Big data computer security protection device
A technology for computer security and protective devices, applied in the field of computer security, can solve the problems of small protective device space, loss of enterprises or systems, secondary damage to big data computers, etc., to increase placement stability, facilitate fixation, and avoid accidental falls. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0028] In the description of the present invention, it should be understood that the terms "center", "longitudinal", "lateral", "length", "width", "thickness", "upper", "lower", "front", " Rear, Left, Right, Vertical, Horizontal, Top, Bottom, Inner, Outer, Axial, Radial, Circumferential The orientation or positional relationship indicated by etc. is based on the orientation or positional relationship shown in the drawings, and is only for the convenience of describing the technical solutions of the present invention and simplifying the description, rather than indicating or implying that the device or element referred to must have a specific orientation, It is constructed and operated in a particular orientation and is therefore not to be construed as a limitation of the present invention.
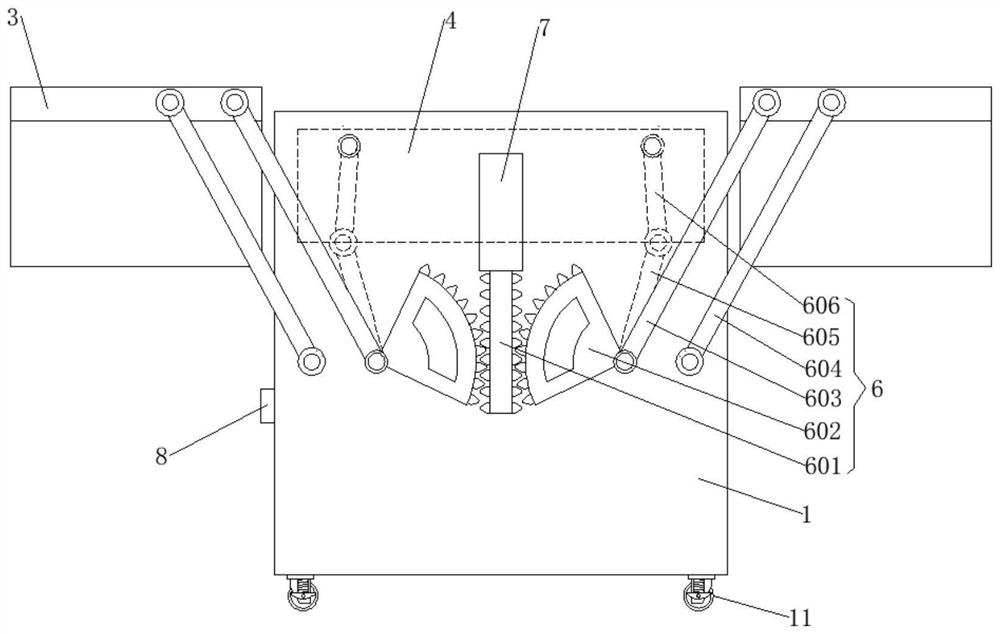
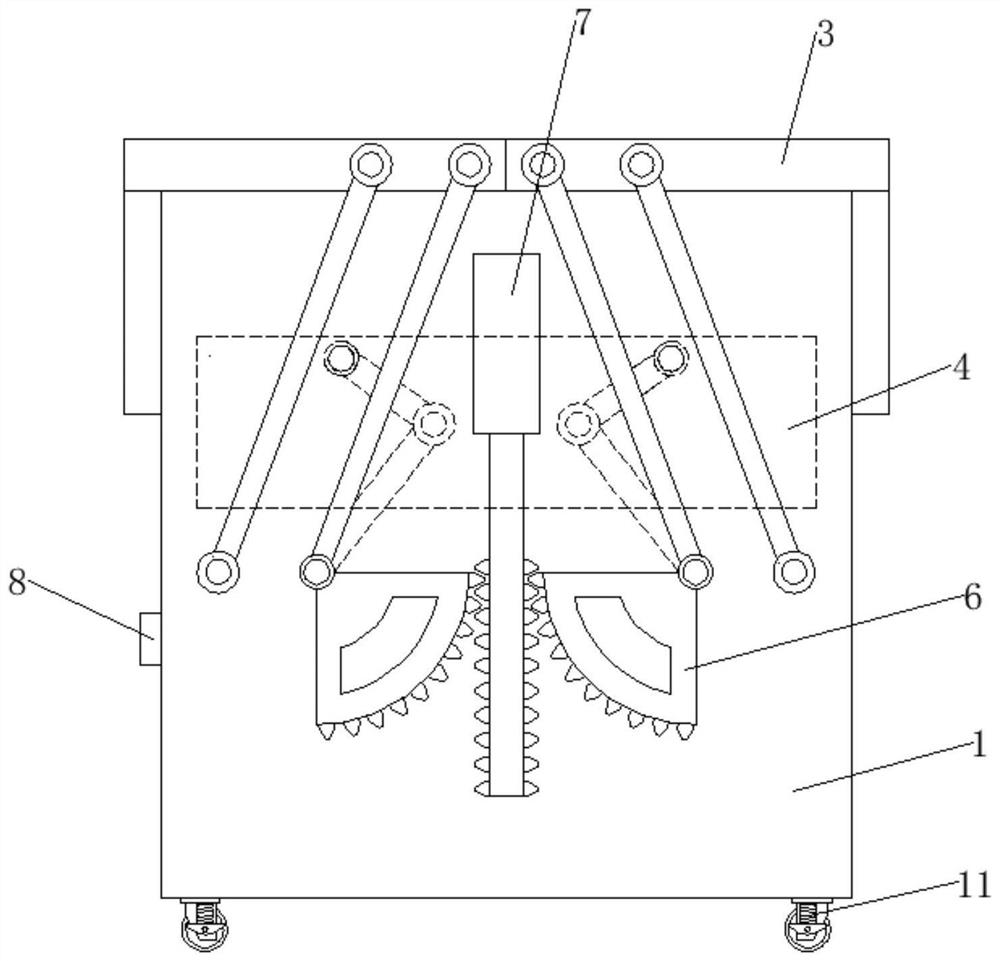
[0029] like Figures 1 to 6 As shown, a big data computer security protection device includes:
[0030] The protective shell 1, the upper end of the protective shell 1 is an open structu...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com