Method, system and equipment for generating anti-counterfeiting code from product number and storage medium
An anti-counterfeiting code and product number technology, applied in data processing applications, instruments, calculations, etc., can solve problems such as low algorithm efficiency and insufficient encryption strength, and achieve high encryption strength, uniqueness and unforgeability.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
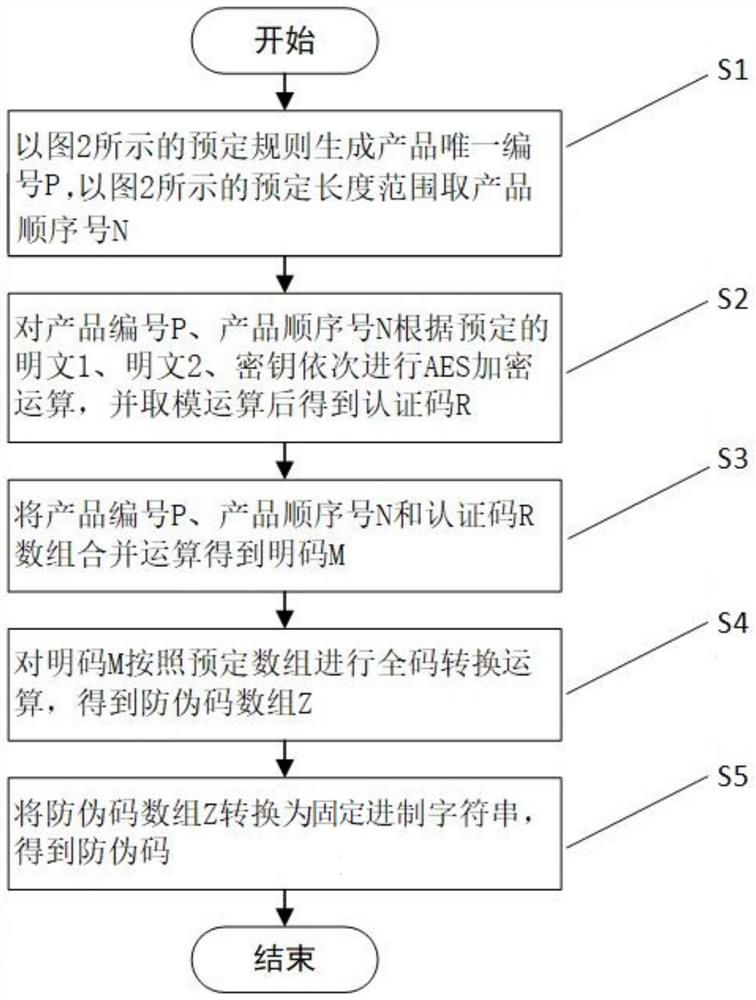
[0113] Step S1: Follow Figure 5 The reservation rule shown generates the product unique number 00001, according to Figure 5 The shown predetermined length range takes the product sequence number 00000001, and then proceeds to step S2.
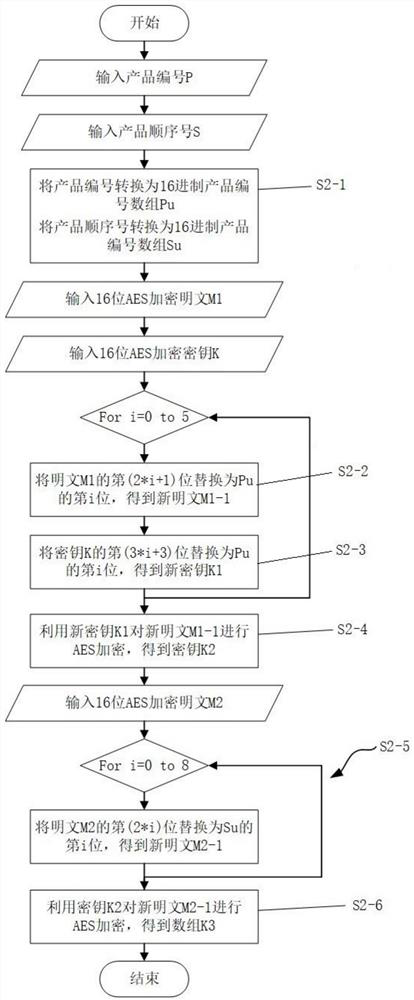
[0114] Step S2: Convert the product number 00001 into a hexadecimal product number array Pu{0,0,0,0,1}, and replace the product sequence number 00000001 with a hexadecimal product number array Su{0,0,0,0 ,0,0,0,1}, and according to the predetermined plaintext M1{
[0115] 0xf6,0xF1,0xf6,0xa6,
[0116] 0x09,0xf6,0xB3,0xC9,
[0117] 0xd2,0x09,0xae,0xCA,
[0118] 0x83, 0x34, 0xAF, 0x9E
[0119] }, plaintext M2{
[0120] 0x88,0x5a,0x30,0x8d,
[0121] 0x32,0x43,0xf6,0xa8,
[0122] 0x31,0x31,0x98,0xa2,
