Method and system for protecting software on additional card of peripheral equipment
A technology of peripheral equipment and add-on cards, which is applied in the direction of instruments, electronic digital data processing, program control devices, etc., and can solve the problems of being vulnerable to illegal plagiarism and mass duplication
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
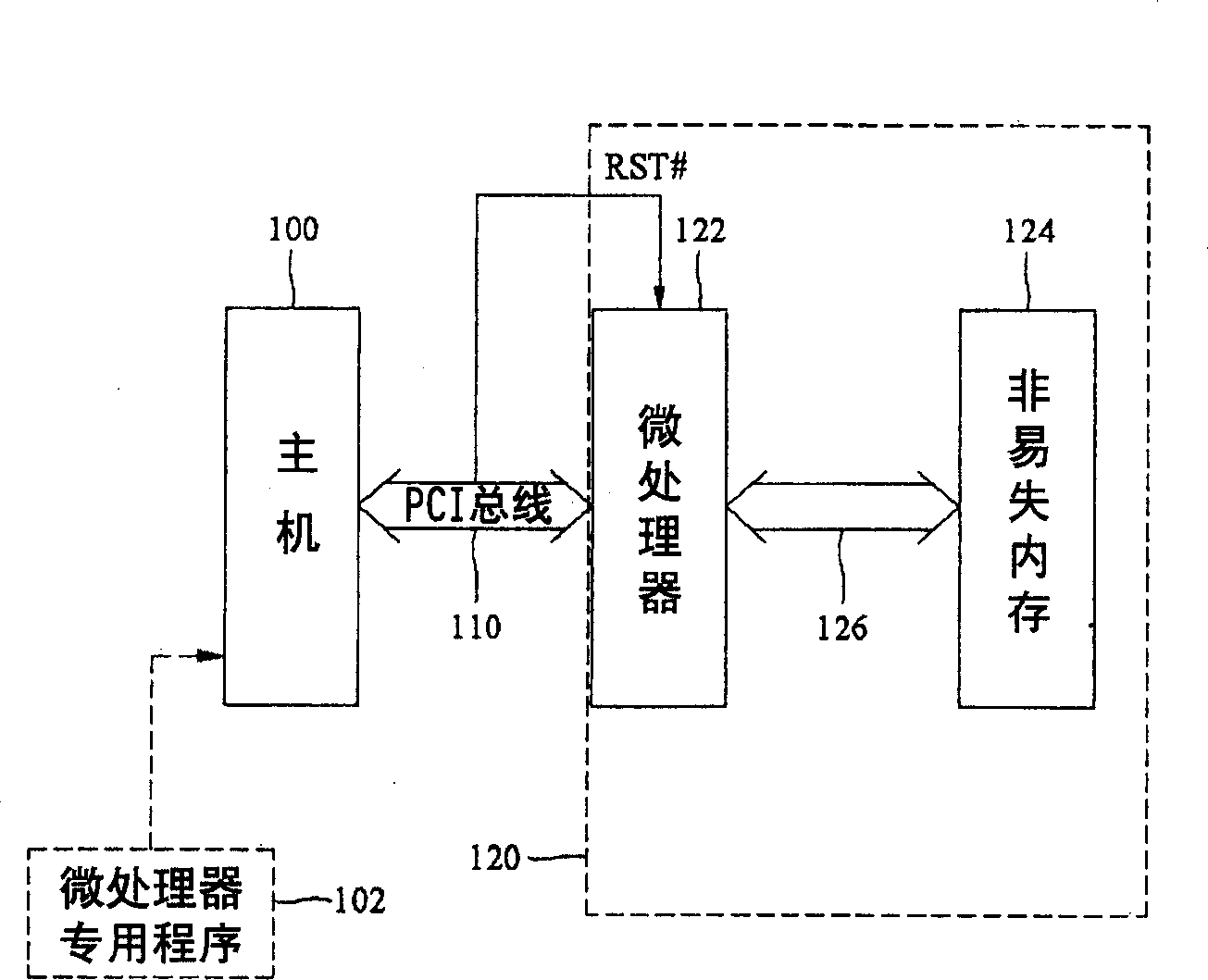
[0014] refer to figure 1 , the traditional peripheral equipment add-in card 120 is made up of microprocessor 122 and nonvolatile memory 124, and microprocessor 122 has interface 126 to connect nonvolatile memory 124 in order to read and write the data stored therein, and microprocessor 122 can be replaced by an Application Specific Integrated Circuit (ASIC). Taking a microprocessor as an example, the host computer 100 is controlled by a peripheral component interconnect (Peripheral Component Interconnect, PCI) bus 110. The microprocessor on the peripheral add-on card 120 122 and exchange data with it. The driver program or application program 102 dedicated to the microprocessor 122 is loaded into the host computer 100 for execution after booting, and resets the microprocessor 122 through the reset signal RST# of the PCI bus 110 to activate the peripheral device add-in card 120 to work. Since the data in the non-volatile memory 124 is read and written through the interface 126...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com