Method and system for confirming identification using key when user accessing identification proxy
A technology of access authentication and key, which is applied to the public key and key distribution of secure communication, which can solve the problems of non-compliance with AS's authentication security, key non-compliance, and key non-compliance.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
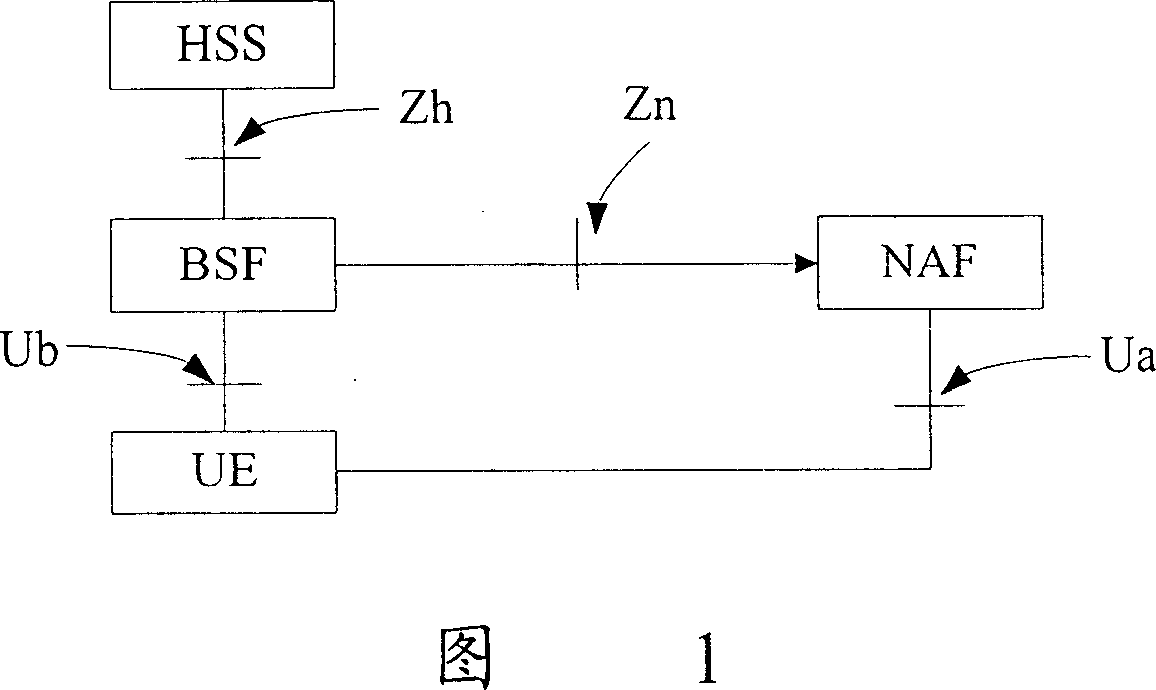
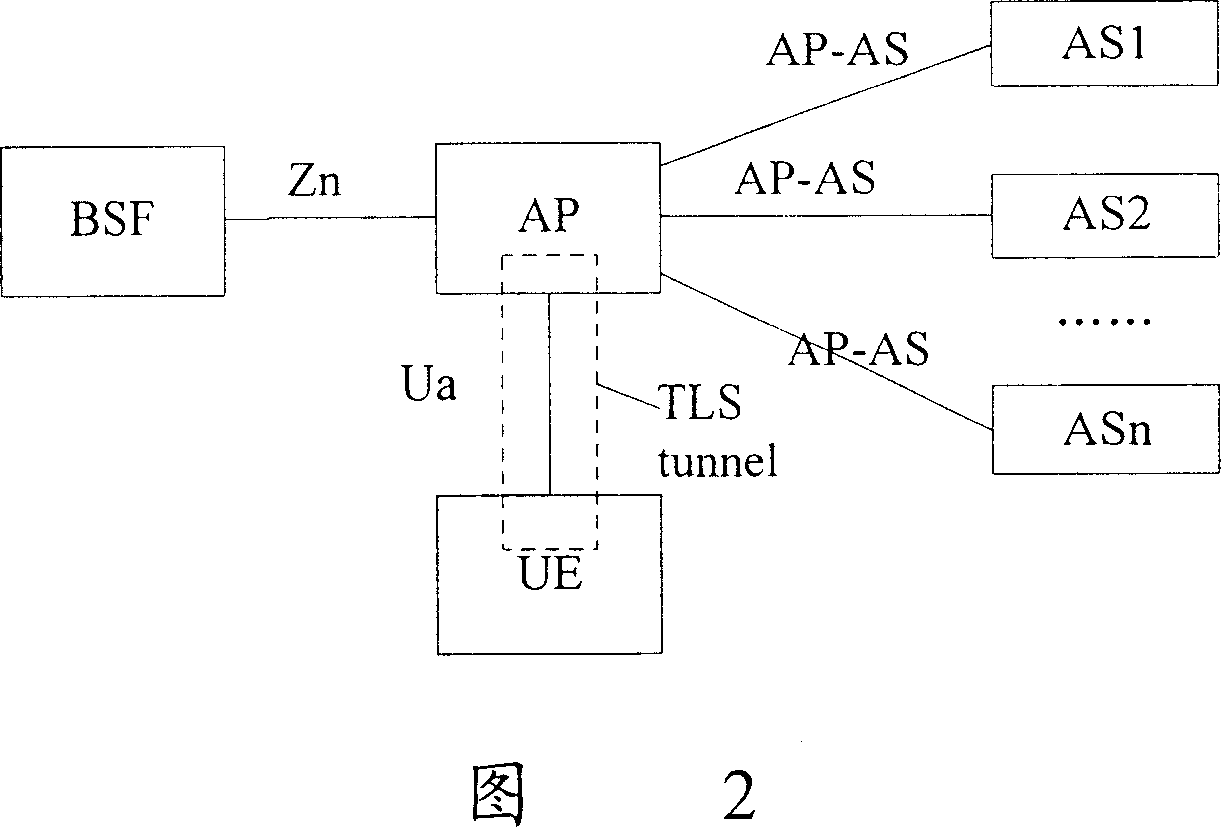
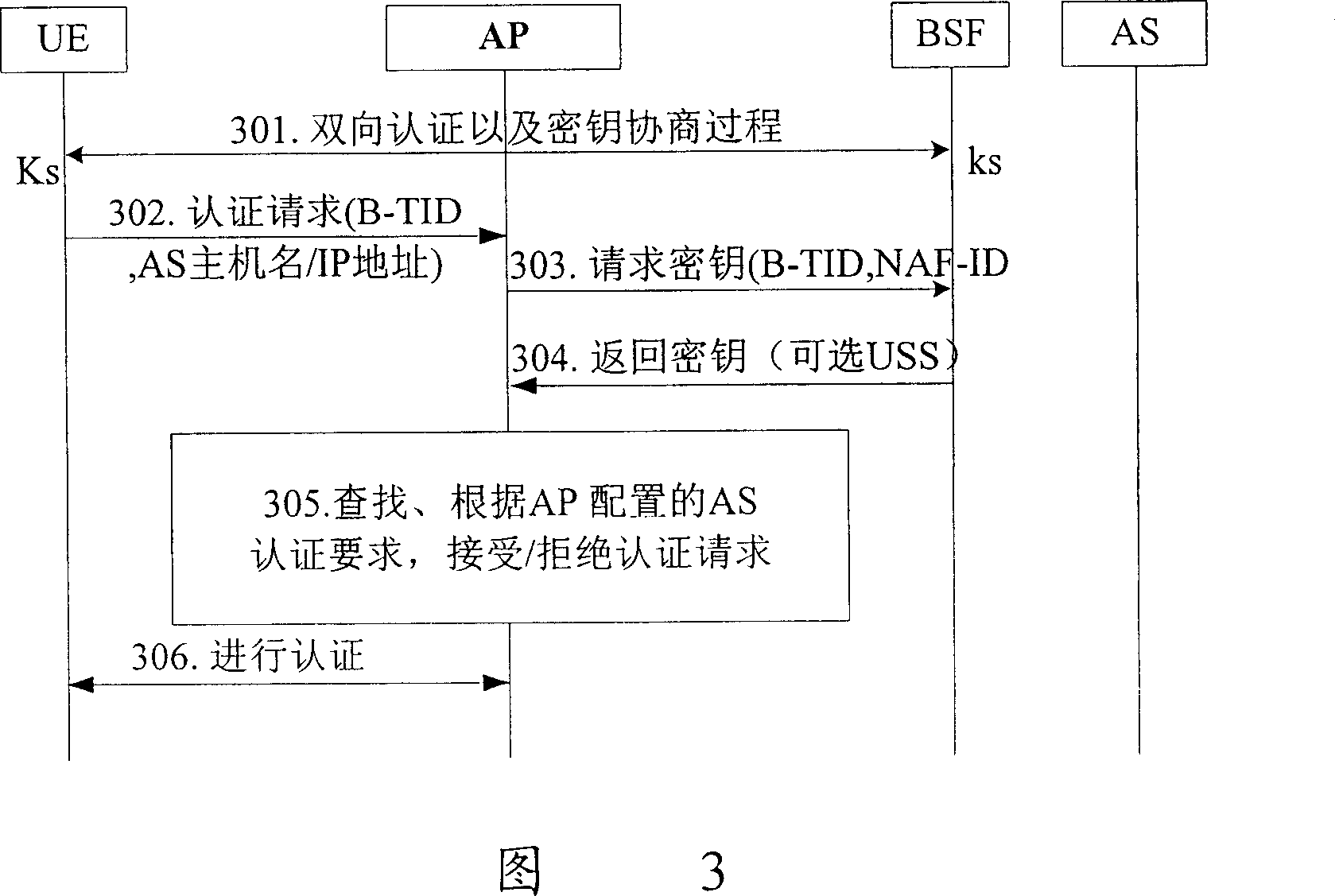
[0040] In advance, the AP configures the requirements for the type of keys required for authentication for each associated AS, and the configuration information can be configured in the authentication requirement information configured by the AP for the AS. This configuration information is used to specify the requirements of the AS for the key type required for authentication, which can be one of Ks_NAF, Ks_ext_NAF, Ks_int_NAF; or a preferred type. During configuration, associate and save the AS authentication requirement information with the corresponding AS name. So that the AP can retrieve the corresponding authentication requirement information according to the AS name.
[0041] The key types required for authentication are configured for each AS as described above, which can also be configured in the BSF (configurable by the operator), and then sent to the AP after configuration.
[0042] After the above information is configured, when communicating between the AP and t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com