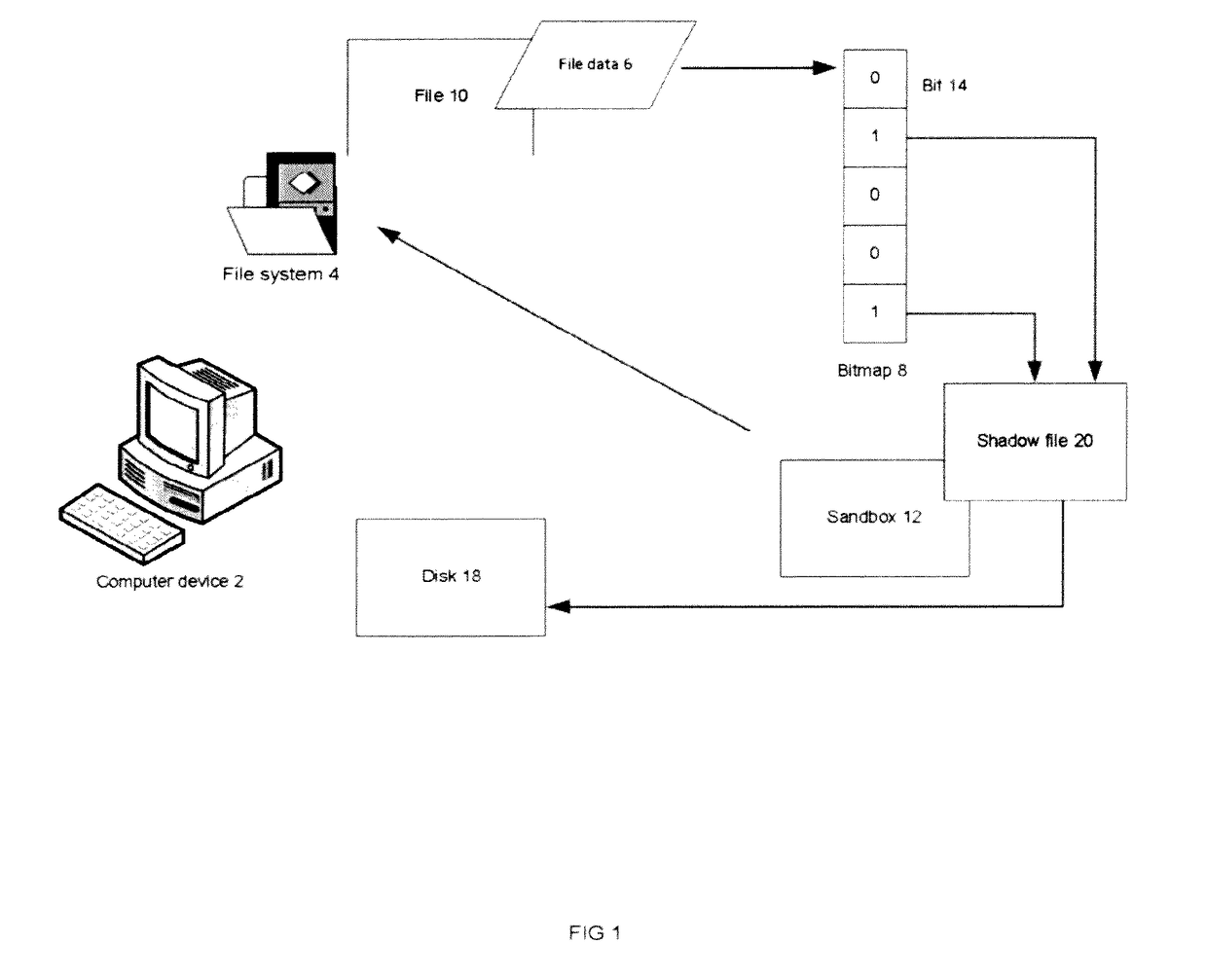
[0016]In FIG. 1 the sandbox process, running on a computer device 2, is accessing file system 4; the modification of file data 6 is recorded by a bitmap 8, and only modified part of the file 10 is redirected in sandbox 12. Bitmap 8 contains filesize or clustersize bits 14. Every bit 14 in bitmap 8 represents the redirect relationship ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com