[0123] 0xe0, 0x37, 0x07, 0x34
[0124] }, key K{
[0125] 0xF1,0x34,0xa6,0x09,
[0126] 0xab,0x7E,0xF1,0xAB,
[0127] 0xd2,0x09,0xae,0xCA,
[0128] 0xC9, 0xf6, 0xcf, 0x7E
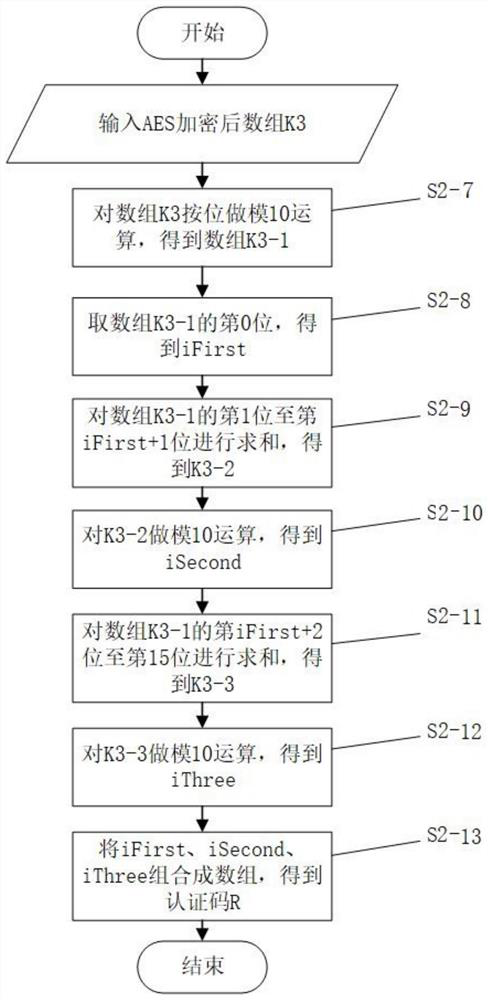
[0129] } Perform the AES encryption algorithm operation in tur...
Embodiment 2
[0158] Step S1: Follow Image 6 The reservation rule shown generates the product unique number 01, according to Image 6 The shown predetermined length range takes the product sequence number 0000001, and then proceeds to step S2.
[0159] Step S2: Convert the product number 01 into a hexadecimal product number array Pu{0,1}, and replace the product sequence number 0000001 with a hexadecimal product number array Su{0,0,0,0,0,0,1 }, and according to the predetermined plaintext M1{
[0160] 0xf6,0xF1,0xf6,0xa6,
[0161] 0x09,0xf6,0xB3,0xC9,
[0162] 0xd2,0x09,0xae,0xCA,
[0163] 0x83, 0x34, 0xAF, 0x9E
[0164] }, plaintext M2{
[0165] 0x88,0x5a,0x30,0x8d,
[0166] 0x32,0x43,0xf6,0xa8,
[0167] 0x31,0x31,0x98,0xa2,
[0168] 0xe0, 0x37, 0x07, 0x34
[0169] }, key K{
[0170] 0xF1,0x34,0xa6,0x09,
[0171] 0xab,0x7E,0xF1,0xAB,
[0172] 0xd2,0x09,0xae,0xCA,
[0173] 0xC9, 0xf6, 0xcf, 0x7E
[0174] } Perform the AES encryption algorithm operation in turn to obtain the ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com