Security authentication method and system based on computer
A security authentication and computer technology, applied in the field of computer-based security authentication methods and systems, can solve the problems of lack of unified friendly interface, low usability, complicated operation, etc., and achieve real-time authentication, avoid hidden dangers of data security, and simple operation Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
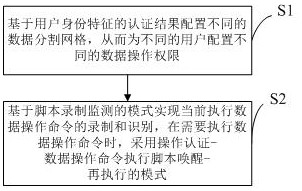
[0028] like figure 1 As shown, the computer-based security authentication method includes the following steps:
[0029] S1, configure different data division grids based on the authentication results of the user identity characteristics, thereby configuring different data operation rights for different users; the data division grids are used to frame the data of the database in the corresponding data operation rights respectively. In the grid, different data operation permissions include hidden, read-only, transfer only, revision only, and full authority;
[0030] S2. Realize the recording and identification of the currently executed data operation command based on the mode of script recording and monitoring. When the data operation command needs to be executed, the mode of operation authentication-data operation command execution script wake-up and re-execution is adopted; When the operation command is executed, the dynamic identity authentication module is activated and req...
Embodiment 2
[0032] like figure 2 As shown, a computer-based security authentication system includes:
[0033] The identity authentication module is used to complete the identification of the user's biometric identity and obtain the corresponding user identity authentication result;
[0034] Data segmentation grid, which is used to frame the data in the database in grids corresponding to different data operation permissions according to the results of user authentication; different data operation permissions include hidden, read-only, only transfer, only revision, and full authority ;
[0035] The data operation behavior recognition module is used to realize the recognition of user data operation behavior in the way of script recording + behavior recognition model real-time recognition. The operation behavior monitoring module is deployed on the computer in the form of a static jar package;
[0036] The dynamic identity recognition module is activated when a data operation command need...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com