Identity card identifier for Internet device
A technology of identity and users, applied in the field of methods and systems, can solve problems such as time-consuming and troublesome, and achieve the effect of preventing unauthorized sharing
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
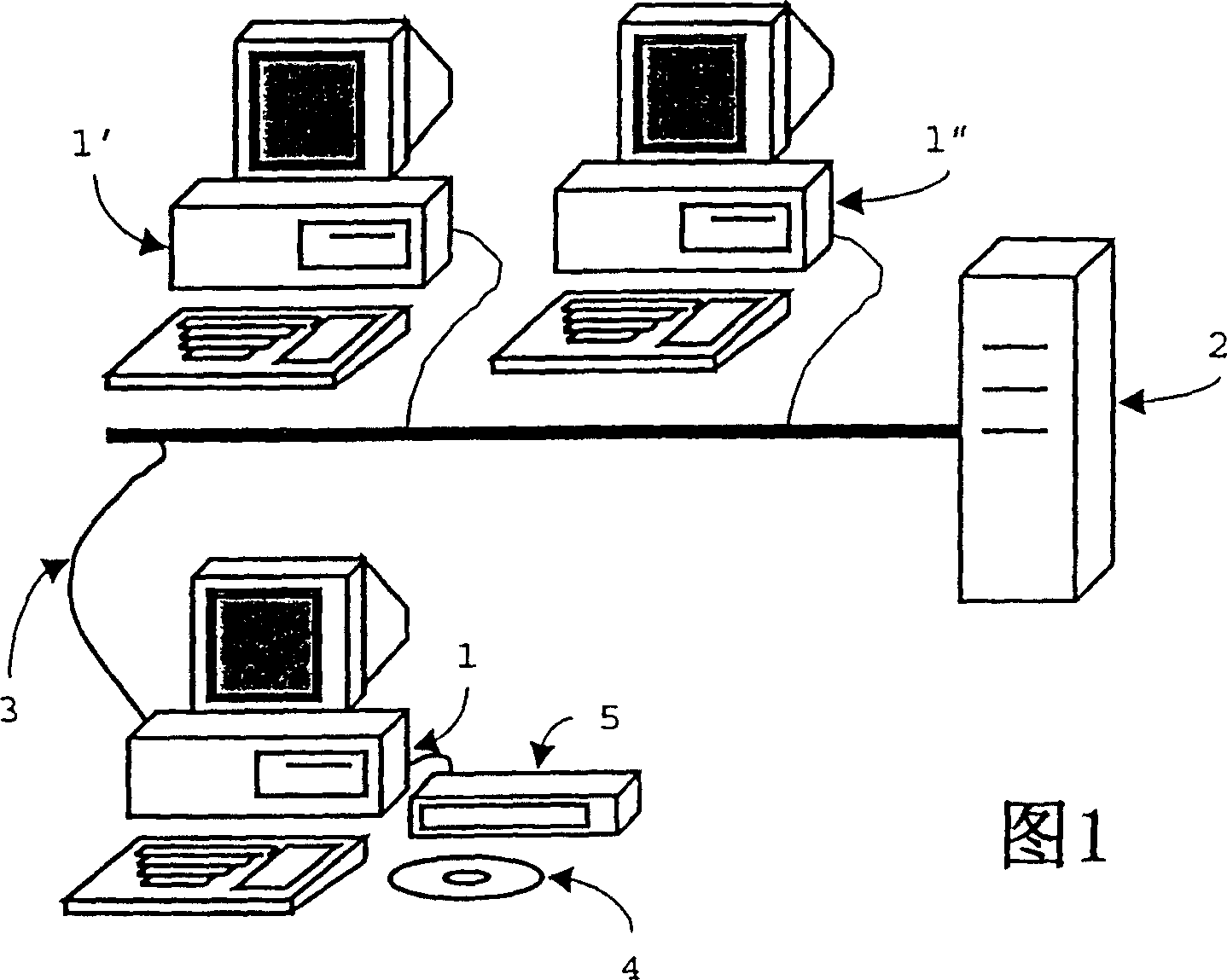
[0018] Figure 1 shows a computer network using the method according to the invention. A first device 1, in this case a computer in a network, is directly or indirectly connected to a second device 2, so that data can be transferred from one to the other. In this particular embodiment, the second device is a server. The first device is connected to the second device 2 via a data link 3 . Data link 3 may be a network like a local area network, a dial-up connection, or an Internet connection.
