Encrypted three-dimensional code generation and identification method and system
An identification method and three-dimensional code technology, which are applied in electromagnetic radiation induction, record carriers used by machines, instruments, etc., can solve the problems of confidentiality and easy reading of the content information of the code map, so as to achieve low encryption cost and increase data load. , The effect of high recognition efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
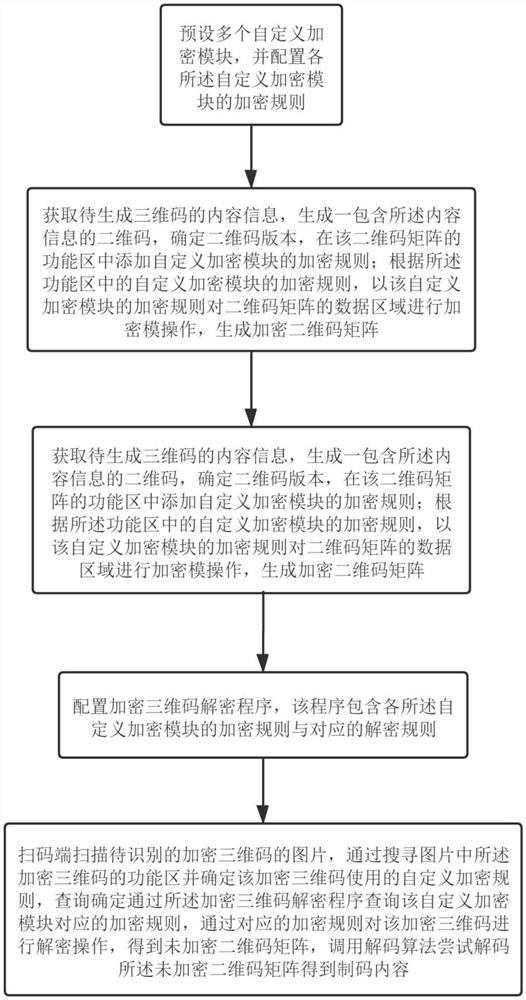
[0047] see figure 1 , this embodiment provides an encrypted three-dimensional code generation and identification method, which can be used for cross-network business card or communication information transmission, including the code generation step and the identification step;
[0048] The code generation steps are as follows:
[0049] A plurality of custom encryption modules are preset, and encryption rules of each of the custom encryption modules are configured. Can be encrypted with a custom mask.
[0050] Encrypt; generate three positioning modules and one calibration module, among which the three positioning modules present an isosceles right triangle; the ratio of the black and white part of the locator is 1:1:3:1:1, and the ratio of the black and white part of the calibration symbol is 1:1:1:1:1, generate a functional area, the custom encryption rules contained in the functional area can be user-defined mask information and version information, there are 40 versions, ...
Embodiment 2
[0061] see Figure 6 , this embodiment provides an encrypted three-dimensional code generation and recognition system, including a code generation module and a recognition module.
[0062] The code generation module includes a self-defined encryption unit, an encryption unit and a three-dimensional code generation unit.
[0063] The self-defined encryption unit is preset with a plurality of self-defined encryption modules, and is used to configure the encryption rules of each of the self-defined encryption modules.
[0064] The encryption unit is used to obtain the content information of the three-dimensional code to be generated, generate a two-dimensional code containing the content information, determine the two-dimensional code version, and add the encryption of the custom encryption module in the functional area of the two-dimensional code matrix Rules; according to the encryption rules of the self-defined encryption module in the functional area, the data area of th...
Embodiment 3
[0073] This embodiment provides an encrypted three-dimensional code generation and identification device, including a memory, a processor, and a computer program stored on the memory and operable on the processor. The method described in the examples.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com