Movable external memory content enciphering method independent of computer
A computer and content technology, applied in the direction of protecting stored content from loss, preventing unauthorized use of memory, etc., can solve problems such as the general limitations of mobile external storage devices, and the lack of reliable protection of content, and the method is simple, practical, and efficient. Increased security and ease of use, high reliability effects
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment approach
[0016] In the present invention, the step of running the encryption program can also be realized by installing and running the encryption program in the mobile external storage in the computer.
[0017] In one embodiment of the present invention, when the mobile external memory is inserted into the computer, the encryption program in the mobile external memory is installed in the computer; after the encryption program is installed in the computer, the computer automatically runs the encryption program every time it is started. program.
[0018] The method of the present invention can be independent of the computer and only relies on the mobile external storage to realize the encryption of the content of the mobile external storage, thereby greatly increasing its security and ease of use; when the mobile external storage encrypted according to the present invention is inserted into any computer After connecting the USB interface, the encryption method of the present invention w...
Embodiment 1
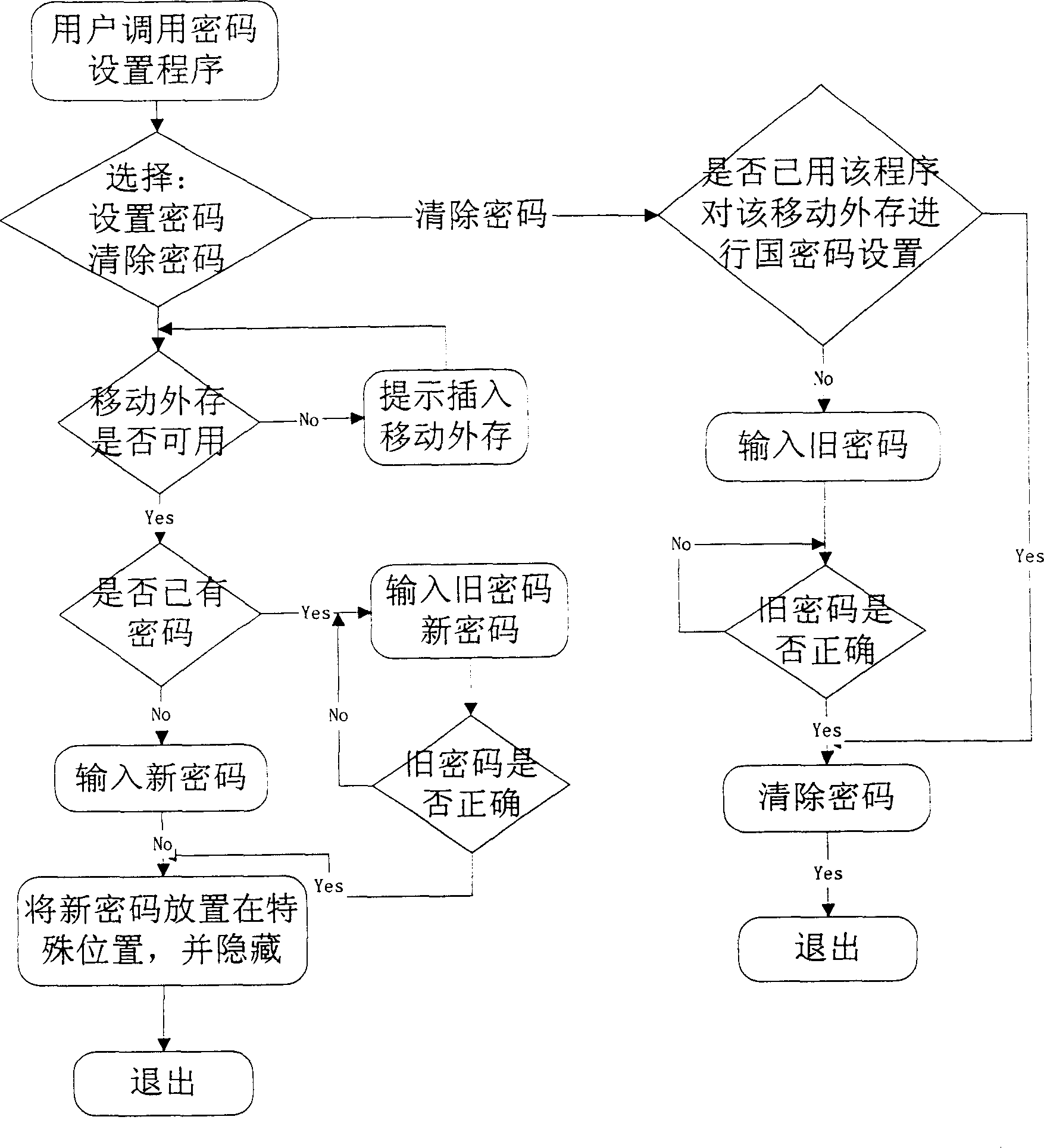
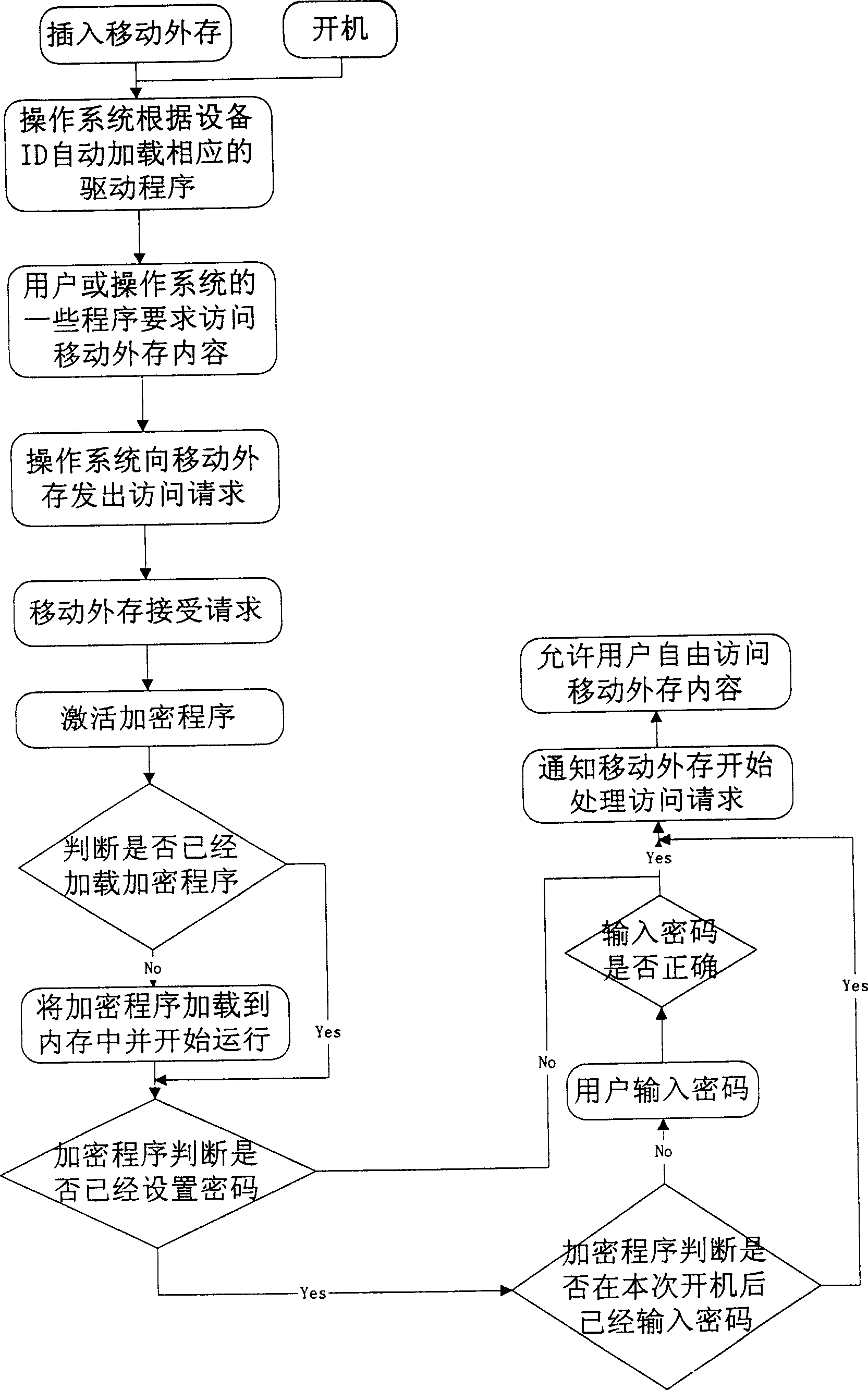
[0026] figure 1 and figure 2 is a flowchart illustrating the embodiment.
[0027] 1. First, there needs to be a program for setting a password for the mobile external storage. This program is an independent program installed in the operating system. This program provides functions of password setting and password erasing. When the user needs to set a password for the mobile external storage, call this program, and the program will store the set password in a special location of the mobile external storage and hide it. There are many methods for hiding passwords, and the functions of these methods for hiding passwords are also strong or weak, which can be selected according to user needs. When the user forgets the password of the mobile storage, the password of the mobile storage can be deleted on this machine. (The computer that installs the password setting program can have the authority to set, modify, and delete the password of the mobile external storage)
[0028] 2. ...