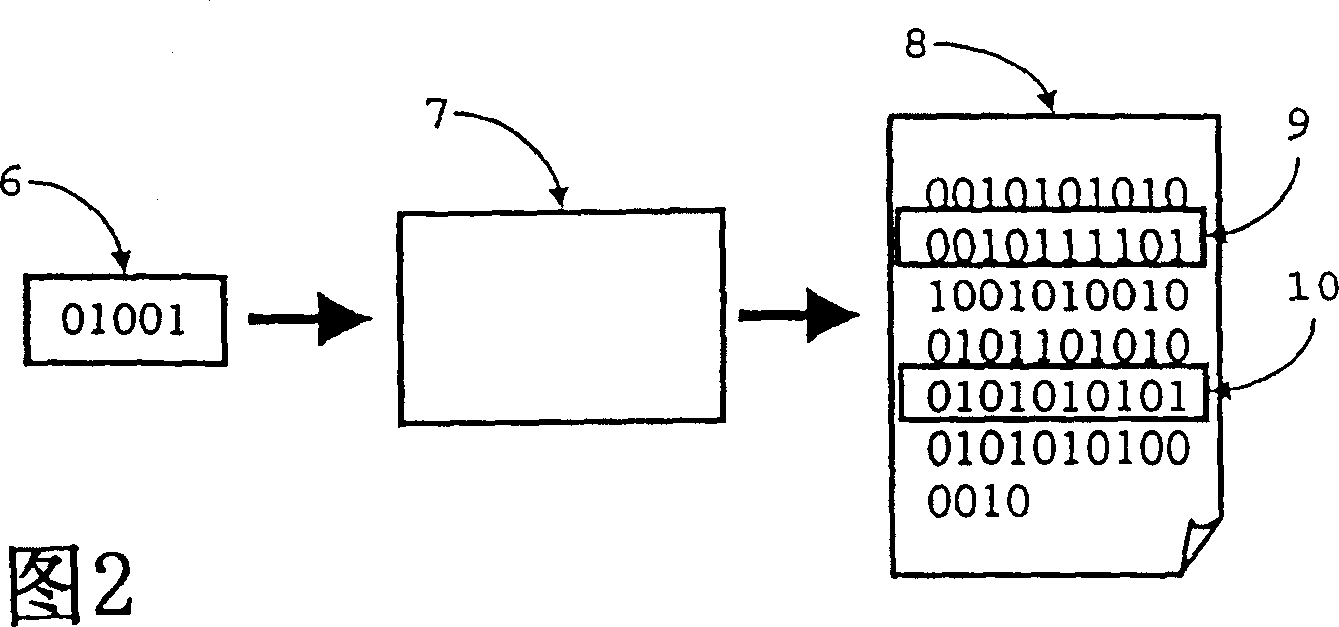
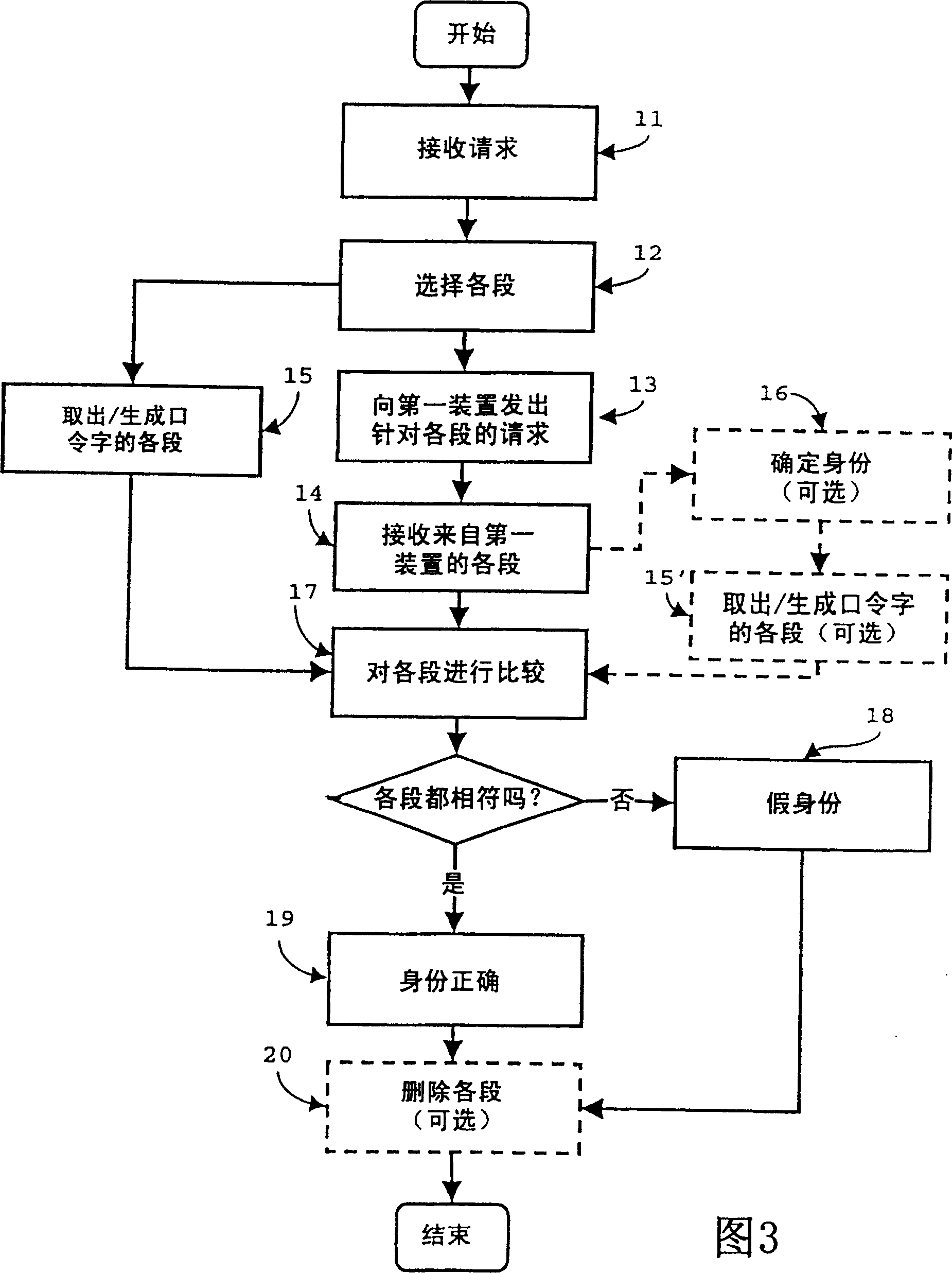
[0019] A user of the first device 1 wishes to log in in order to retrieve files eg from the second device or from other connected devices in the network. The user has been provided with available passwords, consisting of a very long string of bits. This password is unique to the user. Also, some way of associating the user with the password could be used. This could be a set of codes in part of a very long string of bits, or a user name, or an identification of the computer 1 .
[00...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com