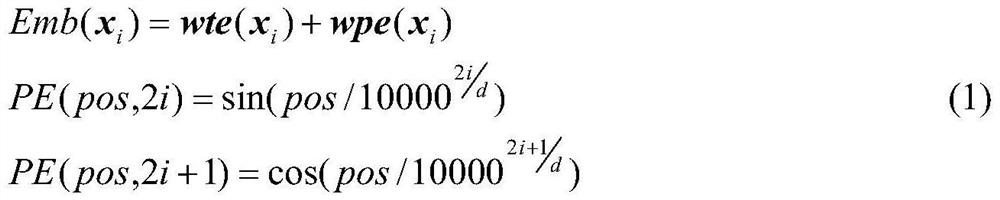Generative text covert communication method based on theme guidance
A covert communication, generative technology, applied in the field of secret data transmission, can solve the problems of high computational complexity and low information hiding efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
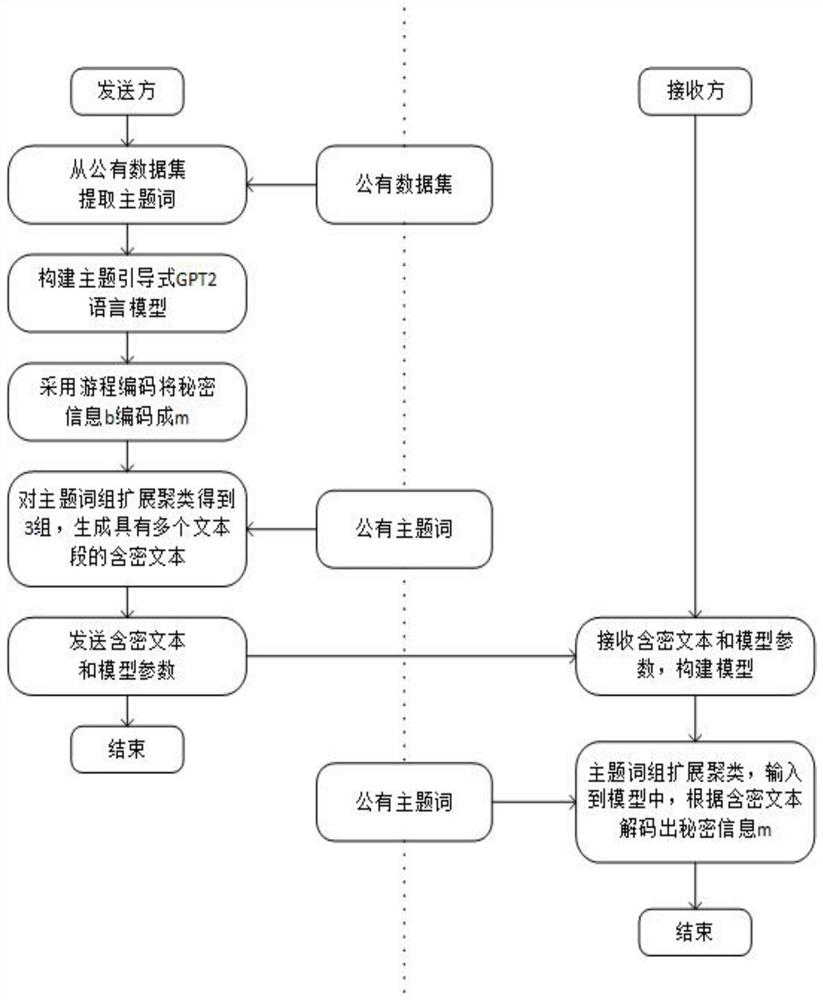
[0031] Such as figure 1 As shown, a topic-guided generative text covert communication method, the specific operation steps are as follows: Among them, the specific operation steps of the sender are as follows:
[0032] Step 1: extract the subject phrase of each text segment according to the public data set;
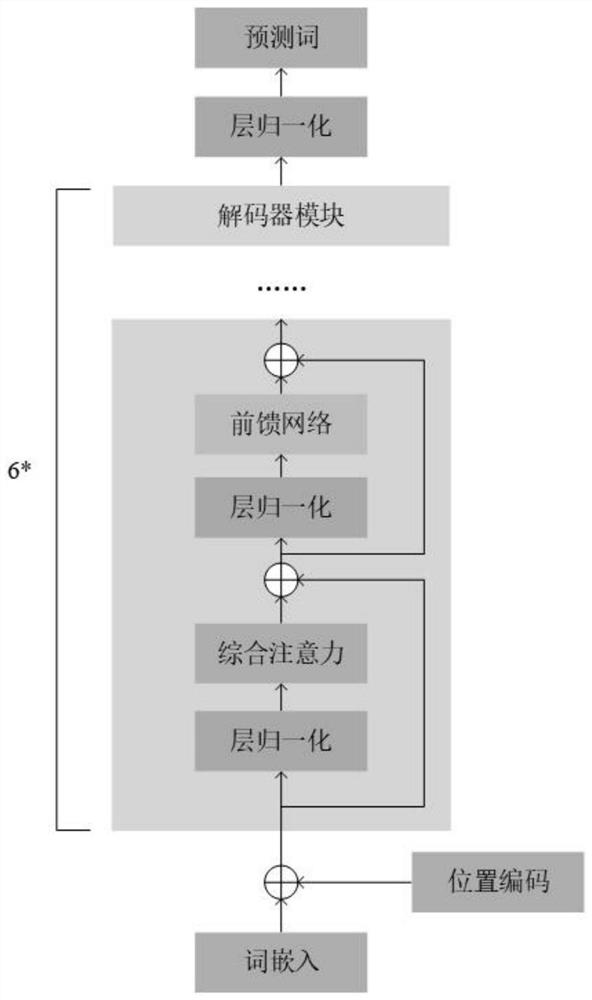
[0033] Step 2: According to figure 2 , build a language model, and use the subject phrase and data set obtained in step 1 to train the model;
[0034] Step 3: Use run-length coding to encode the secret information as m=N 0 0N 1 1...,N 0 ,N 1 ∈[1,9];
[0035] Step 4: Subject expansion and clustering of the public subject words to obtain three groups of subject phrases, generate three text segments according to the subject phrases, respectively encode "0", "1" and "0" and order of "1";
[0036] Step 5: The sender sends the generated ciphertext and model parameters to the receiver.
[0037] The specific operation steps of the receiver are as follows:
[0038] Step 1...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com