Authentication system in DSTM communication network and method using the same
A verification method and a verification system technology, applied in the field of address translation, can solve problems such as inefficiency of communication networks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
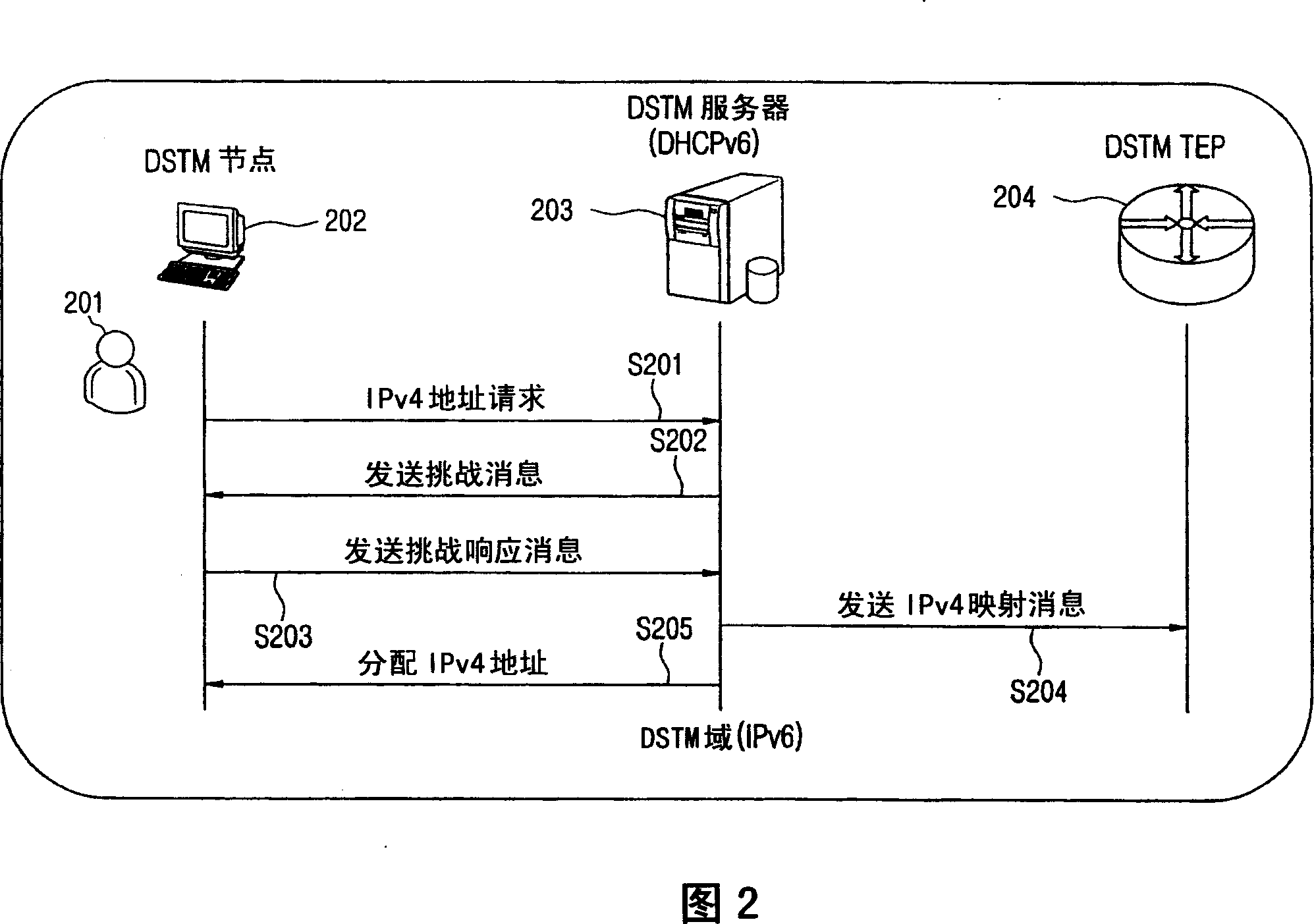
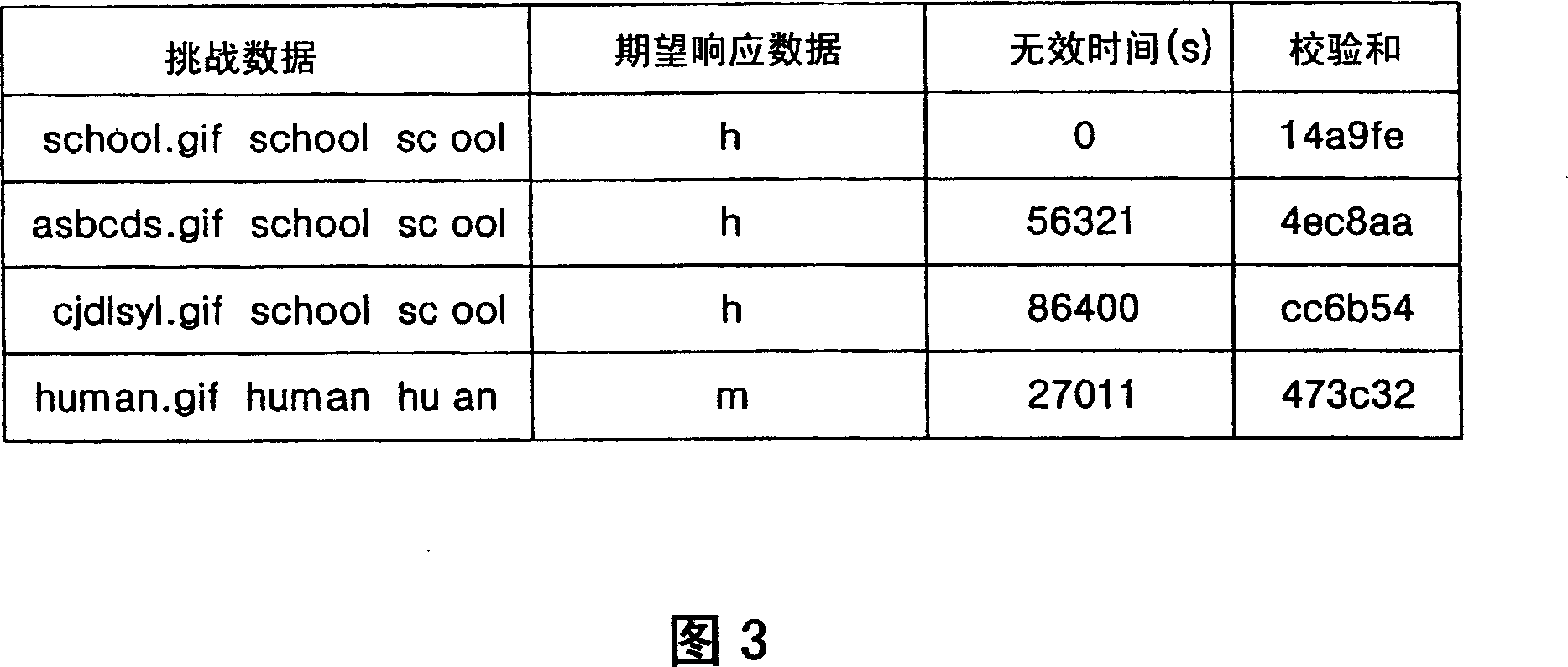
[0031] Hereinafter, exemplary embodiments of the present invention will be described in detail with reference to the accompanying drawings. Throughout the drawings, similar elements are indicated by like reference numerals. For matters related to the present invention and well known in the art, those matters will not be described in detail when it is considered that these descriptions would obscure the clarity and conciseness of the present disclosure. The present invention provides a verification system and method that, in response to a verification request, performs verification through a response process based on a verification message recognizable by a human, rather than an automatic mechanism of the system, to verify a dual protocol stack transition Mechanism (DSTM) node.
