Cloud key management method and system based on intelligent IC card security authentication
A key management system and security certification technology, which is applied in the cloud key management method and system field based on smart IC card security certification, can solve the problems of high requirements for the enterprise center network environment, high implementation cost, and long card production cycle , to achieve the effect of convenient expansion, high security, and low requirements
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
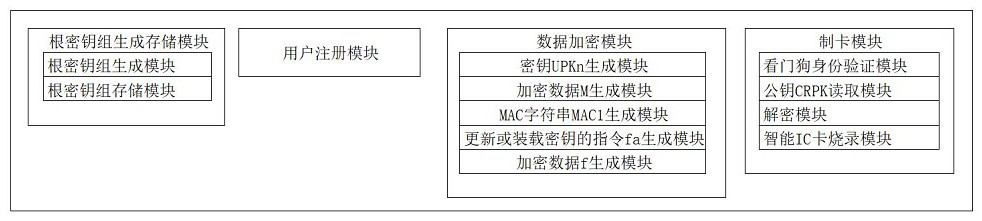
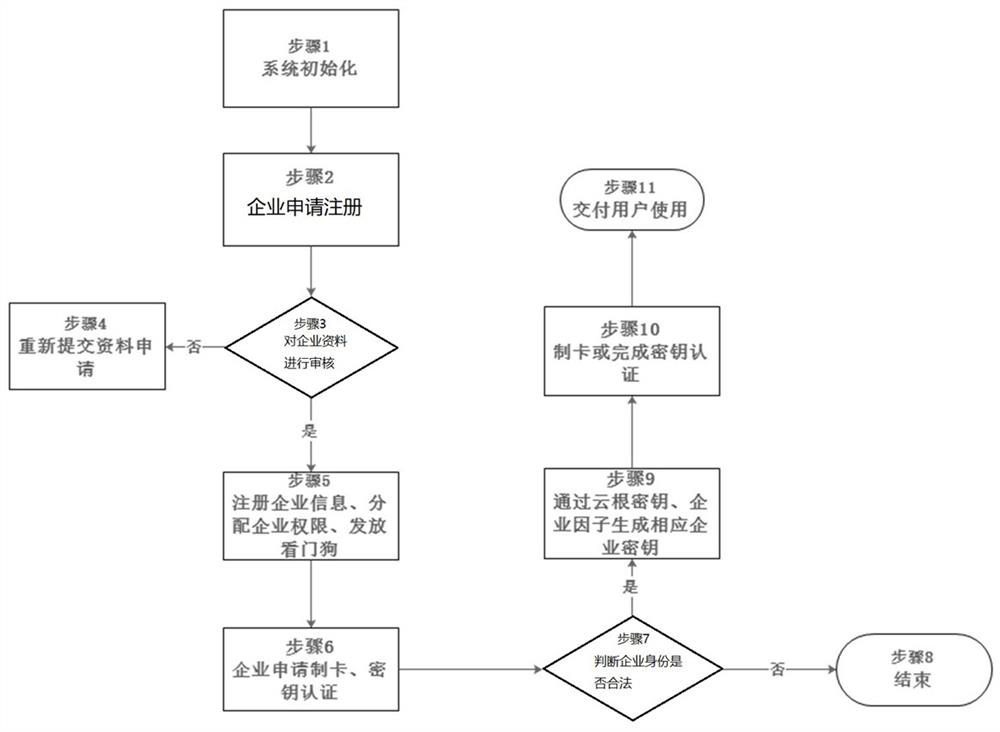
Image
Examples
Embodiment Construction
[0063] In order to enable those skilled in the art to better understand the technical solutions of the present invention, the present invention will be further described in detail below in conjunction with specific embodiments.
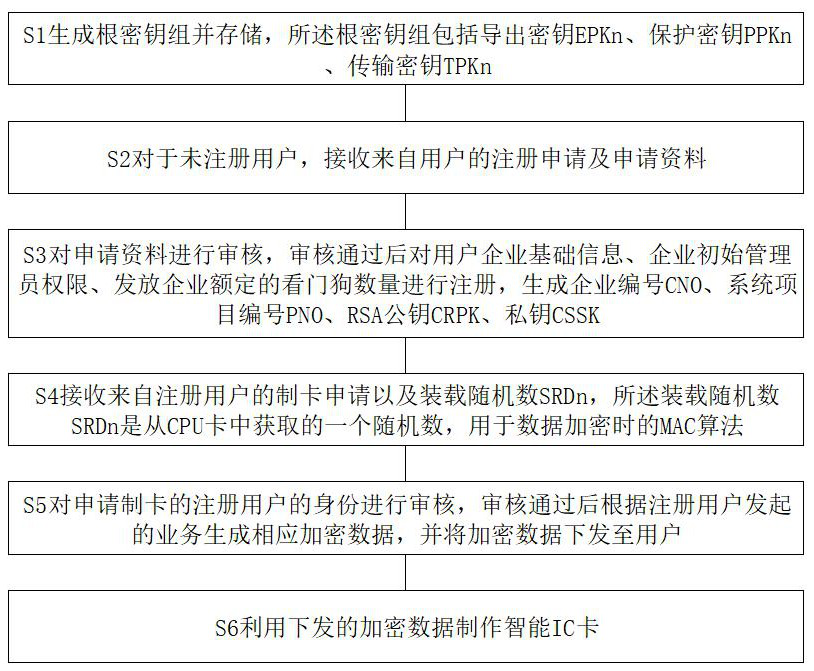
[0064] Such as figure 1 As shown, a kind of cloud key management method based on smart IC card security authentication of the present invention comprises:
[0065] S1 generates and stores a root key group, which includes an derived key EPKn, a protection key PPKn, and a transmission key TPKn.
[0066] S2 For an unregistered user, receive a registration application and application materials from the user.
[0067] S3 reviews the application materials, and after the review is passed, registers the user's company basic information, company initial administrator rights, and the number of watchdogs issued by the company, and generates the company number CNO, system project number PNO, RSA public key CRPK, and private key CSSK.
[0068] S4 receives the car...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com