Embodiment 2
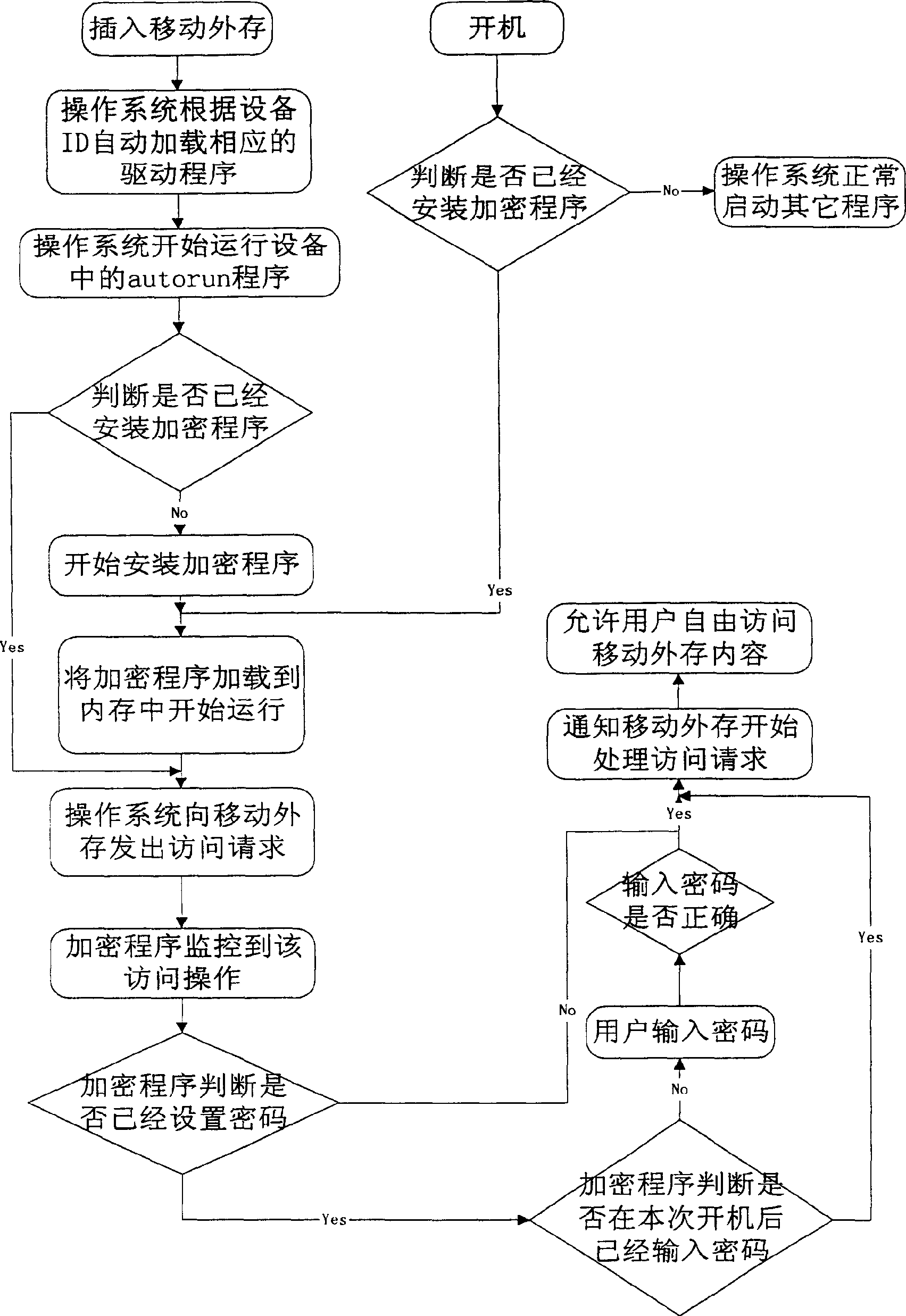
[0035]The biggest difference between Embodiment 2 and Embodiment 1 is that the encryption program is activated in different ways, such as image 3 shown. Embodiment 2 mainly utilizes the principle similar to the automatic operation of a CD. At the same time, the encryption program is installed in the computer, rather than just loaded into the computer memory as in Embodiment 1, so this scheme will leave traces in the computer.
[0036] 1. First, there is a program for setting a password for the mobile external storage, which can be the same as that described in Embodiment 1, such as figure 1 shown.
[0037] 2 Secondly, place an AUTORUN.INF file in the root directory of the mobile memory (this file is mainly used to automatically run the contents of the mobile memory when it is just inserted , the disc can be automatically started), the file is read-only, but not hidden, and the file is always readable and will not be encrypted.
[0038] 3. At the same time, the encryption p...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com