Access traffic anomaly detection method and device based on LOF and isolated forest
An access traffic and anomaly detection technology, which is applied in the field of access traffic anomaly detection based on LOF and isolated forest, can solve the problems of random data distribution, prone to misjudgment, low computational complexity, etc., and achieves less model training time and meets real-time Requirements, low time complexity effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
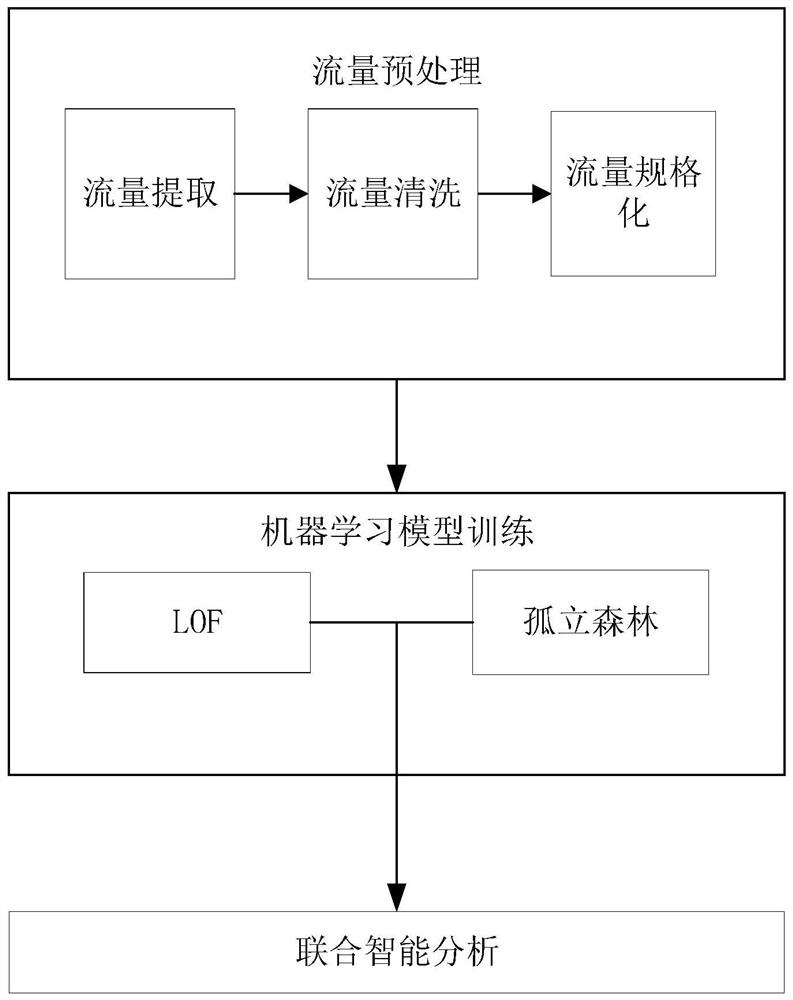
[0037]Nowadays, anomaly detection technology is widely used in network intrusion detection, fraud detection, crowd identification, etc., but it is rarely used in anomaly detection of unlabeled access traffic. This embodiment provides an access traffic anomaly detection method based on LOF and isolated forest, which uses the local outlier factor detection algorithm combined with the isolated forest to perform joint analysis, and performs anomaly detection on the collected access traffic categories to determine whether the traffic is abnormal and ensure System security. The access traffic anomaly detection method first preprocesses the access traffic data to obtain the traffic data set, uses LOF and isolation forest algorithms for model training, and finally tests according to the two trained models, and uses weighting factors for joint analysis .
[0038] Such as figure 1 As shown, the access traffic anomaly detection method includes:
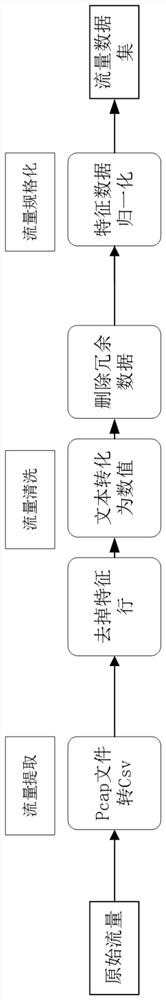
[0039] Step 1. Traffic preprocessing: ...
Embodiment 2
[0059] This embodiment is on the basis of embodiment 1:
[0060] This embodiment provides a computer device, including a memory and a processor. The memory stores a computer program. When the processor executes the computer program, the steps of the method for detecting abnormal access traffic based on LOF and isolated forests in Embodiment 1 are implemented. Among them, the computer program may be in the form of source code, object code, executable file or some intermediate form.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com