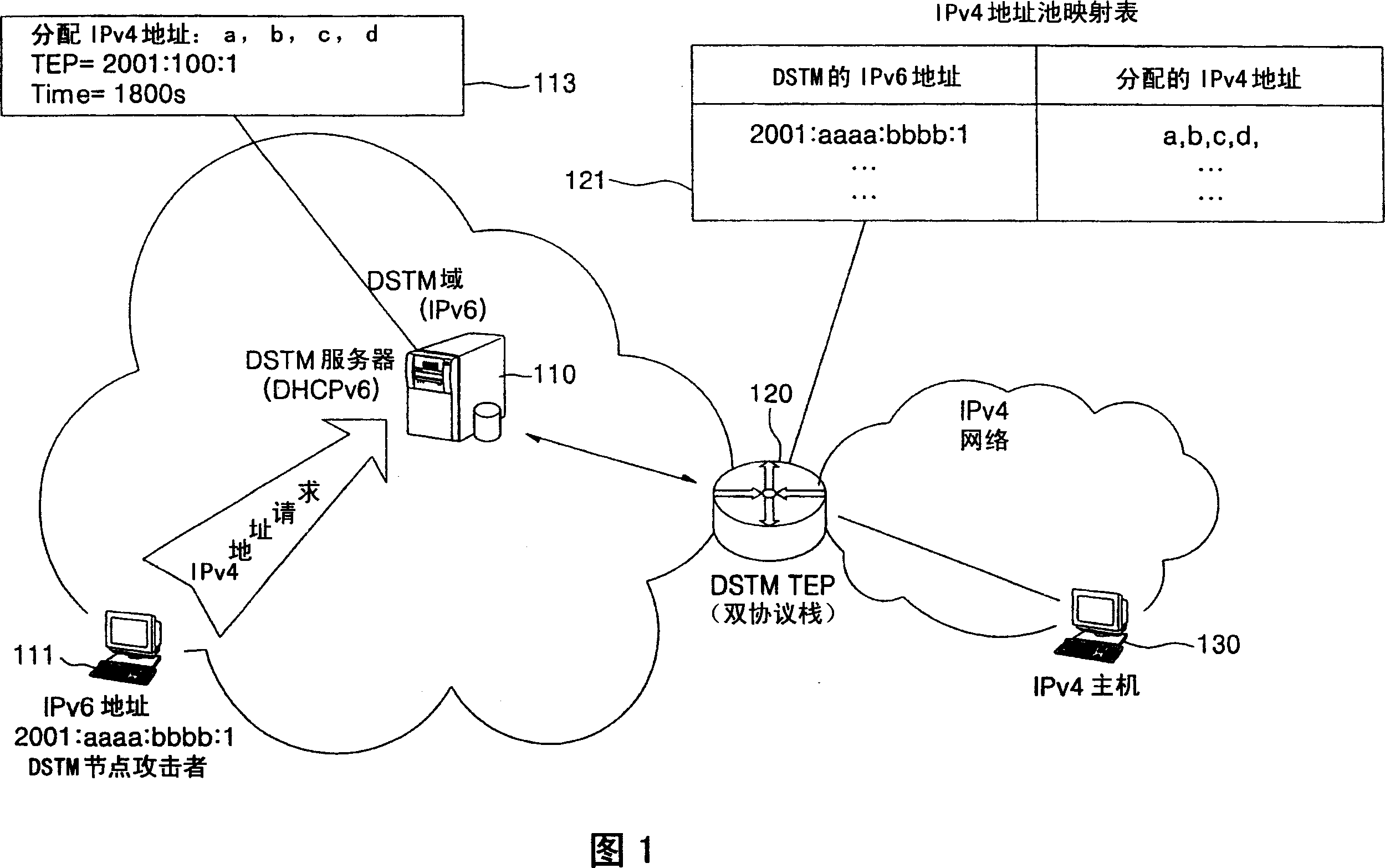
[0032] Figure 1 shows the process of a DSTM node obtaining an IPv4 address for communicating with an IPv4 node, and the problem of exhausting the IPv4 address pool of a DSTM server by an attacker of a...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com